Topic 5, Misc. Questions
You have a Microsoft 365 E5 subscription that contains 200 Android devices enrolled in Microsoft Intune.
You create an Android app protection policy named Policy! that is targeted to all Microsoft apps and assigned to all users.
Policy! has the Data protection settings shown in the following exhibit.
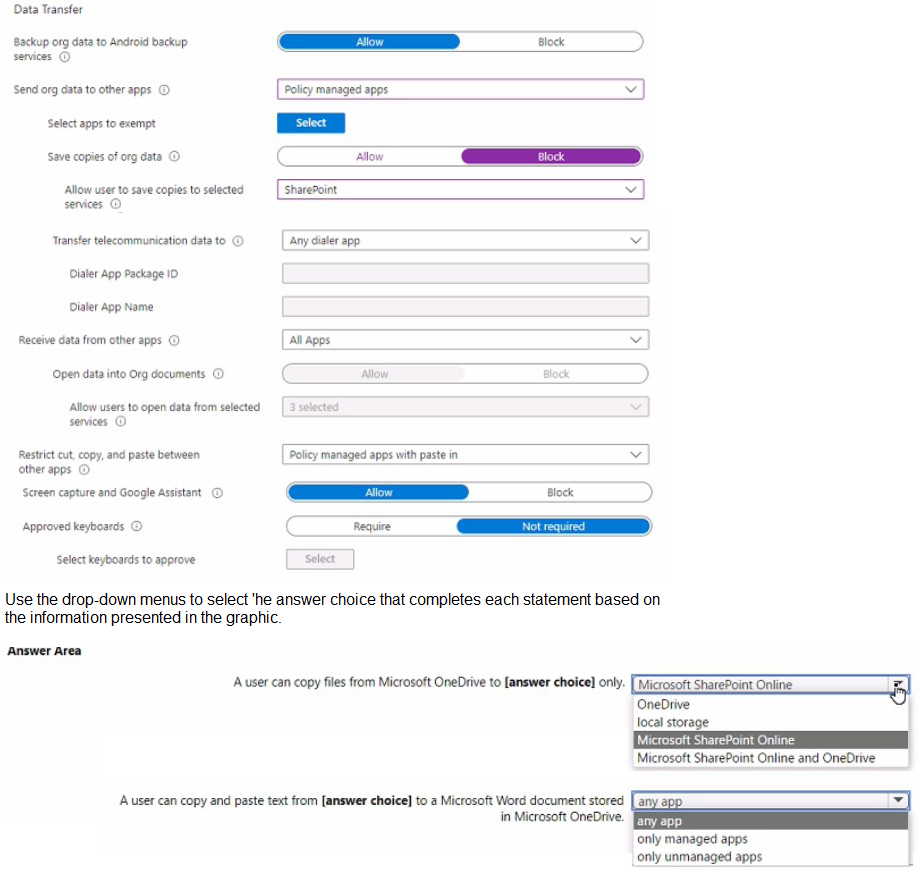
You have the sensitivity labels shown in the following exhibit.
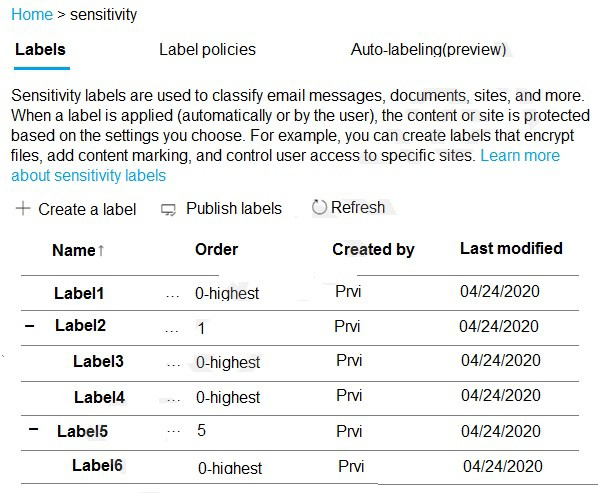
Which labels can users apply to content?
A.
Label3, Label4, and Label6 only
B.
Label1, Label2. Label3. Label4. Label5. and Label6
C.
Label1, Label2, and Label5 only
D.
Label1, Label3, Label4, and Label6 only
Label1, Label3, Label4, and Label6 only
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it As a result, these questions will not appear in the review screen. Your network contains an on-premises Active Directory domain. The domain contains domain controllers that run Windows Server 2019. The functional level of the forest and the domain is Windows Server 2012 R2.
The domain contains 100 computers that run Windows 10 and a member server named Server1 that runs Windows Server 2012 R2. You plan to use Server1 to manage the domain and to configure Windows 10 Group Policy settings.
You install the Group Policy Management Console (GPMC) on Server1.
You need to configure the Windows Update for Business Group Policy settings on Server1.
Solution: You raise the domain functional level to Windows Server 2019. You copy the Group Policy Administrative Templates from a Windows 10 computer to the Netlogon share on all the domain controllers.
Does this meet the goal?
A.
Yes
B.
