Topic 3, Mix Questions
You have an Azure Synapse Analytics dedicated SQL pool.
You need to ensure that data in the pool is encrypted at rest. The solution must NOT
require modifying applications that query the data.
What should you do?
A.
Enable encryption at rest for the Azure Data Lake Storage Gen2 account.
B.
Enable Transparent Data Encryption (TDE) for the pool.
C.
Use a customer-managed key to enable double encryption for the Azure Synapse workspace.
D.
Create an Azure key vault in the Azure subscription grant access to the pool.
Enable Transparent Data Encryption (TDE) for the pool.
Explanation:
Transparent Data Encryption (TDE) helps protect against the threat of malicious activity by
encrypting and decrypting your data at rest. When you encrypt your database, associated
backups and transaction log files are encrypted without requiring any changes to your
applications. TDE encrypts the storage of an entire database
by using a symmetric key called the database encryption key.
Reference:
https://docs.microsoft.com/en-us/azure/synapse-analytics/sql-data-warehouse/sql-datawarehouse-
overviewmanage-security
You have files and folders in Azure Data Lake Storage Gen2 for an Azure Synapse workspace as shown in the following exhibit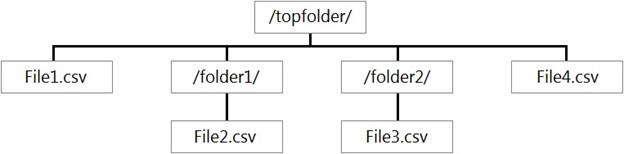
You create an external table named ExtTable that has LOCATION='/topfolder/'.
When you query ExtTable by using an Azure Synapse Analytics serverless SQL pool,
which files are returned?
A.
File2.csv and File3.csv only
B.
File1.csv and File4.csv only
C.
File1.csv, File2.csv, File3.csv, and File4.csv
D.
File1.csv only
File1.csv, File2.csv, File3.csv, and File4.csv
Explanation:
To run a T-SQL query over a set of files within a folder or set of folders while treating them
as a single entity or
rowset, provide a path to a folder or a pattern (using wildcards) over a set of files or folders.
Reference:
https://docs.microsoft.com/en-us/azure/synapse-analytics/sql/query-data-storage#querymultiple-
files-or-folders
You have an Azure subscription that contains the following resources:
* An Azure Active Directory (Azure AD) tenant that contains a security group named
Group1.
* An Azure Synapse Analytics SQL pool named Pool1.
You need to control the access of Group1 to specific columns and rows in a table in Pool1
Which Transact-SQL commands should you use? To answer, select the appropriate
options in the answer area.
NOTE: Each appropriate options in the answer area.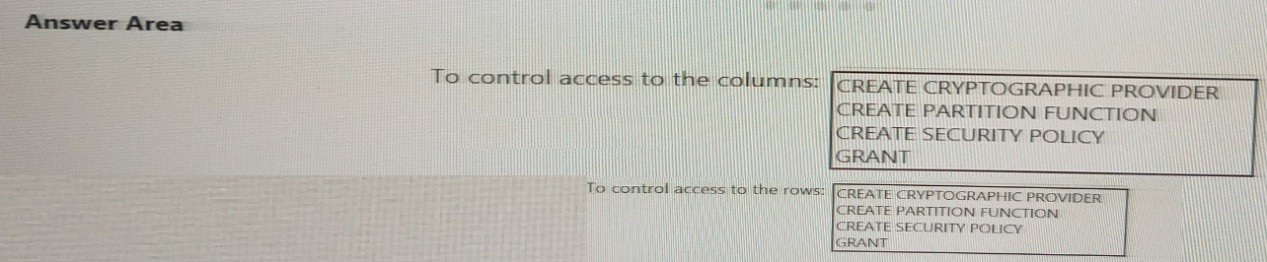
You are designing a dimension table for a data warehouse. The table will track the value of
the dimension attributes over time and preserve the history of the data by adding new rows
as the data changes.
Which type of slowly changing dimension (SCD) should use?
A.
Type 0
B.
Type 1
C.
Type 2
D.
Type 3
Type 2
Explanation: Type 2 - Creating a new additional record. In this methodology all history of
dimension changes is kept in the database. You capture attribute change by adding a new
row with a new surrogate key to the dimension table. Both the prior and new rows contain
as attributes the natural key(or other durable identifier). Also 'effective date' and 'current
indicator' columns are used in this method. There could be only one record with current
indicator set to 'Y'. For 'effective date' columns, i.e. start_date and end_date, the end_date
for current record usually is set to value 9999-12-31. Introducing changes to the
dimensional model in type 2 could be very expensive database operation so it is not
recommended to use it in dimensions where a new attribute could be added in the future.
https://www.datawarehouse4u.info/SCD-Slowly-Changing-Dimensions.html
You use Azure Stream Analytics to receive Twitter data from Azure Event Hubs and to output the data to an Azure Blob storage account.
