Topic 1: Exam Pool A
Which configuration enables a Cisco router lo send information to a TACACS+ server for individual EXEC commands associated with privilege level 15?
A. Router(config)# aaa accounting commands 15 default start-stop group tacacs+
B. Router(config)# aaa authorization exec default group tacacs+
C. Router(config)# aaa authorization commands 15 default group tacacs+
D. Router(config)# aaa accounting exec default start-stop group tacacs+
Which two mechanisms are used with OAuth 2.0 for enhanced validation? (Choose two.)
A. custom headers
B. authentication
C. authorization
D. request management
E. accounting
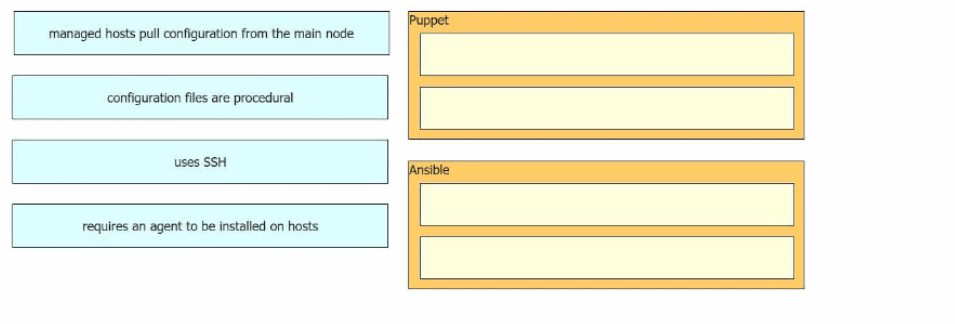
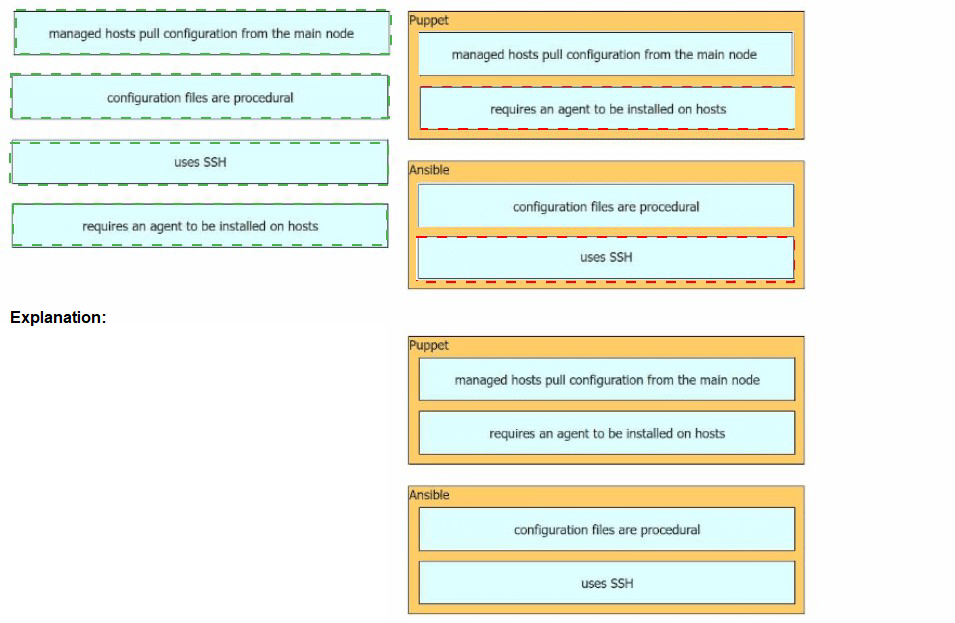
Drag and drop the characteristics from the left onto the corresponding orchestration tool on the right.
Which data is properly formatted with JSON?