No
No
You have an Azure subscription and an on-premises Active Directory domain. The domain contains 50 computers that run Windows 10.
You need to centrally monitor System log events from the computers.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

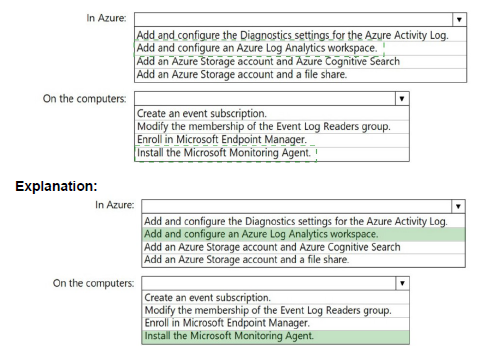
You have a hybrid Azure Active Directory (Azure AD) tenant and a Microsoft Endpoint Configuration Manager deployment. You have the devices shown in the following table.
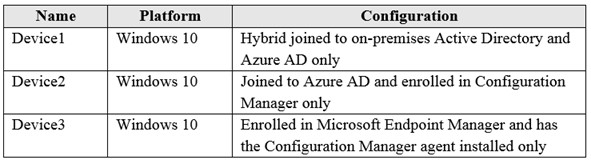
You plan to enable co-management. You need to identify which devices support co-management without requiring the installation of additional software. Which devices should you identify?
A.
Device1 only
B.
Device2 only
C.
Device3 only
D.
Device2 and Device3 only
E.
Device1, Device2, and Device3
Device2 and Device3 only
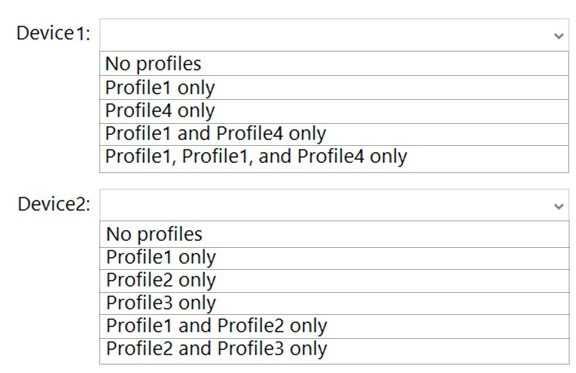
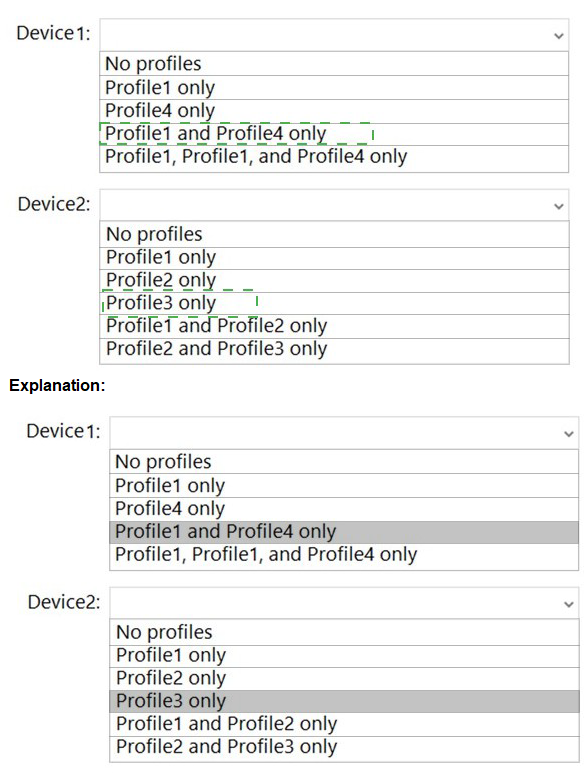
You have a Microsoft 365 E5 subscription that uses Microsoft Intune.
You have devices enrolled in Intune as shown in the following table.
You create the device configuration profiles shown in the following table.
Which profiles will be applied to each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.

You plan to publish a sensitivity label named Label1.
To which groups can you publish Label1?
A.
Group1 only
B.
Group1 and Group2 only
C.
Group1 and Group4 only
D.
Group1, Group2, and Group3 only
E.
Group1 Group2, Group3, and Group4
Group1 only
In addition to using sensitivity labels to protect documents and emails, you can also use sensitivity labels to protect content in the following containers: Microsoft Teams sites, Microsoft 365 groups (formerly Office 365 groups), and SharePoint sites.
Reference:
https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-teamsgroups-sites
You have a Microsoft 365 E5 subscription.
You need to identify which users accessed Microsoft Office 365 from anonymous IP addresses during the last seven days.
What should you do?
A.
From the Cloud App Security admin center, select Users and accounts
B.
From the Microsoft 365 security center, view the Threat tracker.
C.
From the Microsoft 365 admin center, view the Security & compliance report.
D.
From the Azure Active Directory admin center, view the Risky sign-ins report.
