Topic 1: Exam Pool A
What are two benefits of YANG? (Choose two.)
A.
It enforces the use of a specific encoding format for NETCONF.
B.
It collects statistical constraint analysis information.
C.
It enables multiple leaf statements to exist within a leaf list.
D.
It enforces configuration semantics.
E.
It enforces configuration constraints.
It enforces the use of a specific encoding format for NETCONF.
It enforces configuration constraints.
A server running Linux is providing support for virtual machines along with DNS and DHCP services for a small business. Which technology does this represent?
A.
container
B.
Type 1 hypervisor
C.
hardware pass-thru
D.
Type 2 hypervisor
Type 2 hypervisor
Explanation:
In contrast to type 1 hypervisor, a type 2 hypervisor (or hosted hypervisor) runs on top of an operating system and not the physical hardware directly. A big advantage of Type 2 hypervisors is that management console software is not required. Examples of type 2 hypervisor are VMware Workstation (which can run on Windows, Mac and Linux) or Microsoft Virtual PC (only runs on Windows).
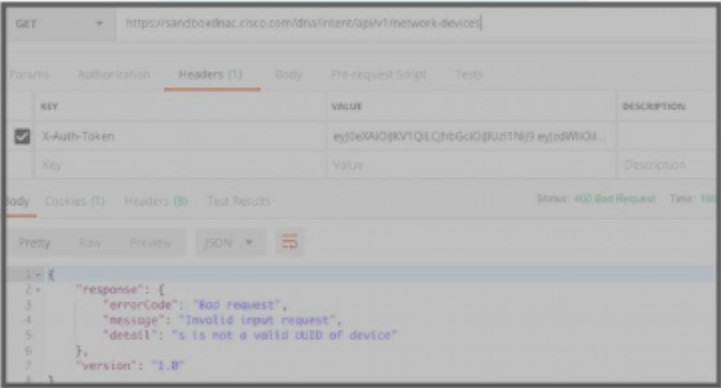
Refer to the exhibit. POSTMAN is showing an attempt to retrieve network device information from Cisco DNA Center API. What is the issue?
A.
The URI string is incorrect
B.
The token has expired
C.
Authentication has failed
D.
The JSON payload contains the incorrect UUID
The URI string is incorrect
Refer to the exhibit.
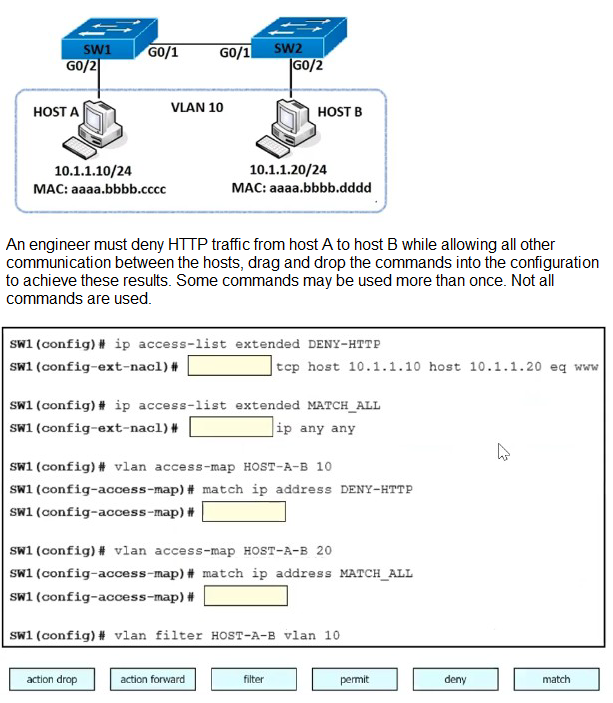
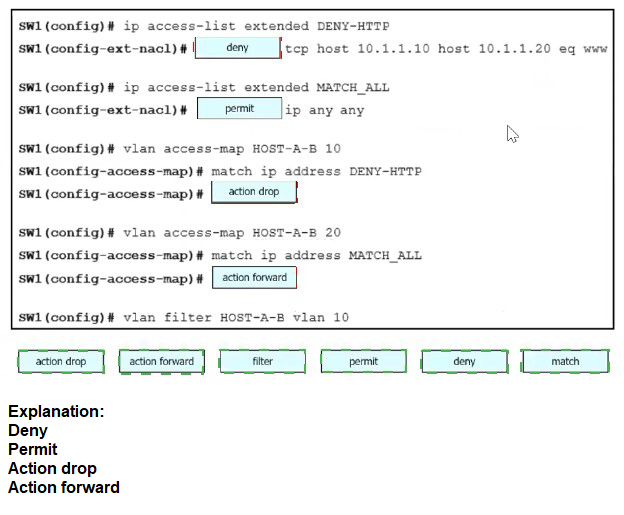
Refer to the exhibit.
