Topic 5: Mix Questions
You have an Azure subscription that contains a user named User1.
You need to ensure that User1 can deploy virtual machines and manage virtual networks.
The solution must use the principle of least privilege.
Which role-based access control (RBAC) role should you assign to User1?
A.
Owner
B.
Virtual Machine Administrator Login
C.
Contributor
D.
Virtual Machine Contributor
Virtual Machine Contributor
To ensure that User1 can deploy virtual machines and manage virtual networks, you need to assign an RBAC role that grants the necessary permissions to perform these tasks. The solution must also use the principle of least privilege, which means that you should only grant the minimum level of access required to accomplish the goal. Based on these requirements, the best RBAC role to assign to User1 is D. Virtual Machine Contributor. This role allows User1 to create and manage virtual machines, disks, snapshots, and network interfaces. It also allows User1 to connect virtual machines to existing virtual networks and subnets. However, it does not allow User1 to create or delete virtual networks or subnets, or to access the virtual machines themselves. This role follows the principle of least privilege by limiting User1’s access to only the resources and actions that are relevant to deploying virtual machines and managing virtual networks1.
You have an Azure subscription named Subscription1 that contains the resources shown in the following table.
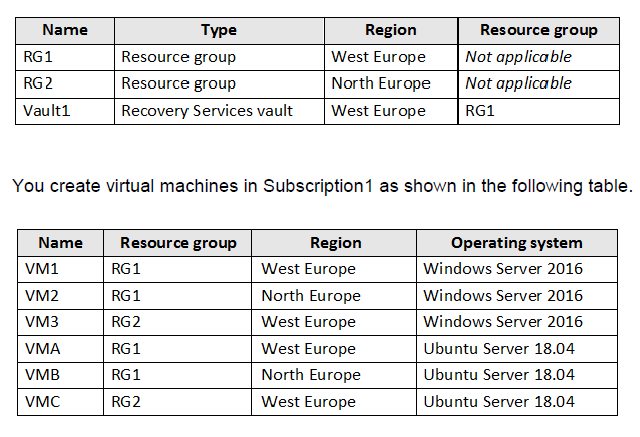
You plan to use Vault1 for the backup of as many virtual machines as possible. Which virtual machines can be backed up to Vault1?
A.
VM1, VM3, VMA, and VMC only
B.
VM1 and VM3 only
C.
VM1, VM2, VM3, VMA, VMB, and VMC
D.
VM1 only
E.
VM3 and VMC only
VM1, VM3, VMA, and VMC only
Explanation:
To create a vault to protect virtual machines, the vault must be in the same region as the virtual machines. If you have virtual machines in several regions, create a Recovery Services vault in each region.
References:
https://docs.microsoft.com/bs-cyrl-ba/azure/backup/backup-create-rs-vault
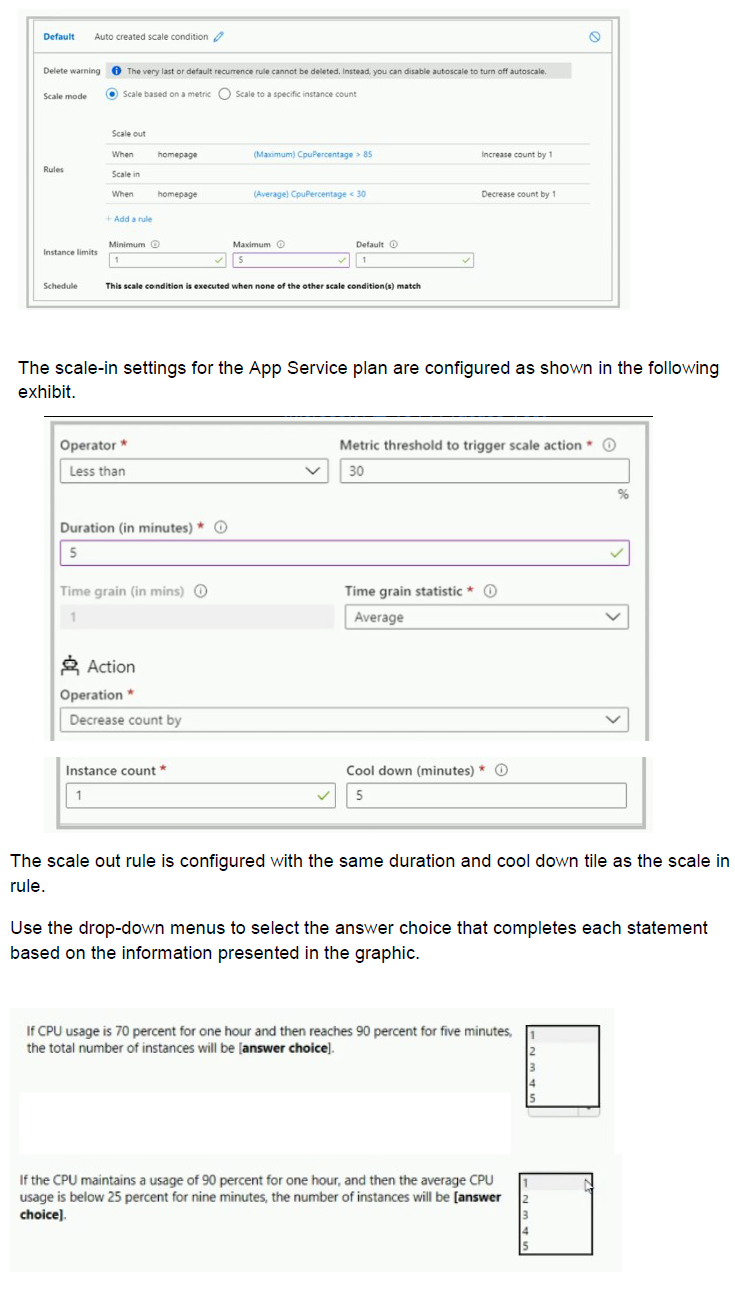
You have the App Service plan shown in the following exhibit.

