Topic 5, Misc. Questions
You have a Microsoft 365 tenant.
Company policy requires that all Windows 10 devices meet the following minimum requirements:
Require complex passwords.
Require the encryption of data storage devices.
Have Microsoft Defender Antivirus real-time protection enabled.
You need to prevent devices that do not meet the requirements from accessing resources in the tenant.
Which two components should you create? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A.
a configuration policy
B.
a compliance policy
C.
a security baseline profile
D.
a conditional access policy
E.
a configuration profile
a compliance policy
a conditional access policy
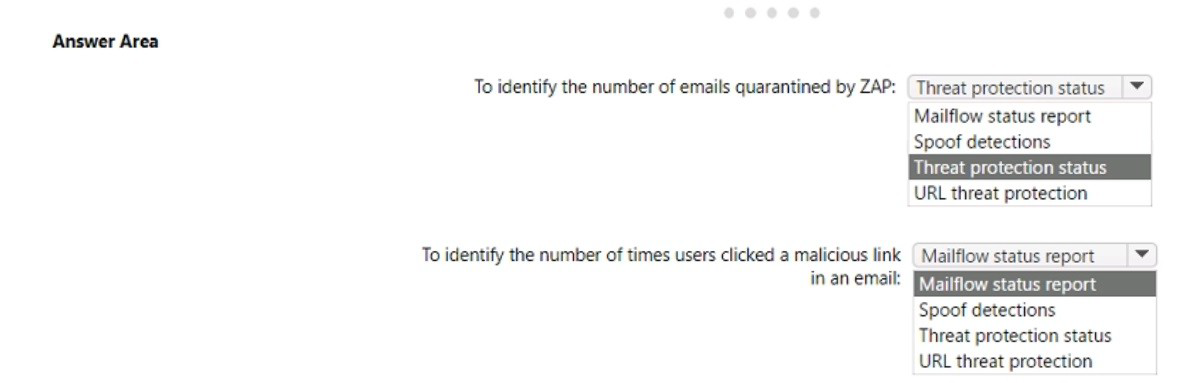
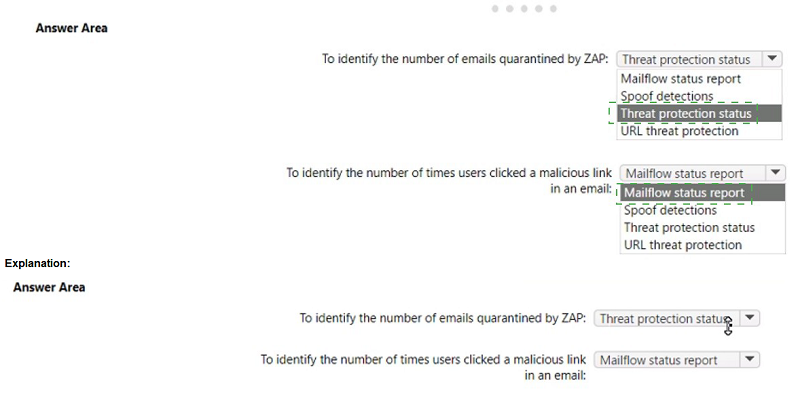
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Office 365.
The subscription has the default inbound anti-spam policy and a custom Safe Attachments policy.
You need to identify the following information:
• The number of email messages quarantined by zero-hour auto purge (ZAP)
• The number of times users clicked a malicious link in an email message
Which Email & collaboration report should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You plan to implement Microsoft Purview policies to meet the following requirements:
Identify documents that are stored in Microsoft Teams and SharePoint that contain Personally Identifiable Information (PII).
Report on shared documents that contain PII.
What should you create?
A.
a data loss prevention (DLP) policy
B.
a retention policy
C.
an alert policy
D.
a Microsoft Defender for Cloud Apps policy
a data loss prevention (DLP) policy
Explanation:
Demonstrate data protection
Protection of personal information in Microsoft 365 includes using data loss prevention (DLP) capabilities. With DLP policies, you can automatically protect sensitive information across Microsoft 365.
There are multiple ways you can apply the protection. Educating and raising awareness to where EU resident data is stored in your environment and how your employees are permitted to handle it represents one level of information protection using Office 365 DLP. In this phase, you create a new DLP policy and demonstrate how it gets applied to the IBANs.docx file you stored in SharePoint Online in Phase 2 and when you attempt to send an email containing IBANs.
