Topic 1: Exam Pool A
desc about topic
What is a characteristic of cloud-based network topology?
A. wireless connections provide the sole access method to services
B. onsite network services are provided with physical Layer 2 and Layer 3 components
C. services are provided by a public, private, or hybrid deployment
D. physical workstations are configured to share resources
Which device controls the forwarding of authentication requests for users when connecting to the network using a lightweight access point?
A. TACACS server
B. wireless access point
C. RADIUS server
D. wireless LAN controller
Refer to the exhibit.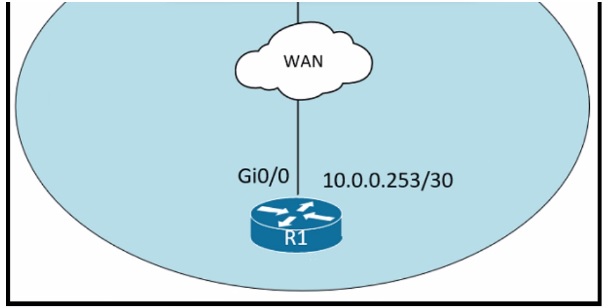
An administrator must turn off the Cisco Discovery Protocol on the port configured with address last usable address in the 10.0.0.0/30 subnet. Which command set meets the requirement?
A. interface gi0/1 no cdp enable
B. interface gi0/1 clear cdp table
C. interface gi0/0 no cdp advertise-v2
D. interface gi0/0 no cdp run
Several new coverage cells are required to improve the Wi-Fi network of an organization.Which two standard designs are recommended? (choose two.)
A. 5GHz provides increased network capacity with up to 23 nonoveriapping channels.
B. For maximum throughput, the WLC is configured to dynamically set adjacent access points to the same channel.
C. 5GHz channel selection requires an autonomous access point.
D. Adjacent cells with overlapping channels use a repeater access point.
E. Cells that overlap one another are configured to use nonoveriapping channels.
What is a difference between local AP mode and FiexConnet AP mode?
A. Local AP mode creates two CAPWAP tunnels per AP to the WLC
B. FiexConnect AP mode fails to function if the AP loses connectivity with the WLC
C. FlexConnect AP mode bridges the traffic from the AP to the WLC when local switching is configured
D. Local AP mode causes the AP to behave as if it were an autonomous AP
In software defined architectures, which plane is distributed and responsible for traffic forwarding?
A. management plane
B. control plane
C. policy plane
D. data plane
Refer to the exhibit.
Which password must an engineer use to enter the enable mode?
A. adminadmin123
B. default
C. testing 1234
D. cisco123
Explanation:
If neither the enable password command nor the enable secret command is configured, and if there is a line password configured for the console, the console line password serves as the enable password for all VTY sessions -> The “enable secret” will be used first if available, then “enable password” and line password.
What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
A. Filter traffic based on destination IP addressing
B. Sends the default route to the hosts on a network
C. ensures a loop-free physical topology
D. forwards multicast hello messages between routers
Explanation:
FHRP is layer 3 protocol whose purpose is to protect the default gateway by offering redundancy of the gateway in a subnet. This is achieved by allowing two or more routers to provide a backup for the first-hop IP router address. If a failure of an active router occurs, the backup router will take over the address. The routers negotiate their roles (Active/Standby) with each other by multicast hello messages to share the VIP (virtual IPaddress) between the FHRP routers. The terms Active/Standby vary between the different types of FHRP. The active router will act as the default gateway and the standby router
acts as a backup the active router
A port security violation has occurred on a switch port due to the maximum MAC address count being exceeded. Which command must be configured to increment the securityviolation count and forward an SNMP trap?
A. switchport port-security violation access
B. switchport port-security violation protect
C. switchport port-security violation restrict
D. switchport port-security violation shutdown
Explanation:
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4500/12-2/25ew/configuration/guide/conf/port_sec.html
What is the function of a controller in controller-based networking?
A. It serves as the centralized management point of an SDN architecture.
B. It centralizes the data plane for the network.
C. It is the card on a core router that maintains all routing decisions for a campus.
D. It is a pair of core routers that maintain all routing decisions for a campus