Which of the following are risks associated with vendor lock-in? (Choose two.)
A.
The client can seamlessly move data.
B.
The vendor can change product offerings.
C.
The client receives a sufficient level of service.
D.
The client experiences decreased quality of service.
E.
The client can leverage a multicloud approach.
F.
The client experiences increased interoperability.
The vendor can change product offerings.
The client experiences decreased quality of service.
Reference: https://www.cloudflare.com/learning/cloud/what-is-vendor-lockin/#:~:
text=Vendor-lock%2Din-can-become,may-involve-reformatting%2
0the-data
A security engineer was auditing an organization’s current software development practice
and discovered that multiple open-source libraries were Integrated into the organization’s
software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the
security of the open-source libraries?
A.
Perform additional SAST/DAST on the open-source libraries.
B.
Implement the SDLC security guidelines.
C.
Track the library versions and monitor the CVE website for related vulnerabilities.
D.
Perform unit testing of the open-source libraries.
Implement the SDLC security guidelines.
Reference: https://www.whitesourcesoftware.com/resources/blog/application-security-bestpractices/
A security engineer has been asked to close all non-secure connections from the corporate network. The engineer is attempting to understand why the corporate UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:

Which of the following should the security engineer do to ensure IMAPS functions properly
on the corporate user network?
A.
Contact the email service provider and ask if the company IP is blocked.
B.
Confirm the email server certificate is installed on the corporate computers.
C.
Make sure the UTM certificate is imported on the corporate computers.
D.
Create an IMAPS firewall rule to ensure email is allowed.
Make sure the UTM certificate is imported on the corporate computers.
Which of the following is the MOST important security objective when applying
cryptography to control messages that tell an ICS how much electrical power to output?
A.
Importing the availability of messages
B.
Ensuring non-repudiation of messages
C.
Enforcing protocol conformance for messages
D.
Assuring the integrity of messages
Assuring the integrity of messages
Company A is establishing a contractual with Company B. The terms of the agreement are
formalized in a document covering the payment terms, limitation of liability, and intellectual
property rights. Which of the following documents will MOST likely contain these elements
A.
Company A-B SLA v2.docx
B.
Company A OLA v1b.docx
C.
Company A MSA v3.docx
D.
Company A MOU v1.docx
E.
Company A-B NDA v03.docx
Company A-B SLA v2.docx
An application server was recently upgraded to prefer TLS 1.3, and now users are unable
to connect their clients to the server. Attempts to reproduce the error are confirmed, and
clients are reporting the following:
ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Which of the following is MOST likely the root cause?
A.
The client application is testing PFS.
B.
The client application is configured to use ECDHE.
C.
The client application is configured to use RC4.
D.
The client application is configured to use AES-256 in GCM
The client application is configured to use RC4.
Reference: https://kinsta.com/knowledgebase/err_ssl_version_or_cipher_mismatch/
A security architect for a large, multinational manufacturer needs to design and implement
a security solution to monitor traffic.
When designing the solution, which of the following threats should the security architect
focus on to prevent attacks against the network?
A.
Packets that are the wrong size or length
B.
Use of any non-DNP3 communication on a DNP3 port
C.
Multiple solicited responses over time
D.
Application of an unsupported encryption algorithm
Multiple solicited responses over time
An organization is prioritizing efforts to remediate or mitigate risks identified during the
latest assessment. For one of the risks, a full remediation was not possible, but the
organization was able to successfully apply mitigations to reduce the likelihood of impact.
Which of the following should the organization perform NEXT?
A.
Assess the residual risk.
B.
Update the organization’s threat model.
C.
Move to the next risk in the register.
D.
Recalculate the magnitude of impact.
Recalculate the magnitude of impact.
A cybersecurity analyst receives a ticket that indicates a potential incident is occurring.
There has been a large in log files generated by a generated by a website containing a
‘’Contact US’’ form. The analyst must determine if the increase in website traffic is due to a
recent marketing campaign of if this is a potential incident. Which of the following would
BEST assist the analyst?
A.
Ensuring proper input validation is configured on the ‘’Contact US’’ form
B.
Deploy a WAF in front of the public website
C.
Checking for new rules from the inbound network IPS vendor
D.
Running the website log files through a log reduction and analysis tool
Running the website log files through a log reduction and analysis tool
A security analyst is reading the results of a successful exploit that was recently conducted
by third-party penetration testers. The testers reverse engineered a privileged executable.
In the report, the planning and execution of the exploit is detailed using logs and outputs
from the test However, the attack vector of the exploit is missing, making it harder to
recommend remediation’s. Given the following output:
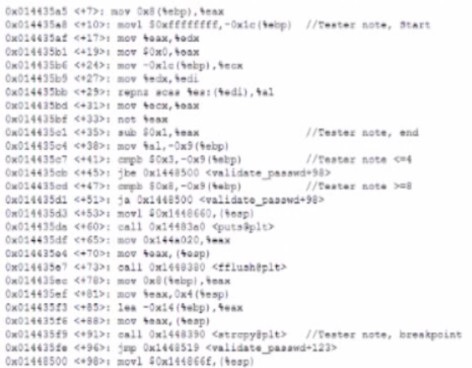
The penetration testers MOST likely took advantage of:
A.
A TOC/TOU vulnerability
B.
A plain-text password disclosure
C.
An integer overflow vulnerability
D.
A buffer overflow vulnerability
A TOC/TOU vulnerability
| Page 4 out of 20 Pages |
| Previous |