An administrator wants to implement bandwidth limits to restrict employee access to highrisk
web sites. On the Mobility Master (MM), where would the administrator define these
limits?
A.
802.1X policy
B.
User role
C.
Firewall policy
D.
AAA policy
User role
Refer to the exhibit.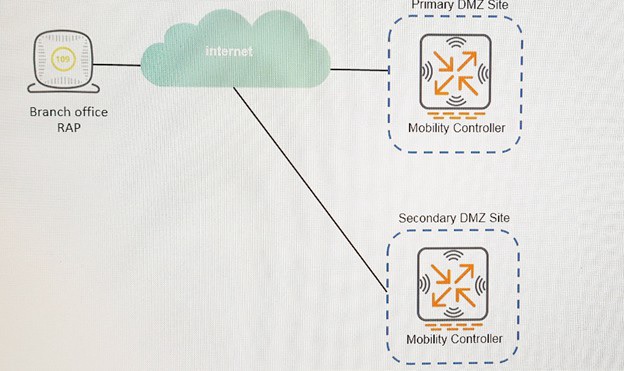
An administrator supports a RAP at a branch office shown in the exhibit. The company has
one Mobility Controller (MC) at the Primary DMZ site and one at the Secondary DMZ site.
The RAP is configured to connect to only the MC at the Primary DMZ site. A network
outage with the ISP at the Primary DMZ site causes the RAP to reboot. Upon reboot, the
RAP cannot build a tunnel to the Secondary DMZ site MC because the administrator forgot
to add the Second LMS IP address to the AP Group configuration. Once the RAP can
successfully connect, the administrator can add the Secondary DMZ MC as a backup LMS
to fix the AP Group.
What should the administrator implement to allow the RAP to connect to the MC at the
Secondary DMZ site while the outage at the primary site persists?
A.
Dynamic discovery through DHCP Option 43
B.
Static configuration from apboot mode
C.
Dynamic discovery through DHCP Option 60
D.
Dynamic discovery through multicast ADP
Static configuration from apboot mode
An administrator implements the Aruba AitGroup feature to accommodate the Apple
Bonjour service. In this implementation, which protocol advertises devices such as printers,
computers, and their services?
A.
LLDP
B.
Multicast DHCP
C.
Multicast DNS
D.
Broadcast DNS
Multicast DNS
In a VPN that uses certificate-based authentication, which component must be configured
on the Mobility Master (MM) to allow a RAP to successfully connect to a Mobility Controller
(MC)?
A.
RAP VPN username and password
B.
WLAN and new RAP group
C.
RAP IPSec pre-shared key
D.
RAP whitelist
RAP whitelist
An administrator wants to implement 802.1X authentication on Ethernet ports on branch
office controllers. What must the administrator do to implement this policy?
A.
Define the port an untrusted, and assign an AAA policy to the port.
B.
Define the port as trusted, and assign an AAA policy to the port.
C.
Define the port as untrusted, and assign an AAA policy to the VLAN.
D.
Define the port as trusted, and assign an AAA policy to the VLAN.
Define the port an untrusted, and assign an AAA policy to the port.
Which forwarding mode is used for a WLAN if a RAP needs to decrypt all user traffic and
forward it locally?
A.
Split-tunnel
B.
Bridge
C.
Tunnel
D.
Decrypt-tunnel
Bridge
An administrator creates service-based policies for AirGroup on the Mobility Master (MM).
The administrator can define location-based policy limits based on which information?
A.
AP names, AP groups, controller names, and controller groups
B.
AP Fully Qualified Location Names (FQLNs) and controller Fully Qualified Domain Names (FQDNs)
C.
AP names, AP groups, and AP Fully Qualified Location Names (FQLNs)
AP names, AP groups, and AP Fully Qualified Location Names (FQLNs)
Refer to the exhibit.
A user uses Microsoft Windows for a wireless session. Based on the output shown in the
exhibit for the selected Aruba AP, what is the possible problem with this user’s wireless
session?
A.
The AP has reached the limit for number of users that are allowed to connect to the radio.
B.
The controller cannot reach the AAA server to perform the authentication.
C.
The user is configured for PEAP, but the WLAN profile on the controller implemented EAP-TLS.
D.
The user misconfigured the Managed Network Settings profile in Windows
The user is configured for PEAP, but the WLAN profile on the controller implemented EAP-TLS.
Refer to the exhibit.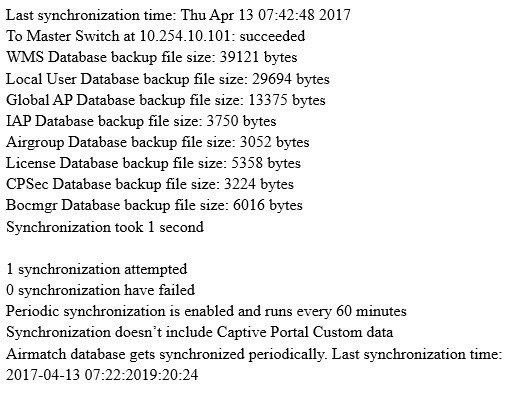
What can be determined from the command output shown in the exhibit?
A.
The synchronized data is protected by VRRP.
B.
The command was executed on the standby Mobility Master (MM).
C.
The synchronization period is at its default value.
D.
The other Mobility Master (MM) is the active license server
The synchronization period is at its default value.
An administrator supports an Aruba wireless solution that uses ClearPass to implement
server role assignment. A user reports that they are not able to access the correct
department resources. The administrator determines from the connected controller that the
user is associated to the login user profile instead of the department user profile.
What should the administrator examine on the ClearPass server to determine the Aruba
VSA User Role value that ClearPass returns to the controller?
A.
Accounting
B.
Event Viewer
C.
Audit Viewer
D.
Access Tracker
Access Tracker
| Page 4 out of 17 Pages |
| Previous |