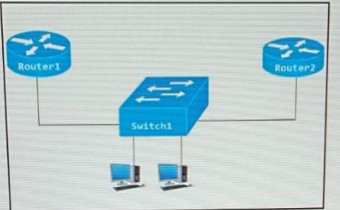
Router 1 is currently operating as the HSRP primary with a priority of 110 router1 fails and router2 take over the forwarding role. Which command on router1 causes it to take over the forwarding role when it return to service?
A.
standby 2 priority
B.
standby 2 preempt
C.
standby 2 track
D.
standby 2 timers
standby 2 preempt
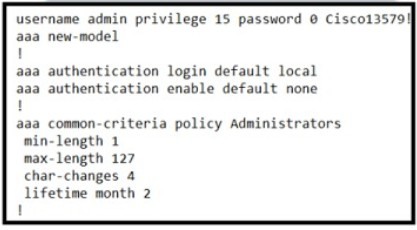
Refer to the exhibit. A network engineer must configure a password expiry mechanism on the gateway router for all local passwords to expire after 60 days. What is required to complete this task?
A.
The password expiry mechanism is on the AAA server and must be configured there.
B.
Add the aaa authentication enable default Administrators command.
C.
Add the username admin privilege 15 common-criteria*policy Administrators password 0 Cisco13579! command.
D.
No further action Is required. The configuration is complete.
Add the username admin privilege 15 common-criteria*policy Administrators password 0 Cisco13579! command.
Explanation: Perform this task to create a password security policy and to apply the policy to a specific user profile.
Device> enable
Device# configure terminal
Device(config)# aaa new-model
Device(config)# aaa common-criteria policy policy1
Device(config-cc-policy)# char-changes 4
Device(config-cc-policy)# max-length 20
Device(config-cc-policy)# min-length 6
Device(config-cc-policy)# numeric-count 2
Device(config-cc-policy)# special-case 2
Device(config-cc-policy)# exit
Device(config)# username user1 common-criteria-policy policy1 password password1
Device(config)# end
What is one difference between saltstack and ansible?
A.
SaltStack uses an API proxy agent to program Cisco boxes on agent mode, whereas Ansible uses a Telnet connection
B.
SaltStack uses the Ansible agent on the box, whereas Ansible uses a Telnet server on the box
C.
SaltStack is constructed with minion, whereas Ansible is constructed with YAML
D.
SaltStack uses SSH to interact with Cisco devices, whereas Ansible uses an event bus
SaltStack is constructed with minion, whereas Ansible is constructed with YAML
What is the differences between TCAM and the MAC address table?
A.
The MAC address table is contained in TCAM ACL and QoS information is stored in TCAM
B.
The MAC address table supports partial matches. TCAM requires an exact match
C.
Router prefix lookups happens in CAM. MAC address table lookups happen in TCAM
D.
TCAM is used to make Layer 2 forwarding decisions CAM is used to build routing tables
The MAC address table is contained in TCAM ACL and QoS information is stored in TCAM
Explanation: https://community.cisco.com/t5/networking-documents/cam-contentaddressable-memory-vs-tcam-ternary-content/ta-p/3107938
When using Ternary Content Addressable Memory (TCAM) inside routers it’s used for faster address lookup that enables fast routing.
In switches Content Addressable Memory (CAM) is used for building and lookup of mac address table that enables L2 forwarding decisions.
