Topic 3: Exam Pool C
What are two functionalities of northbound and southbound APIs within Cisco SDN
architecture? (Choose two.)
A.
Southbound APIs are used to define how SDN controllers integrate with applications.
B.
Southbound interfaces utilize device configurations such as VLANs and IP addresses.
C.
Northbound APIs utilize RESTful API methods such as GET, POST, and DELETE.
D.
Southbound APIs utilize CLI, SNMP, and RESTCONF.
E.
Northbound interfaces utilize OpenFlow and OpFlex to integrate with network devices.
Northbound APIs utilize RESTful API methods such as GET, POST, and DELETE.
Southbound APIs utilize CLI, SNMP, and RESTCONF.
What are two rootkit types? (Choose two)
A.
registry
B.
virtual
C.
bootloader
D.
user mode
E.
buffer mode
bootloader
user mode
The term ‘rootkit’ originally comes from the Unix world, where the
word ‘root’ is used to describe a user with thehighest possible level of access privileges, similar to an ‘Administrator’ in Windows. The word ‘kit’ refers to thesoftware that grants root-level access to the machine. Put the two together and you get ‘rootkit’, a program that gives someone – with legitimate or malicious intentions – privileged access to a computer.There are four main types of rootkits: Kernel rootkits, User mode rootkits, Bootloader rootkits, Memory rootkits
Which technology should be used to help prevent an attacker from stealing usernames and
passwords of users within an organization?
A.
RADIUS-based REAP
B.
fingerprinting
C.
Dynamic ARP Inspection
D.
multifactor authentication
multifactor authentication
Which solution supports high availability in routed or transparent mode as well as in northbound and southbound deployments?
A.
Cisco FTD with Cisco ASDM
B.
Cisco FTD with Cisco FMC
C.
Cisco Firepower NGFW physical appliance with Cisco. FMC
D.
Cisco Firepower NGFW Virtual appliance with Cisco FMC
Cisco FTD with Cisco FMC
What is a difference between GETVPN and IPsec?
A.
GETVPN reduces latency and provides encryption over MPLS without the use of a
central hub
B.
GETVPN provides key management and security association management
C.
GETVPN is based on IKEv2 and does not support IKEv1
D.
GETVPN is used to build a VPN network with multiple sites without having to statically
configure all devices
GETVPN provides key management and security association management
Which industry standard is used to integrate Cisco ISE and pxGrid to each other and with
other
interoperable security platforms?
A.
IEEE
B.
IETF
C.
NIST
D.
ANSI
IETF
Refer to the exhibit.
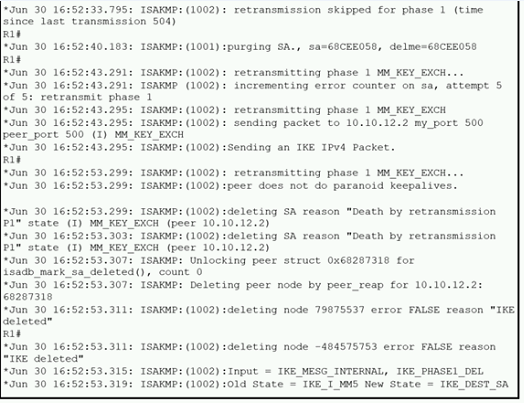
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
A.
hashing algorithm mismatch
B.
encryption algorithm mismatch
C.
authentication key mismatch
D.
interesting traffic was not applied
authentication key mismatch
Which CLI command is used to enable URL filtering support for shortened URLs on the
Cisco ESA?
A.
webadvancedconfig
B.
websecurity advancedconfig
C.
outbreakconfig
D.
websecurity config
websecurity advancedconfig
Which Cisco ASA deployment model is used to filter traffic between hosts in the same IP subnet using higher-level protocols without readdressing the network?
A.
routed mode
B.
transparent mode
C.
single context mode
D.
multiple context mode
transparent mode
What is a feature of container orchestration?
A.
ability to deploy Amazon ECS clusters by using the Cisco Container Platform data plane
B.
ability to deploy Amazon EKS clusters by using the Cisco Container Platform data plane
C.
ability to deploy Kubernetes clusters in air-gapped sites
D.
automated daily updates
ability to deploy Kubernetes clusters in air-gapped sites
| Page 24 out of 63 Pages |
| Previous |