You need to output the count of tweets during the last five minutes every five minutes.
Each tweet must only
be counted once.
Which windowing function should you use?
A.
a five-minute Session window
B.
a five-minute Sliding window
C.
a five-minute Tumbling window
D.
a five-minute Hopping window that has one-minute hop
a five-minute Tumbling window
Explanation:
Tumbling window functions are used to segment a data stream into distinct time segments
and perform a function against them, such as the example below. The key differentiators of
a Tumbling window are that they repeat, do not overlap, and an event cannot belong to
more than one tumbling window.
References:
https://docs.microsoft.com/en-us/azure/stream-analytics/stream-analytics-window-functions
What should you recommend to prevent users outside the Litware on-premises network from accessing the analytical data store?
A
A.
a server-level virtual network rule
B.
a database-level virtual network rule
C.
a database-level firewall IP rule
D.
a server-level firewall IP rule
a server-level virtual network rule
Virtual network rules are one firewall security feature that controls whether the database
server for your single databases and elastic pool in Azure SQL Database or for your
databases in SQL Data Warehouse accepts communications that are sent from particular
subnets in virtual networks.
Server-level, not database-level: Each virtual network rule applies to your whole Azure SQL
You have an Azure subscription that contains a logical Microsoft SQL server named
Server1. Server1 hosts an Azure Synapse Analytics SQL dedicated pool named Pool1.
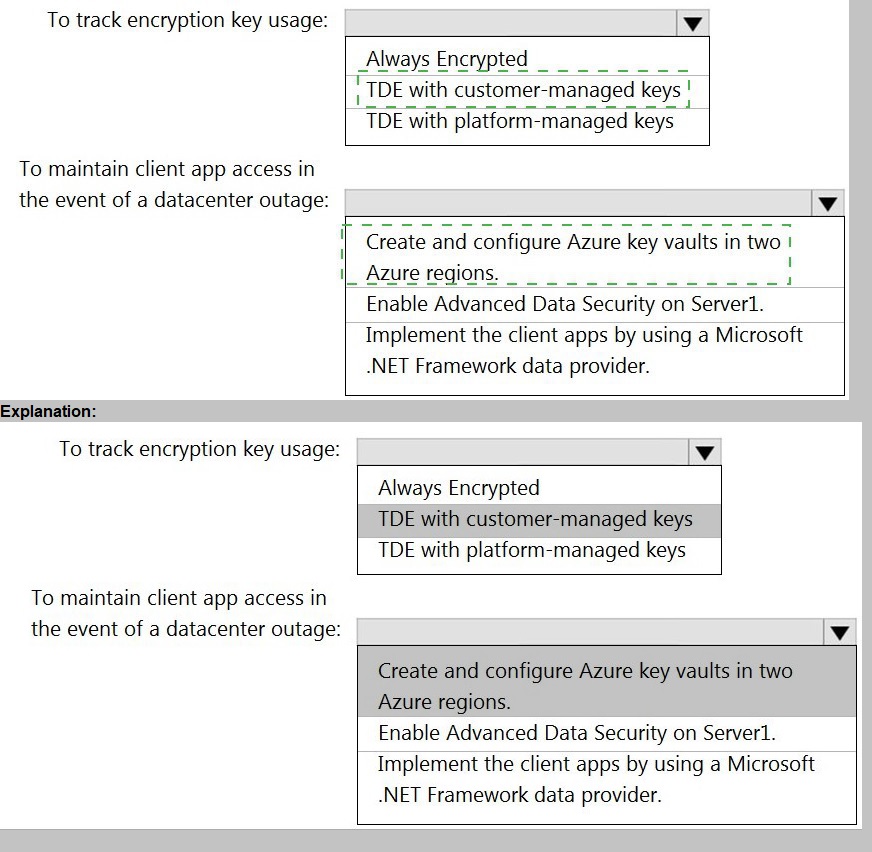
You need to recommend a Transparent Data Encryption (TDE) solution for Server1. The
solution must meet the following requirements:
Track the usage of encryption keys.
Maintain the access of client apps to Pool1 in the event of an Azure datacenter
outage that affects the availability of the encryption keys.
What should you include in the recommendation? To answer, select the appropriate
options in the answer area.