From the Security & Compliance tab of your browser, click Home.
Click Data loss prevention > Policy.
Click + Create a policy.
In Start with a template or create a custom policy, click Custom > Custom policy > Next.
In Name your policy, provide the following details and then click Next: a. Name:
EU Citizen PII Policy b. Description: Protect the personally identifiable information of European citizens Etc.
Reference:
https://learn.microsoft.com/en-us/compliance/regulatory/gdpr-discovery-protectionreporting-in-office365-dev-test-environment
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains 1,000 Windows 10 devices.
You perform a proof of concept (PoC) deployment of Microsoft Defender for Endpoint for 10 test devices. During the onboarding process, you configure Microsoft Defender for Endpoint-related data to be stored in the United States.
You plan to onboard all the devices to Microsoft Defender for Endpoint.
You need to store the Microsoft Defender for Endpoint data in Europe.
What should you do first?
A.
Delete the workspace.
B.
Create a workspace.
C.
Onboard a new device.
D.
Offboard the test devices.
Create a workspace.
Explanation:
Storage locations
Understand where Defender for Cloud stores data and how you can work with your data:
* Machine information
- Stored in a Log Analytics workspace.
- You can use either the default Defender for Cloud workspace or a custom workspace.
Data is stored in accordance with the workspace location.
Reference:
https://learn.microsoft.com/en-us/azure/defender-for-cloud/plan-defender-for-servers-dataworkspace
You have a Microsoft 365 tenant that contains a Windows 10 device named Device1 and the Microsoft Endpoint Manager policies shown in the following table.

A.
only the settings of Policy!
B.
only the settings of Policy2
C.
only the settings of Policy3
D.
no settings
only the settings of Policy3
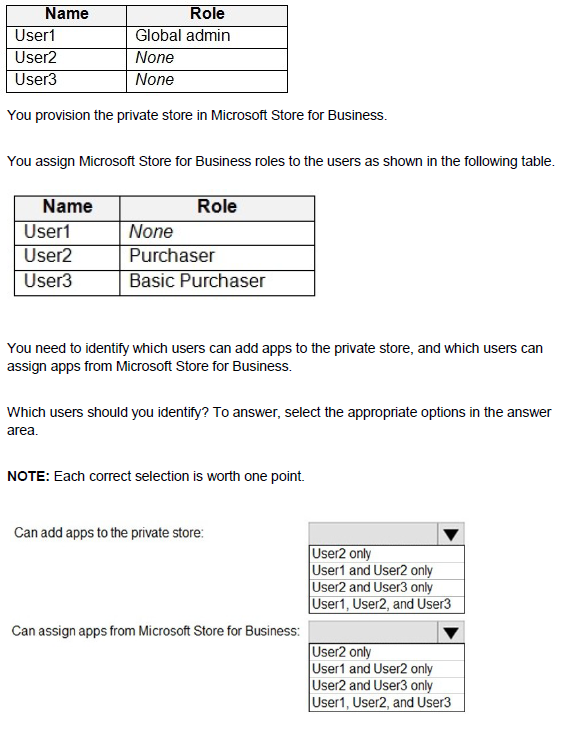
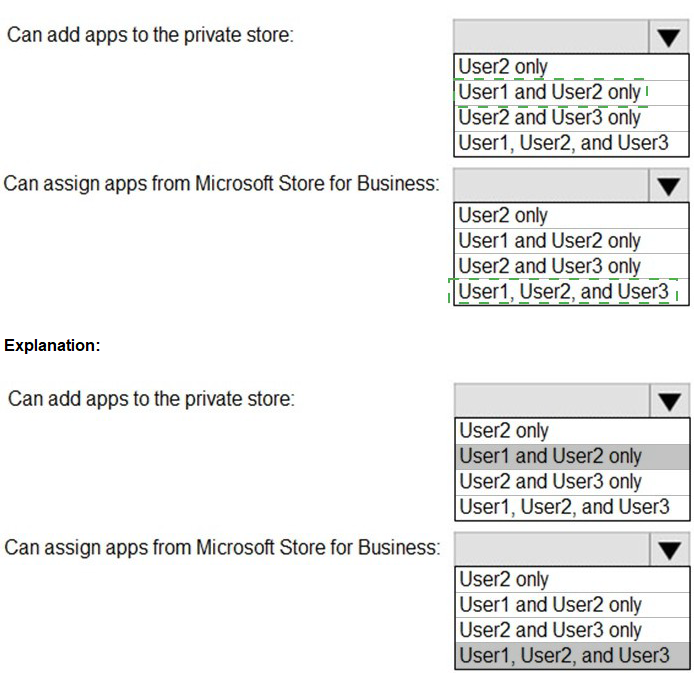
You have a Microsoft 365 E5 tenant that contains the users shown in the following table.
