Topic 1: Exam Pool A
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware?
(Choose two)
A.
Sophos engine
B.
white list
C.
RAT
D.
outbreak filters
E.
DLP
Sophos engine
outbreak filters
Which Cisco platform ensures that machines that connect to organizational networks have
the recommended
antivirus definitions and patches to help prevent an organizational malware outbreak?
A.
Cisco WiSM
B.
Cisco ESA
C.
Cisco ISE
D.
Cisco Prime Infrastructure
Cisco ISE
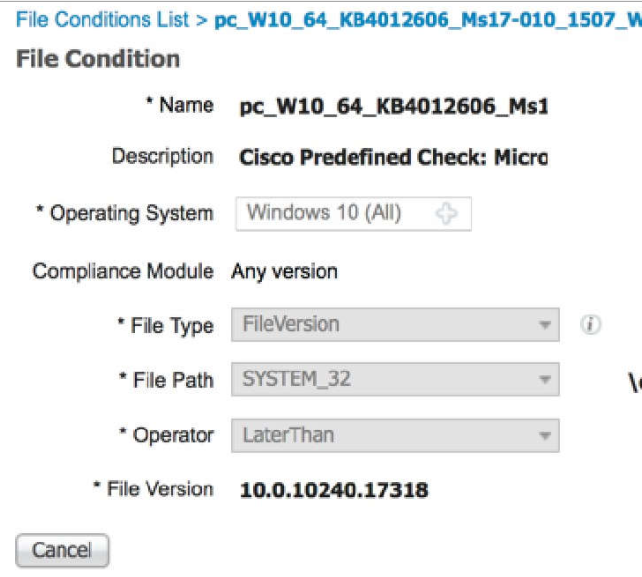
A posture policy is a collection of posture requirements, which
are associated with one or more identity groups, and operating systems. We can configure
ISE to check for the Windows patch at Work Centers > Posture > Posture Elements >
Conditions > File.In this example, we are going to use the predefined file check to ensure
that our Windows 10 clients have the critical security patch installed to prevent the Wanna
Cry malware; and we can also configure ISE to update the client with this patch.
In which two ways does a system administrator send web traffic transparently to the Web Security Appliance?
(Choose two)
A.
configure Active Directory Group Policies to push proxy settings
B.
configure policy-based routing on the network infrastructure
C.
reference a Proxy Auto Config file
D.
configure the proxy IP address in the web-browser settings
E.
use Web Cache Communication Protocol
configure policy-based routing on the network infrastructure
use Web Cache Communication Protocol
What is a benefit of conducting device compliance checks?
A.
It indicates what type of operating system is connecting to the network.
B.
It validates if anti-virus software is installed
C.
It scans endpoints to determine if malicious activity is taking place
D.
It detects email phishing attacks.
It validates if anti-virus software is installed
Which type of algorithm provides the highest level of protection against brute-force attacks?
A.
PFS
B.
HMAC
C.
MD5
D.
SHA
SHA
What is a difference between FlexVPN and DMVPN?
A.
DMVPN uses IKEv1 or IKEv2, FlexVPN only uses IKEv1
B.
DMVPN uses only IKEv1 FlexVPN uses only IKEv2
C.
FlexVPN uses IKEv2, DMVPN uses IKEv1 or IKEv2
D.
FlexVPN uses IKEv1 or IKEv2, DMVPN uses only IKEv2
FlexVPN uses IKEv2, DMVPN uses IKEv1 or IKEv2
When configuring ISAKMP for IKEv1 Phase1 on a Cisco IOS router, an administrator
needs to input the
command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the
IP addressing in this command issued for. What would be the effect of changing the IP
address from 0.0.0.0 to 1.2.3.4?
A.
The key server that is managing the keys for the connection will be at 1.2.3.4
B.
The remote connection will only be allowed from 1.2.3.4
C.
The address that will be used as the crypto validation authority
D.
All IP addresses other than 1.2.3.4 will be allowed
The remote connection will only be allowed from 1.2.3.4
The command crypto isakmp key cisco address 1.2.3.4
authenticates the IP address of the 1.2.3.4 peer by using the key cisco. The address of “0.0.0.0” will authenticate any address with this key.