NOTE: Each correct selection is worth one point.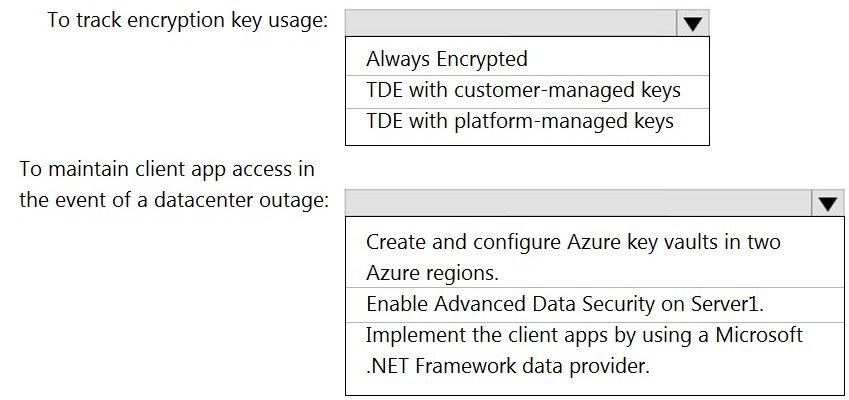
You have an Azure Storage account and a data warehouse in Azure Synapse Analytics in
the UK South region.
You need to copy blob data from the storage account to the data warehouse by using
Azure Data Factory. The solution must meet the following requirements:
Ensure that the data remains in the UK South region at all times.
Minimize administrative effort.
Which type of integration runtime should you use?
A.
Azure integration runtime
B.
Azure-SSIS integration runtime
C.
Self-hosted integration runtime
Azure integration runtime
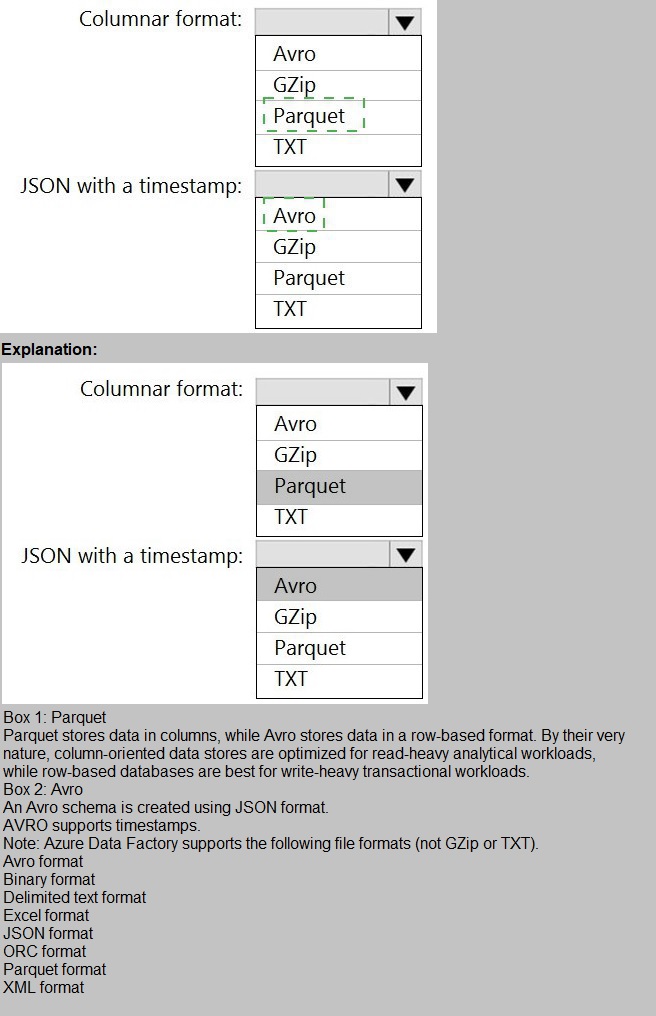
You need to output files from Azure Data Factory.
Which file format should you use for each type of output? To answer, select the appropriate
options in the answer area.
NOTE: Each correct selection is worth one point.
You are designing an enterprise data warehouse in Azure Synapse Analytics that will
contain a table named Customers. Customers will contain credit card information.
You need to recommend a solution to provide salespeople with the ability to view all the
entries in Customers.
The solution must prevent all the salespeople from viewing or inferring the credit card
information.
What should you include in the recommendation?
A.
data masking
B.
Always Encrypted
C.
column-level security
D.
row-level security
data masking
Explanation:
SQL Database dynamic data masking limits sensitive data exposure by masking it to nonprivileged
users.
The Credit card masking method exposes the last four digits of the designated fields and
adds a constant string as a prefix in the form of a credit card.
Example: XXXX-XXXX-XXXX-1234
Reference:
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-dynamic-data-maskingget-
started
| Page 3 out of 21 Pages |
| Previous |