The firewall team has been asked to deploy a new Panorama server and to forward all firewall logs to this server By default, which component of the Palo Alto Networks firewall architect is responsible for log forwarding and should be checked for early signs of overutilization?
A. Management plane CPU
B. Dataplane CPU
C. Packet buffers
D. On-chip packet descriptors
A company has configured GlobalProtect to allow their users to work from home. A decrease in performance for remote workers has been reported during peak-use hours. Which two steps are likely to mitigate the issue? (Choose TWO)
A. Exclude video traffic
B. Enable decryption
C. Block traffic that is not work-related
D. Create a Tunnel Inspection policy
An administrator is configuring a Panorama device group. Which two objects are configurable? (Choose two.)
A. DNS Proxy
B. SSL/TLS profiles
C. address groups
D. URL Filtering profiles
An engineer is configuring a Protection profile to defend specific endpoints and resources
against malicious activity.
The profile is configured to provide granular defense against targeted flood attacks for
specific critical systems that are accessed by users from the internet.
Which profile is the engineer configuring?
A. Packet Buffer Protection
B. Zone Protection
C. Vulnerability Protection
D. DoS Protection
Explanation: The engineer is configuring a DoS Protection profile to defend specific endpoints and resources against malicious activity. A DoS Protection profile is a feature that enables the firewall to detect and prevent denial-of-service (DoS) attacks that attempt to overwhelm network resources or disrupt services. A DoS Protection profile can provide granular defense against targeted flood attacks for specific critical systems that are accessed by users from the internet, such as web servers, DNS servers, or VPN gateways. A DoS Protection profile can be applied to a security policy rule that matches the traffic to and from the protected systems, and can specify the thresholds and actions for different types of flood attacks, such as SYN, UDP, ICMP, or other IP floods12. References: DoS Protection, PCNSE Study Guide (page 58)
Review the information below. A firewall engineer creates a U-NAT rule to allow users in
the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as
expected?
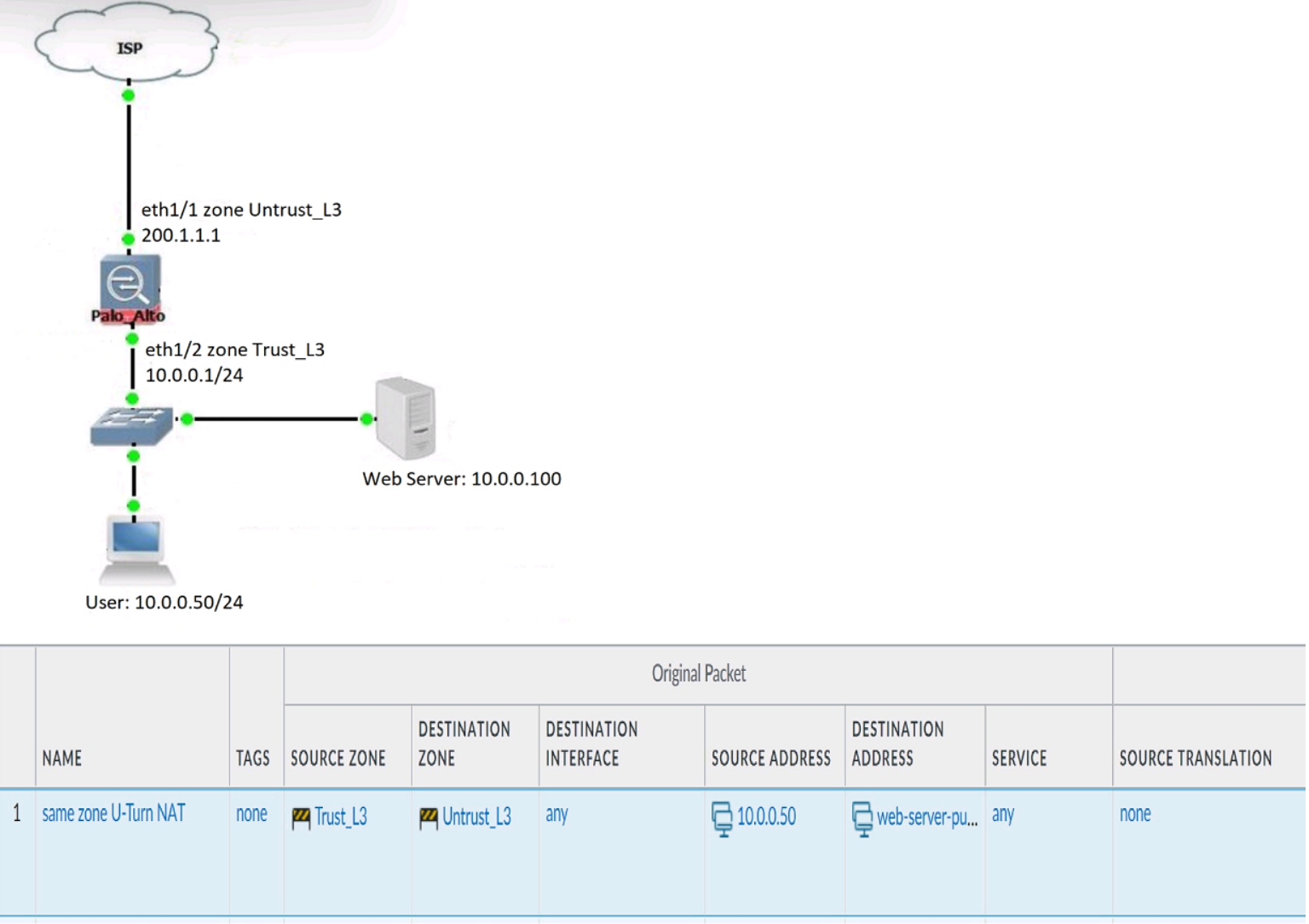
A. Change destination NAT zone to Trust_L3.
B. Change destination translation to Dynamic IP (with session distribution) using firewall ethI/2 address.
C. Change Source NAT zone to Untrust_L3.
D. Add source Translation to translate original source IP to the firewall eth1/2 interface translation.
A firewall engineer is configuring quality of service (OoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet. Which combination of pre-NAT and / or post-NAT information should be used in the QoS rule?
A. Post-NAT source IP address Pre-NAT source zone
B. Post-NAT source IP address Post-NAT source zone
C. Pre-NAT source IP address Post-NAT source zone
D. Pre-NAT source IP address Pre-NAT source zone