From the Cloud App Security admin center, select Users and accounts
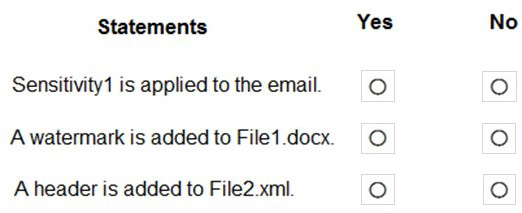
You have a Microsoft 365 E5 tenant.
You have a sensitivity label configured as shown in the Sensitivity label exhibit. (Click the Sensitivity label tab.)
You have an auto-labeling policy as shown in the Auto-labeling policy exhibit. (Click the Auto-labeling policy tab.)
A user sends an email that contains the components shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
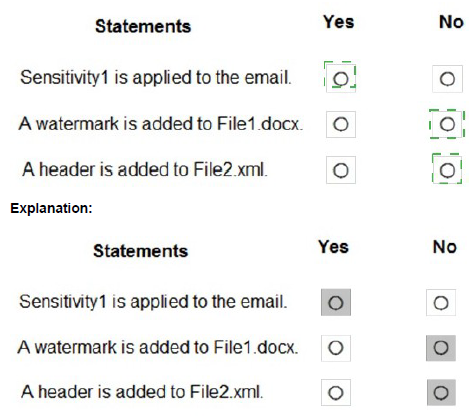
You have a new Microsoft 365 E5 tenant.
Enable Security defaults is set to Yes.
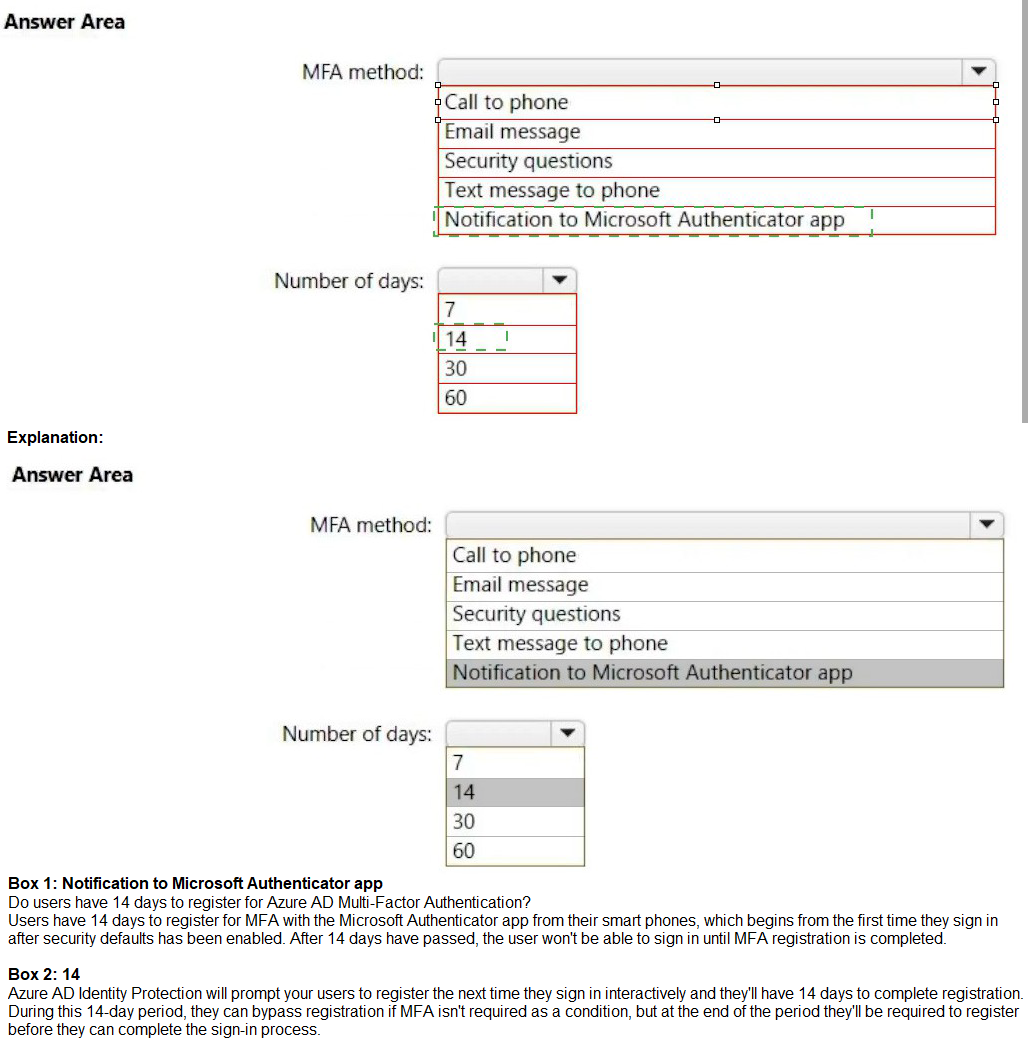
A user signs in to the tenant for the first time.
Which multi-factor authentication (MFA) method can the user use, and how many days does the user have to register for MFA? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
| Page 5 out of 31 Pages |
| Previous |