Which action prevent toll fraud in Cisco Unified Communications Manager?
A.
Configure ad hoc conference restriction
B.
Implement toll fraud restriction in the Cisco IOS router
C.
Allow off-net to off-net transfers
D.
Implement route patterns in Cisco Unified CM.
Configure ad hoc conference restriction
An engineer is designing a load balancing solution for two Cisco Unified Border routers.
The first router (cube1.abc.com) takes 60% of the calls and the second router
(cute2.abc.com) takes 40% of the calls, Assume all DNS A records have been created.
Which two SRV records are needed for a load balanced solution? (Choose two.)
A.
sip_udp.abc.com 60 IN SRV 1 40 5060 cube2.abc.com
B.
sip_udp.abc.com 60 IN SRV 3 60 5060 cube2.abc.com
C.
sip_udp.abc.com 60 IN SRV 60 1 5060 cube1.abc.com
D.
sip_udp.abc.com 60 IN SRV 2 60 5060 cube1.abc.com
E.
sip_udp.abc.com 60 IN SRV 1 60 5060 cube1.abc.com
sip_udp.abc.com 60 IN SRV 1 40 5060 cube2.abc.com
sip_udp.abc.com 60 IN SRV 1 60 5060 cube1.abc.com
Which description of the Mobile and Remote Access feature is true?
A.
Collaboration Edge feature that enables remote individuals to perform international calls
from Jabber with a VPN connection
B.
Collaboration Edge feature that enables remote individual to access enterprise
collaboration services via Jabber with the use of a VPN connection
C.
Collaboration Edge feature that enables remote individuals to access enterprise
collaboration services via Jabber without the use of a VPN connection
D.
Collaboration Edge feature that enables remote individuals to access all enterprise
collaboration services using a PC within the corporate environment
Collaboration Edge feature that enables remote individuals to access enterprise
collaboration services via Jabber without the use of a VPN connection
Which DHCP option must be set up for new phones to obtain the TFTP server IP address?
A.
Option 66
B.
Option 15
C.
Option 120
D.
Option 6
Option 66
Which configuration tells a switch port to send Cisco Discovery protocol packets that
configure an attached Cisco IP phone to trust tagged traffic that is received from a device that is connected to the access port on the Cisco IP phone?

A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option B
What is set when using CoS to mark an Ethernet frame?
A.
IPP bits
B.
802.1p User Priority bits
C.
IP ECN bits
D.
DCSP bits
802.1p User Priority bits
Refer to the exhibit.
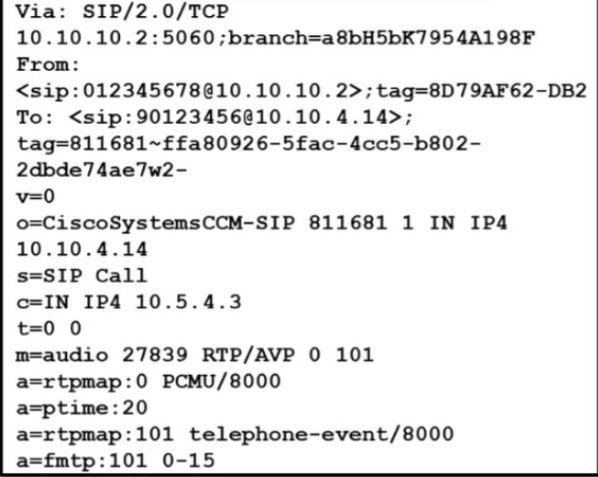
Which Codec is negotiated?
A.
G.729
B.
ILBC
C.
G.711ulaw
D.
G.728
G.711ulaw
An engineer is notified that the Cisco TelePresence MX800 that is registered in Cisco
Unified communications Manager shows an empty panel, and the Touch 10 shows a
corresponding icon with no action when pressed. Where does the engineer go to remove the inactive custom panel?
A.
The phone configuration page in CUCM Administration
B.
The SIP Trunk security profile page in CUCM Administration
C.
The software Upgrades page in CUCM OS Administration
D.
The In-Room control Editor on the webpage of the MX800
The In-Room control Editor on the webpage of the MX800
An engineer is setting up a system with voice and video endpoints using auto-QoS policy
on the switches. Which DSCP values are expected for interactive voice and video?
A.
EF AND AF41
B.
EF AND AF21
C.
EF AND CS3
D.
EF AND CS6
EF AND AF41
Refer to the exhibit.

A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
| Page 5 out of 28 Pages |
| Previous |