Besides Longest-Prefix Matching, TCAM in today’s routers and multilayer Switch devices are used to store ACL, QoS and other things from upper-layer processing.
What is a characteristic of YANG?
A.
It is a Cisco proprietary language that models NETCONF data
B.
It allows model developers to create custom data types
C.
It structures data in an object-oriented fashion to promote model reuse
D.
It provides loops and conditionals to control now within models
It structures data in an object-oriented fashion to promote model reuse
Refer to the exhibit.
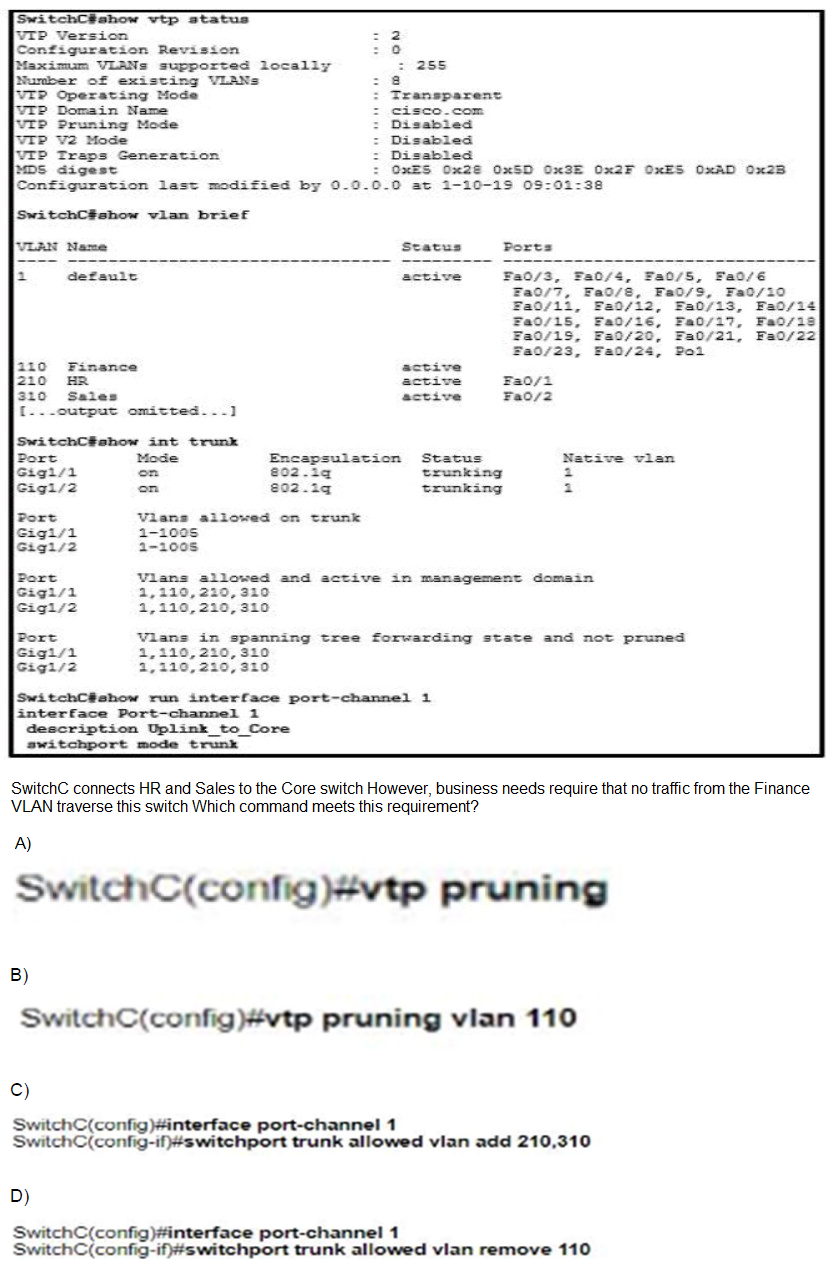
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
| Page 2 out of 84 Pages |
| Previous |