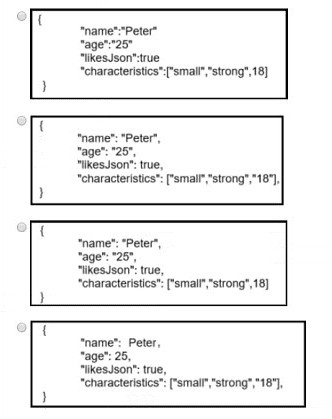
A. Option A
B. Option B
C. Option C
D. Option D
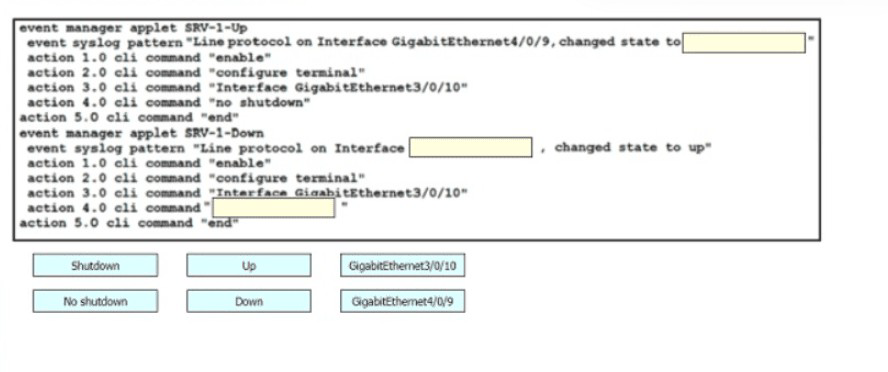
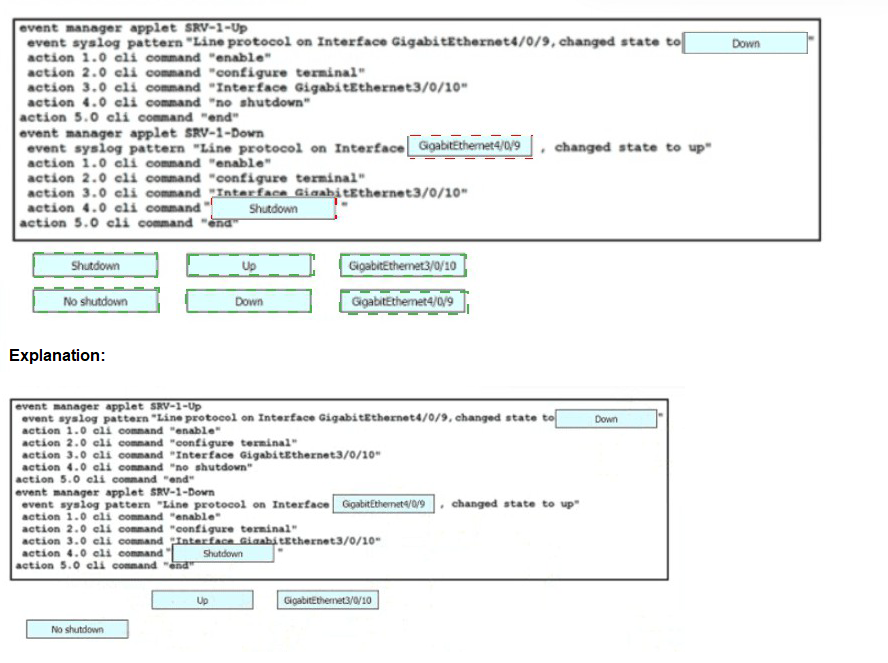
Drag and drop the snippets onto the blanks within the code to construct a script that brings up the failover Ethernet port if the primary port goes down and also shuts down the failover port when the primary returns to service. Not all options are used.
Which NGFW mode block flows crossing the firewall?
A. Passive
B. Tap
C. Inline tap
D. Inline
Which two methods are used to assign security group tags to the user in a Cisco Trust Sec architecture? (Choose two.)
A. modular QoS
B. policy routing
C. web authentication
D. DHCP
E. IEEE 802.1x
Which three methods does Cisco Catalyst Center (formerly DNA Center) use to discover devices? (Choose three.)
A. SNMP
B. a specified range of IP addresses
C. NETCONF
D. LLDP
E. ping
F. CDP
Which mobility role is assigned to a client in the client table of the new controller after a Layer 3 roam?
A. anchor
B. foreign
C. mobility
D. transparent
Which features does Cisco EDR use to provide threat detection and response protection?
A. containment, threat intelligence, and machine learning
B. firewalling and intrusion prevention
C. container-based agents
D. cloud analysts and endpoint firewall controls