Topic 2: Exam Pool B
Why is it important to have logical security controls on endpoints even though the users are
trained to spot security threats and the network devices already help prevent them?
A.
to prevent theft of the endpoints
B.
because defense-in-depth stops at the network
C.
to expose the endpoint to more threats
D.
because human error or insider threats will still exist
because human error or insider threats will still exist
What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs?
A.
Multiple NetFlow collectors are supported
B.
Advanced NetFlow v9 templates and legacy v5 formatting are supported
C.
Secure NetFlow connections are optimized for Cisco Prime Infrastructure
D.
Flow-create events are delayed
Advanced NetFlow v9 templates and legacy v5 formatting are supported
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
A.
STIX
B.
XMPP
C.
pxGrid
D.
SMTP
STIX
TAXII (Trusted Automated Exchange of Indicator Information) is a standard that provides a transport
What is the purpose of the My Devices Portal in a Cisco ISE environment?
A.
to register new laptops and mobile devices
B.
to request a newly provisioned mobile device
C.
to provision userless and agentless systems
D.
to manage and deploy antivirus definitions and patches on systems owned by the end
user
to register new laptops and mobile devices
An organization recently installed a Cisco WSA and would like to take advantage of the
AVC engine to allow the organization to create a policy to control application specific
activity. After enabling the AVC engine, what must be done to implement this?
A.
Use security services to configure the traffic monitor, .
B.
Use URL categorization to prevent the application traffic
C.
Use an access policy group to configure application control settings
D.
Use web security reporting to validate engine functionality
Use an access policy group to configure application control settings
The Application Visibility and Control (AVC) engine
lets you create policies to control application activity on the network without having to fully
understand the underlying technology of each application. You can configure application
control settings in Access Policy groups. You can block or allow applications individually or
according to application type. You can also apply controls to particular application types.
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two)
A.
DDoS
B.
antispam
C.
antivirus
D.
encryption
E.
DLP
encryption
DLP
https://www.cisco.com/c/dam/en/us/td/docs/security/ces/overview_guide/Cisco_Cloud_Hybrid_Email_Security_Overview_Guide.pdf
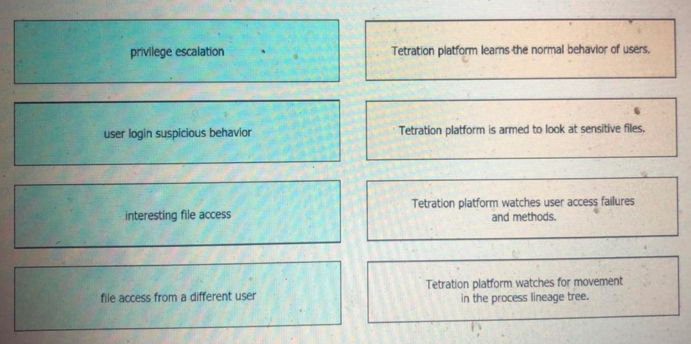
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the
correct definitions on the right.

Which Cisco product is open, scalable, and built on IETF standards to allow multiple
security products from
Cisco and other vendors to share data and interoperate with each other?
A.
Advanced Malware Protection
B.
Platform Exchange Grid
C.
Multifactor Platform Integration
D.
Firepower Threat Defense
Platform Exchange Grid
With Cisco pxGrid (Platform Exchange Grid), your multiple
security products can now share data and work together. This open, scalable, and IETF
standards-driven platform helps you automate security to get answers and contain threats
faster.
A network administrator needs to find out what assets currently exist on the network. Thirdparty
systems need to be able to feed host data into Cisco Firepower. What must be
configured to accomplish this?
A.
a Network Discovery policy to receive data from the host
B.
a Threat Intelligence policy to download the data from the host
C.
a File Analysis policy to send file data into Cisco Firepower
D.
a Network Analysis policy to receive NetFlow data from the host
a Network Discovery policy to receive data from the host
You can configure discovery rules to tailor the discovery of host
and application data to your needs.The Firepower System can use data from NetFlow
exporters to generate connection and discovery events, and to add host and application
data to the network map.A network analysis policy governs how traffic is decoded and
preprocessed so it can be further evaluated, especially for anomalous traffic that might
signal an intrusion attempt -> Answer D is not correct.
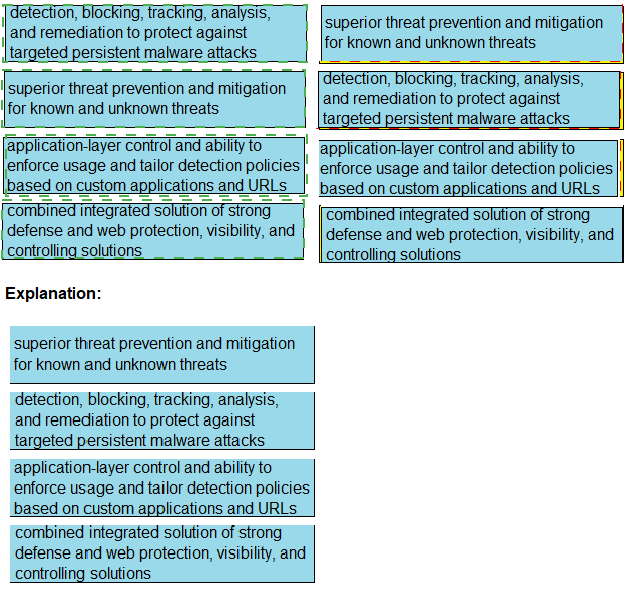
Drag and drop the capabilities from the left onto the correct technologies on the right.

Text, chat or text message
Description automatically generated
| Page 6 out of 63 Pages |
| Previous |