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
A.
Time-based one-time passwords
B.
Data loss prevention
C.
Heuristic-based filtering
D.
Geolocation-based filtering
E.
NetFlow
Data loss prevention
Geolocation-based filtering
https://www.cisco.com/c/en/us/td/docs/security/esa/esa11-
0/user_guide_fs/b_ESA_Admin_Guide_11_0/b_ESA_Admin_Guide_chapter_00.html
Drag and drop the VPN functions from the left onto the description on the right.
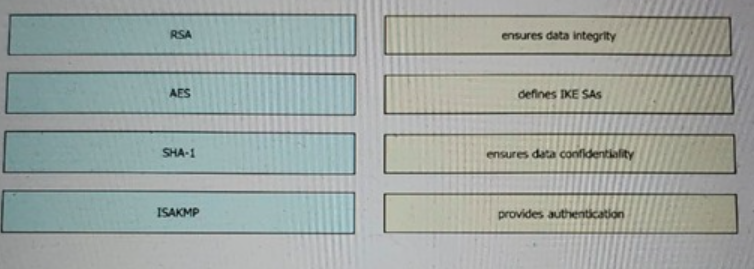
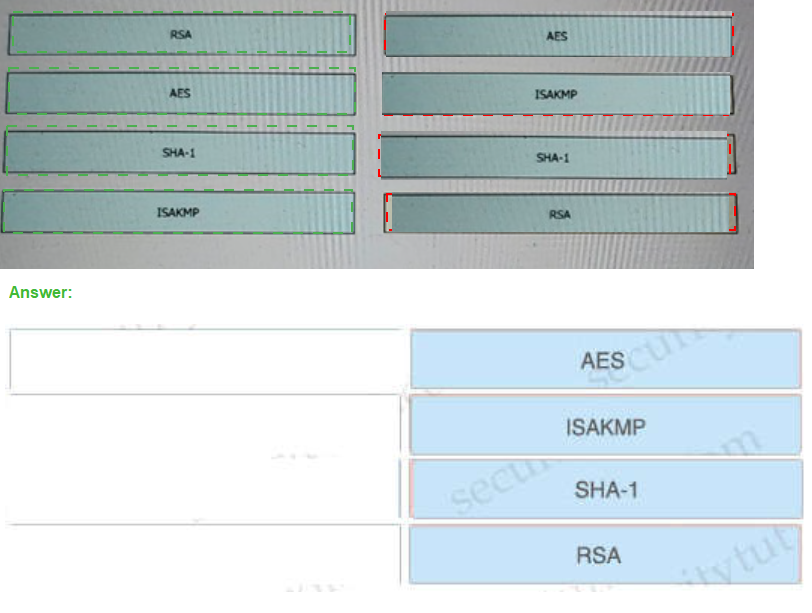
The purpose of message integrity algorithms, such as Secure Hash Algorithm
(SHA-1), ensures data has notbeen changed in transit. They use one way hash functions to determine if data has been changed.SHA-1, which is also known as HMAC-SHA-1 is a
strong cryptographic hashing algorithm, stronger thananother popular algorithm known as
Message Digest 5 (MD5). SHA-1 is used to provide data integrity (toguarantee data has not
been altered in transit) and authentication (to guarantee data came from the source itwas
supposed to come from). SHA was produced to be used with the digital signature
standard.A VPN uses groundbreaking 256-bit AES encryption technology to secure your
online connection againstcyberattacks that can compromise your security. It also offers
robust protocols to combat malicious attacks and reinforce your online identity.IKE SAs
describe the security parameters between two IKE devices, the first stage in establishing
IPSec.
Which risk is created when using an Internet browser to access cloud-based service?
A.
misconfiguration of infrastructure, which allows unauthorized access
B.
intermittent connection to the cloud connectors
C.
vulnerabilities within protocol
D.
insecure implementation of API
vulnerabilities within protocol
| Page 9 out of 63 Pages |
| Previous |