You have an Azure subscription that contains the virtual networks shown in the following table.
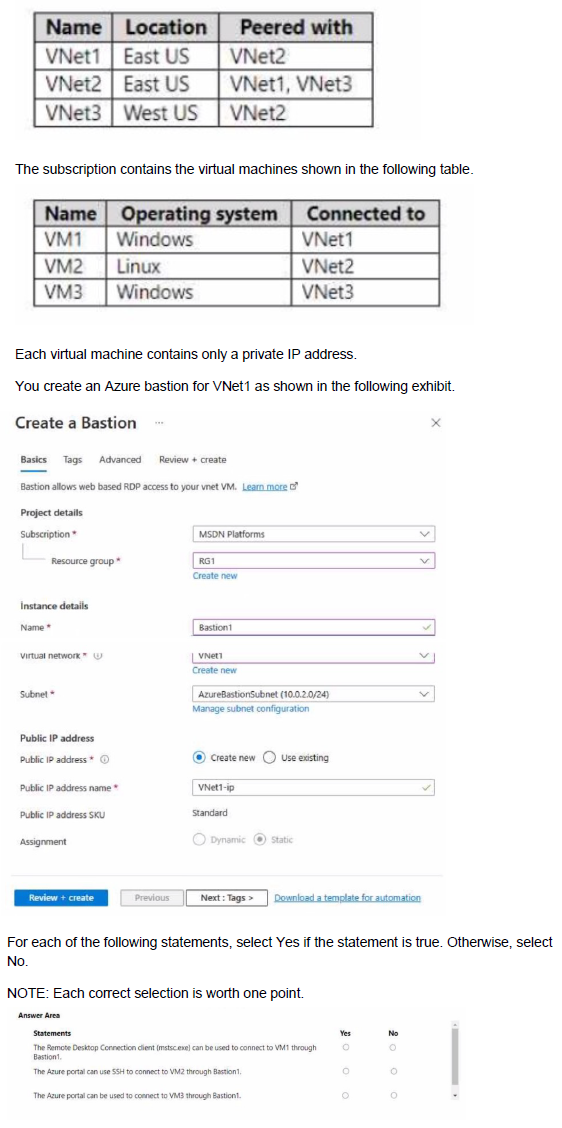
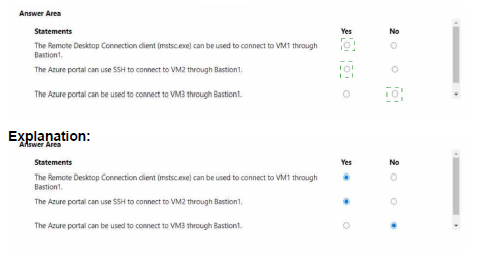
You have an Azure virtual machine named VM1 and an Azure key vault named Vault1. On VM1, you plan to configure Azure Disk Encryption to use a key encryption key (KEK) You need to prepare Vault! for Azure Disk Encryption.
Which two actions should you perform on Vault1? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A.
Create a new key.
B.
Select Azure Virtual machines for deployment
C.
Configure a key rotation policy.
D.
Create a new secret.
E.
Select Azure Disk Encryption for volume encryption
Create a new key.
Configure a key rotation policy.
Explanation:
To prepare Vault1 for Azure Disk Encryption, you need to perform the following actions on Vault1:
Create a new key. A key encryption key (KEK) is an encryption key that is used to encrypt the encryption secrets before they are stored in the key vault. You can create a new KEK by using the Azure CLI, the Azure PowerShell, or the Azure portal1. You can also import an existing KEK from another source, such as a hardware security module (HSM)2. The KEK must be a 2048-bit RSA key or a 256-bit AES key3.
