A university issues badges through a homegrown identity management system to all staff
and students. Each week during the summer, temporary summer school students arrive
and need to be issued a badge to access minimal campus resources. The security team
received a report from an outside auditor indicating the homegrown system is not
consistent with best practices in the security field and leaves the institution vulnerable.
Which of the following should the security team recommend FIRST?
A.
Investigating a potential threat identified in logs related to the identity management
system
B.
Updating the identity management system to use discretionary access control
C.
Beginning research on two-factor authentication to later introduce into the identity
management system
D.
Working with procurement and creating a requirements document to select a new IAM
system/vendor
Investigating a potential threat identified in logs related to the identity management
system
A business stores personal client data of individuals residing in the EU in order to process
requests for mortgage loan approvals.
Which of the following does the business’s IT manager need to consider?
A.
The availability of personal data
B.
The right to personal data erasure
C.
The company’s annual revenue
D.
The language of the web application
The right to personal data erasure
Reference: https://gdpr.eu/right-to-beforgotten/#:~:
text=Also-known-as-the-right,to-delete-their-person
al-data.&text=The-General-Data-Protection-Regulation,collected%2C%2
0processed%2C-and-erased
A cybersecurity engineer analyst a system for vulnerabilities. The tool created an OVAL.
Results document as output. Which of the following would enable the engineer to interpret
the results in a human readable form? (Select TWO.)
A.
Text editor
B.
OOXML editor
C.
Event Viewer
D.
XML style sheet
E.
SCAP tool
F.
Debugging utility
Text editor
SCAP tool
All staff at a company have started working remotely due to a global pandemic. To
transition to remote work, the company has migrated to SaaS collaboration tools. The
human resources department wants to use these tools to process sensitive information but
is concerned the data could be:
Leaked to the media via printing of the documents
Sent to a personal email address
Accessed and viewed by systems administrators
Uploaded to a file storage site
Which of the following would mitigate the department’s concerns?
A.
Data loss detection, reverse proxy, EDR, and PGP
B.
VDI, proxy, CASB, and DRM
C.
Watermarking, forward proxy, DLP, and MFA
D.
Proxy, secure VPN, endpoint encryption, and AV
VDI, proxy, CASB, and DRM
A company plans to build an entirely remote workforce that utilizes a cloud-based
infrastructure. The Chief Information Security Officer asks the security engineer to design
connectivity to meet the following requirements:
Only users with corporate-owned devices can directly access servers hosted by the cloud
provider.
The company can control what SaaS applications each individual user can access.
User browser activity can be monitored.
Which of the following solutions would BEST meet these requirements?
A.
IAM gateway, MDM, and reverse proxy
B.
VPN, CASB, and secure web gateway
C.
SSL tunnel, DLP, and host-based firewall
D.
API gateway, UEM, and forward proxy
VPN, CASB, and secure web gateway
After a security incident, a network security engineer discovers that a portion of the
company’s sensitive external traffic has been redirected through a secondary ISP that is
not normally used.
Which of the following would BEST secure the routes while allowing the network to function
in the event of a single provider failure?
A.
Disable BGP and implement a single static route for each internal network.
B.
Implement a BGP route reflector.
C.
Implement an inbound BGP prefix list.
D.
Disable BGP and implement OSPF.
Implement a BGP route reflector.
A company that uses AD is migrating services from LDAP to secure LDAP. During the pilot
phase, services are not connecting properly to secure LDAP. Block is an except of output
from the troubleshooting session: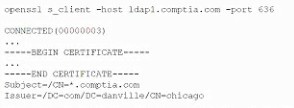
Which of the following BEST explains why secure LDAP is not working? (Select TWO.)
A.
The clients may not trust idapt by default.
B.
The secure LDAP service is not started, so no connections can be made.
C.
Danvills.com is under a DDoS-inator attack and cannot respond to OCSP requests.
D.
Secure LDAP should be running on UDP rather than TCP.
E.
The company is using the wrong port. It should be using port 389 for secure LDAP.
F.
Secure LDAP does not support wildcard certificates.
G.
The clients may not trust Chicago by default.
The secure LDAP service is not started, so no connections can be made.
The company is using the wrong port. It should be using port 389 for secure LDAP.
A security is assisting the marketing department with ensuring the security of the
organization’s social media platforms. The two main concerns are:
The Chief marketing officer (CMO) email is being used department wide as the username
The password has been shared within the department
Which of the following controls would be BEST for the analyst to recommend?
A.
Configure MFA for all users to decrease their reliance on other authentication.
B.
Have periodic, scheduled reviews to determine which OAuth configuration are set for
each media platform.
C.
Create multiple social media accounts for all marketing user to separate their actions.
D.
Ensue the password being shared is sufficiently and not written down anywhere.
Configure MFA for all users to decrease their reliance on other authentication.
A company is looking for a solution to hide data stored in databases. The solution must
meet the following requirements:
Be efficient at protecting the production environment
Not require any change to the application
Act at the presentation layer
Which of the following techniques should be used?
A.
Masking
B.
Tokenization
C.
Algorithmic
D.
Random substitution
Masking
A security analyst receives an alert from the SIEM regarding unusual activity on an
authorized public SSH jump server. To further investigate, the analyst pulls the event logs
directly from /var/log/auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks by the activity in the
logs?
A.
Alerting the misconfigured service account password
B.
Modifying the AllowUsers configuration directive
C.
Restricting external port 22 access
D.
Implementing host-key preferences
Restricting external port 22 access
Reference: https://www.rapid7.com/blog/post/2017/10/04/how-to-secure-ssh-server-usingport-
knocking-on-ubuntu-linux/
| Page 3 out of 20 Pages |
| Previous |