Explanation: When configuring Quality of Service (QoS) policies, particularly for traffic
going to or from specific IP addresses and involving NAT, it's important to base the rule on
how the firewall processes the traffic. For QoS, the firewall evaluates traffic using pre-NAT
IP addresses and zones because QoS policies typically need to be applied before the NAT
action occurs. This is especially true for inbound traffic, where the goal is to limit bandwidth
before the destination IP is translated.
The correct combination for a QoS rule in this scenario, where the aim is to limit bandwidth
for downloads from a specific server (implying inbound traffic to the server), would be:
D. Pre-NAT source IP address Pre-NAT source zone:
Pre-NAT source IP address: This refers to the original IP address of the client or
source device before any NAT rules are applied. Since QoS policies are evaluated
before NAT, using the pre-NAT IP address ensures that the policy applies to the
correct traffic.
Pre-NAT source zone: This is the zone associated with the source interface before
NAT takes place. Using the pre-NAT zone ensures that the QoS policy is applied
to traffic as it enters the firewall, before any translations or routing decisions are made.
By configuring the QoS rule with pre-NAT information, the firewall can accurately apply
bandwidth limitations to the intended traffic, ensuring efficient use of network resources and
mitigating the impact of large file downloads from the specified server.
For detailed guidelines on configuring QoS policies, refer to the Palo Alto Networks
documentation, which provides comprehensive instructions and best practices for
managing bandwidth and traffic priorities on the network.
A company configures its WildFire analysis profile to forward any file type to the WildFire public cloud. A company employee receives an email containing an unknown link that downloads a malicious Portable Executable (PE) file. What does Advanced WildFire do when the link is clicked?
A. Performs malicious content analysis on the linked page, but not the corresponding PE file.
B. Performs malicious content analysis on the linked page and the corresponding PE file.
C. Does not perform malicious content analysis on either the linked page or the corresponding PE file.
D. Does not perform malicious content analysis on the linked page, but performs it on the corresponding PE file.
Explanation: Advanced WildFire analyzes both the webpage linked by the URL and any
files (like PE files) that are downloaded as a result of clicking that link. This includes
checking the linked webpage for malicious content and sending any downloaded files for
further analysis to determine their behavior and potential malicious intent.
The PCNSA Study Guide outlines that WildFire inspects and analyzes both content
downloaded and webpages involved when integrated into the organization's security profile
. This dual-layered approach ensures comprehensive protection against threats from both
the webpage and its payloads.
