Topic 2: Exam Pool B
What features does Cisco FTDv provide over ASAv?
A.
Cisco FTDv runs on VMWare while ASAv does not
B.
Cisco FTDv provides 1GB of firewall throughput while Cisco ASAv does not
C.
Cisco FTDv runs on AWS while ASAv does not
D.
Cisco FTDv supports URL filtering while ASAv does not
Cisco FTDv supports URL filtering while ASAv does not
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications
traffic. Where must the
ASA be added on the Cisco UC Manager platform?
A.
Certificate Trust List
B.
Endpoint Trust List
C.
Enterprise Proxy Service
D.
Secured Collaboration Proxy
Certificate Trust List
Refer to the exhibit.
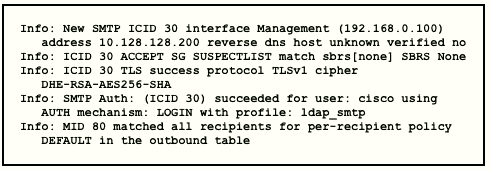
Which type of authentication is in use?
A.
LDAP authentication for Microsoft Outlook
B.
POP3 authentication
C.
SMTP relay server authentication
D.
external user and relay mail authentication
external user and relay mail authentication
Reference: https://www.cisco.com/c/en/us/support/docs/security/email-securityappliance/
118844-technoteesa-00.htmlThe exhibit in this Qshows a successful TLS
connection from the remote host (reception) in the mail log.
A Cisco ESA administrator has been tasked with configuring the Cisco ESA to ensure there
are no viruses before quarantined emails are delivered. In addition, delivery of mail from
known bad mail servers must be prevented. Which two actions must be taken in order to
meet these requirements? (Choose two)
A.
Use outbreak filters from SenderBase
B.
Enable a message tracking service
C.
Configure a recipient access table
D.
Deploy the Cisco ESA in the DMZ
E.
Scan quarantined emails using AntiVirus signatures
Use outbreak filters from SenderBase
Scan quarantined emails using AntiVirus signatures
Reference: https://www.cisco.com/c/en/us/td/docs/security/esa/esa12-
0/user_guide/b_ESA_Admin_Guide_12_0/b_ESA_Admin_Guide_12_0_chapter_0100100.
html-> Therefore Outbreak filters can be used to block emails from bad mail servers.Web
servers and email gateways are generally located in the DMZ soNote: The recipient access
table (RAT), not to be confused with remote-access Trojan (also RAT), is a Cisco ESA term
that defines which recipients are accepted by a public listener.
Which protocol provides the strongest throughput performance when using Cisco
AnyConnect VPN?
A.
TLSv1.2
B.
TLSv1.1
C.
BJTLSv1
D.
DTLSv1
DTLSv1
DTLS is used for delay sensitive applications (voice and video)
as its UDP based while TLS is TCP based.Therefore DTLS offers strongest throughput
performance. The throughput of DTLS at the time of AnyConnect connection can be
expected to have processing performance close to VPN throughput.
What must be configured in Cisco ISE to enforce reauthentication of an endpoint session
when an endpoint is
deleted from an identity group?
A.
posture assessment
B.
CoA
C.
external identity source
D.
SNMP probe
CoA
Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/1-
3/admin_guide/b_ise_admin_guide_13/b_ise_admin_guide_sample_chapter_010101.html
Which product allows Cisco FMC to push security intelligence observable to its sensors
from other products?
A.
Encrypted Traffic Analytics
B.
Threat Intelligence Director
C.
Cognitive Threat Analytics
D.
Cisco Talos Intelligence
Threat Intelligence Director
How is DNS tunneling used to exfiltrate data out of a corporate network?
A.
It corrupts DNS servers by replacing the actual IP address with a rogue address to
collect information or start other attacks.
B.
It encodes the payload with random characters that are broken into short strings and the DNS server rebuilds the exfiltrated data.
C.
It redirects DNS requests to a malicious server used to steal user credentials, which
allows further damage
and theft on the network.
D.
It leverages the DNS server by permitting recursive lookups to spread the attack to other
DNS servers
It encodes the payload with random characters that are broken into short strings and the DNS server rebuilds the exfiltrated data.
Domain name system (DNS) is the protocol that translates
human-friendly URLs, such as securitytut.com, into IP addresses, such as 183.33.24.13.
Because DNS messages are only used as the beginning of each communication and they
are not intended for data transfer, many organizations do not monitor their DNS traffic for
malicious activity. As a result, DNS-based attacks can be effective if launched against their
networks. DNS tunneling is one such attack.An example of DNS Tunneling is shown below:
The attacker incorporates one of many open-source DNS tunneling kits into an
authoritative DNSnameserver (NS) and malicious payload.2. An IP address (e.g.
1.2.3.4) is allocated from the attacker’s infrastructure and a domain name (e.g.
attackerdomain.com) is registered or reused. The registrar informs the top-level
domain (.com) nameservers to refer requests for attackerdomain.com to
ns.attackerdomain.com, which has a DNS record mapped to 1.2.3.43. The
attacker compromises a system with the malicious payload. Once the desired data
is obtained, the payload encodes the data as a series of 32 characters (0-9, A-Z)
broken into short strings (3KJ242AIE9, P028X977W,…).4. The payload initiates
thousands of unique DNS record requests to the attacker’s domain with each
string as
Reference: https://learn-umbrella.cisco.com/i/775902-dns-tunneling/0
A network engineer has been tasked with adding a new medical device to the network.
Cisco ISE is being used as the NAC server, and the new device does not have a supplicant
available. What must be done in order to securely connect this device to the network?
A.
Use MAB with profiling
B.
Use MAB with posture assessment
C.
Use 802.1X with posture assessment
D.
Use 802.1X with profiling
Use MAB with profiling
Reference: https://community.cisco.com/t5/security-documents/ise-profiling-designguide/
ta-p/3739456
An engineer is configuring a Cisco ESA and wants to control whether to accept or reject email messages to a recipient address. Which list contains the allowed recipient addresses?
A.
SAT
B.
HAT
C.
BAT
D.
RAT
RAT
| Page 3 out of 63 Pages |
| Previous |