Select Azure Disk Encryption for volume encryption. This is an advanced access policy setting that enables Azure Disk Encryption to access the keys and secrets in the key vault. You can select this setting by using the Azure CLI, the Azure PowerShell, or the Azure portal4. You must also enable access to Microsoft Trusted Services if you have enabled the firewall on the key vault.
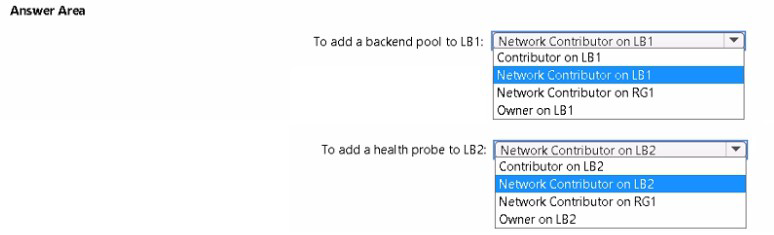
You have an Azure subscription named Subscription1 that contains a resource group named RG1.
In RG1, you create an internal load balancer named LB1 and a public load balancer named LB2.
You need to ensure that an administrator named Admin1 can manage LB1 and LB2. The solution must follow the principle of least privilege.
Which role should you assign to Admin1 for each task? To answer, select the appropriate options in the answer area.
NOTE; Each correct selection is worth one point.
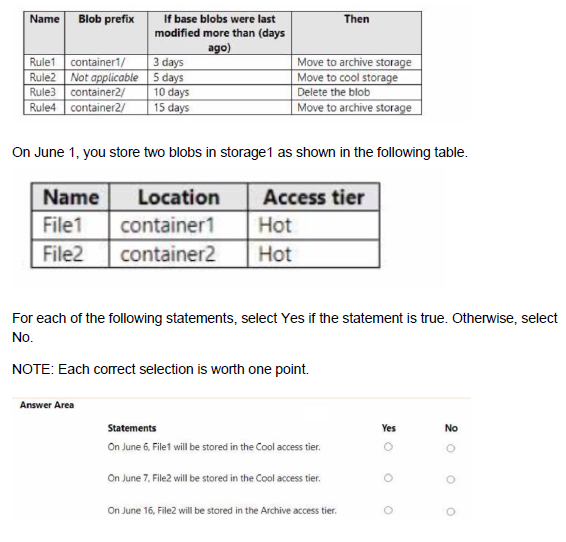
You have an Azure subscription. The subscription contains a storage account named storage1 that has the lifecycle management rules shown in the following table.
You have an Azure Storage account named storage1 that uses Azure Blob storage and Azure File storage. You need to use AzCopy to copy data to the blob storage and file storage in storage1. Which authentication method should you use for each type of storage? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
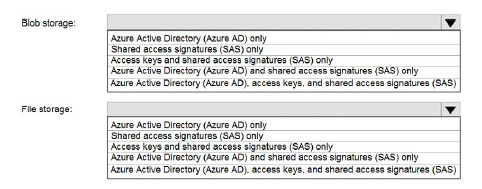
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription.
You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: You configure a custom policy definition, and then you assign the policy to the subscription.
Does this meet the goal?
A.
Yes
B.
No
No
Explanation:
A custom policy definition is a way to define your own rules for using Azure resources. You can use custom policies to enforce compliance, security, cost management, or organization-specific requirements. However, a custom policy definition alone is not enough to meet the goal of automatically blocking TCP port 8080 between the virtual networks. You also need to create a policy assignment that applies the custom policy definition to the scope of the subscription. A policy assignment is the link between a policy definition and an Azure resource. Without a policy assignment, the custom policy definition will not take effect. Therefore, the solution does not meet the goal.
References:
Tutorial: Create a custom policy definition
Create and manage policies to enforce compliance
You plan to automate the deployment of a virtual machine scale set that uses the Windows Server 2016 Datacenter image.
You need to ensure that when the scale set virtual machines are provisioned, they have web server components installed.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE Each correct selection is worth one point.
A.
Modify the extensionProfile section of the Azure Resource Manager template.
B.
Create a new virtual machine scale set in the Azure portal.
C.
Create an Azure policy.
D.
Create an automation account
E.
Upload a configuration script.
Modify the extensionProfile section of the Azure Resource Manager template.
Create a new virtual machine scale set in the Azure portal.
To automate the deployment of a virtual machine scale set that uses the Windows Server 2016 Datacenter image and has web server components installed, you need to perform the following actions:
Modify the extensionProfile section of the Azure Resource Manager template. This section defines the extensions that are applied to the scale set virtual machines after they are provisioned. You can use the Custom Script Extension to run PowerShell scripts that install and configure the web server components. For more information, see Deploy an application to an Azure Virtual Machine Scale Set1. Upload a configuration script. This is the PowerShell script that contains the commands to install and configure the web server components. You can upload the script to a storage account or a GitHub repository, and then reference it in the extensionProfile section of the template. For an example of a configuration script, see Tutorial: Install applications in Virtual Machine Scale Sets with Azure PowerShell2.