Explanation: Advanced WildFire analyzes both the webpage linked by the URL and any
files (like PE files) that are downloaded as a result of clicking that link. This includes
checking the linked webpage for malicious content and sending any downloaded files for
further analysis to determine their behavior and potential malicious intent.
The PCNSA Study Guide outlines that WildFire inspects and analyzes both content
downloaded and webpages involved when integrated into the organization's security profile
. This dual-layered approach ensures comprehensive protection against threats from both
the webpage and its payloads.
Step-by-Step Explanation
Link Clicked and File Download Triggered:
URL Inspection by WildFire:
Forwarding the PE File for Analysis:
Dynamic and Static Analysis:
Threat Verdict:
Automated Response:
Signature Update:
Advanced WildFire Configuration and Behavior
Forwarding File Types:
The WildFire analysis profile must be configured to forward relevant file types. In this case:
PE files are commonly forwarded by default since they are a known vector for
malware.
Administrators can define custom forwarding rules based on file type and traffic.
Integration with the Security Profile:
WildFire integrates with other security profiles (e.g., Antivirus, Anti-Spyware, URL
Filtering).
URL Filtering ensures that the link itself is categorized and blocked if malicious.
WildFire's output informs and updates the threat prevention database dynamically.
Why the Answer is B?
WildFire performs dual analysis:
This layered analysis ensures robust protection against modern threats, which
often combine malicious webpages with harmful payloads.
Four configuration choices are listed, and each could be used to block access to a specific URL. If you configured each choice to block the same URL, then which choice would be evaluated last in the processing order to block access to the URL?
A. Custom URL category in URL Filtering profile
B. EDL in URL Filtering profile
C. PAN-DB URL category in URL Filtering profile
D. Custom URL category in Security policy rule
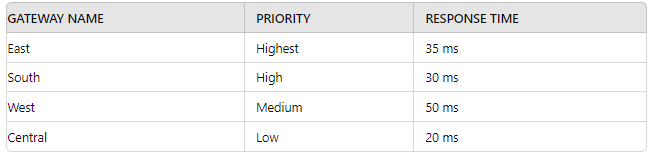
A security engineer has configured a GlobalProtect portal agent with four gateways Which
GlobalProtect Gateway will users connect to based on the chart provided?
A. South
B. West
C. East
D. Central
Explanation: Based on the provided table, the GlobalProtect portal agent configuration
includes four gateways with varying priorities and response times. Users will connect to the
gateway with the highest priority and, if multiple gateways share the same priority, the one
with the lowest response time.
Answer Determination
A network administrator notices a false-positive state after enabling Security profiles. When
the administrator checks the threat prevention logs, the related signature displays the
following:
threat type: spyware category: dns-c2 threat ID: 1000011111
Which set of steps should the administrator take to configure an exception for this
signature?
A. Navigate to Objects > Security Profiles > Anti-Spyware Select related profile Select DNS exceptions tabs Search related threat ID and click enable Commit
B. Navigate to Objects > Security Profiles > Vulnerability Protection Select related profile Select the signature exceptions tab and then click show all signatures Search related threat ID and click enable Change the default action Commit
C. Navigate to Objects > Security Profiles > Vulnerability Protection
Select related profile
Select the Exceptions lab and then click show all signatures
Search related threat ID and click enable
Commit
D. Navigate to Objects > Security Profiles > Anti-Spyware
Select related profile
Select the Exceptions lab and then click show all signatures
Search related threat ID and click enable Commit
Explanation: When dealing with a false positive, particularly for a spyware threat detected
through DNS queries (as indicated by the category "dns-c2"), the correct course of action
involves creating an exception in the Anti-Spyware profile, not the Vulnerability Protection
profile. This is because the Anti-Spyware profile in Palo Alto Networks firewalls is designed
to detect and block spyware threats, which can include command and control (C2) activities
often signaled by DNS queries.
The steps to configure an exception for this specific spyware signature (threat ID:
1000011111) are as follows:
Navigate to Objects > Security Profiles > Anti-Spyware. This is where all the Anti-
Spyware profiles are listed.
Select the related Anti-Spyware profile that is currently applied to the security
policy which is generating the false positive.
Within the profile, go to the DNS Exceptions tab. This tab allows you to specify
exceptions based on DNS signatures.
Search for the related threat ID (in this case, 1000011111) and click enable to
create an exception for it. By doing this, you instruct the firewall to bypass the
detection for this specific signature, effectively treating it as a false positive.
Commit the changes to make the exception active.
By following these steps, the administrator can effectively address the false positive without
disabling the overall spyware protection capabilities of the firewall.
| Page 9 out of 33 Pages |
| Previous |