You have a Microsoft 365 subscription that links to an Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
A user named User1 stores documents in Microsoft OneDrive.
You need to place the contents of User1’s OneDrive account on an eDiscovery hold.
Which URL should you use for the eDiscovery hold? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
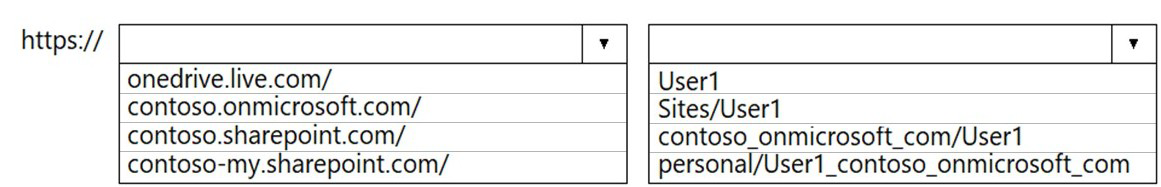
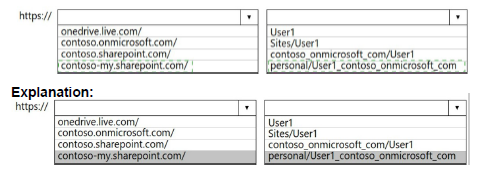
You have a Microsoft Azure Active Directory (Azure AD) tenant named Contoso.com.
You create a Microsoft Defender for identity instance Contoso.
The tenant contains the users shown in the following table.
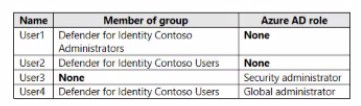
You need to modify the configuration of the Defender for identify sensors.
Solutions: You instruct User3 to modify the Defender for identity sensor configuration.
Does this meet the goal?
A.
Yes
B.
No
Yes
You have a Microsoft 365 E5 tenant that contains a user named User1.
You plan to implement insider risk management.
You need to ensure that User1 can perform the following tasks:
Review alerts.
Manage cases.
Create notice templates.
Review user emails by using Content explorer.
The solution must use the principle of least privilege.
To which role group should you add User1?
A.
Insider Risk Management
B.
Insider Risk Management Analysts
C.
Insider Risk Management Investigators
D.
Insider Risk Management Admin
Insider Risk Management Investigators
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the users shown in the following table.
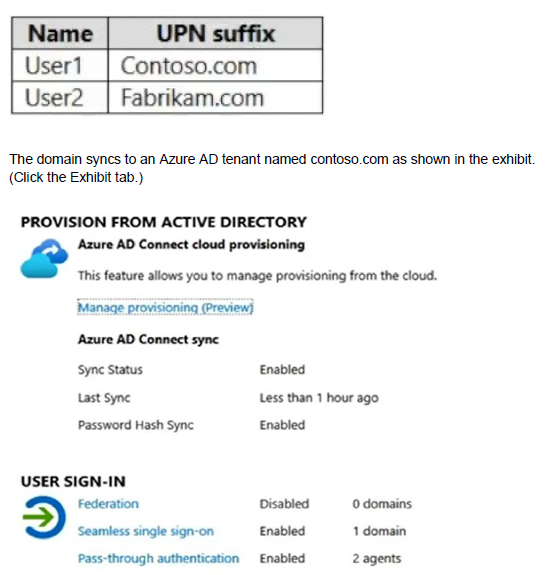
User2 fails to authenticate to Azure AD when signing in as user2@fabrikam.com.
You need to ensure that User2 can access the resources in Azure AD.
Solution: From the Microsoft Entra admin center, you add fabrikam.com as a custom domain. You instruct User2 to sign in as user2@fabrikam.com.
Does this meet the goal?
A.
Yes
B.
No
Yes
Explanation:
The on-premises Active Directory domain is named contoso.com. To enable users to sign on using a different UPN (different domain), you need to add the domain to Microsoft 365 as a custom domain.
| Page 7 out of 31 Pages |
| Previous |