Topic 1: Exam Pool A
Which VPN technology can support a multivendor environment and secure traffic between sites?
A.
SSL VPN
B.
GET VPN
C.
FlexVPN
D.
DMVPN
FlexVPN
FlexVPN is an IKEv2-based VPN technology that provides
several benefits beyond traditional site-to-site VPN implementations. FlexVPN is a
standards-based solution that can interoperate with non-Cisco IKEv2implementations.
Therefore FlexVPN can support a multivendor environment. All of the three VPN
technologies support traffic between sites (site-to-site or spoke-to-spoke).
An engineer needs a solution for TACACS+ authentication and authorization for device administration.
The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
A.
Cisco Prime Infrastructure
B.
Cisco Identity Services Engine
C.
Cisco Stealthwatch
D.
Cisco AMP for Endpoints
Cisco Identity Services Engine
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two)
A.
Patch for cross-site scripting.
B.
Perform backups to the private cloud.
C.
Protect against input validation and character escapes in the endpoint.
D.
Install a spam and virus email filter.
E.
Protect systems with an up-to-date antimalware program
Install a spam and virus email filter.
Protect systems with an up-to-date antimalware program
Phishing attacks are the practice of sending fraudulent
communications that appear to come from a reputablesource. It is usually done through email. The goal is to steal sensitive data like credit card and login information,or to install malware on the victim’s machine.
On which part of the IT environment does DevSecOps focus?
A.
application development
B.
wireless network
C.
data center
D.
perimeter network
application development
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
A.
Enable IP Layer enforcement
B.
Activate the Advanced Malware Protection license
C.
Activate SSL decryption.
D.
Enable Intelligent Proxy.
Enable Intelligent Proxy.
Which benefit does DMVPN provide over GETVPN?
A.
DMVPN supports QoS, multicast, and routing, and GETVPN supports only QoS.
B.
DMVPN is a tunnel-less VPN, and GETVPN is tunnel-based.
C.
DMVPN supports non-IP protocols, and GETVPN supports only IP protocols
D.
DMVPN can be used over the public Internet, and GETVPN requires a private network
DMVPN can be used over the public Internet, and GETVPN requires a private network
Refer to the exhibit.
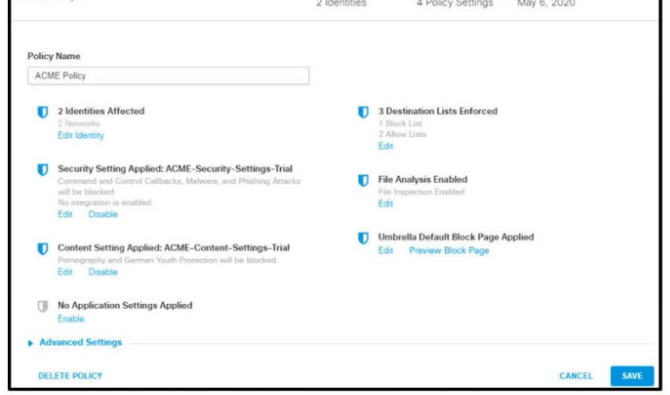
How does Cisco Umbrella manage traffic that is directed toward risky domains?
A.
Traffic is proximed through the intelligent proxy.
B.
Traffic is managed by the security settings and blocked
C.
Traffic is managed by the application settings, unhandled and allowed
D.
Traffic is allowed but logged.
Traffic is managed by the security settings and blocked
Which two application layer preprocessors are used by Firepower Next Generation Intrusion Prevention System? (Choose two)
A.
packet decoder
B.
SIP
C.
modbus
D.
inline normalization
E.
SSL
SIP
SSL
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmcconfig-guidev60/Application_Layer_Preprocessors.html#ID-2244-0000080cFirePower uses many preprocessors, including DNS, FTP/Telnet, SIP, SSL, SMTP, SSH preprocessors.
An organization wants to use Cisco FTD or Cisco ASA devices. Specific URLs must be
blocked from being
accessed via the firewall which requires that the administrator input the bad URL
categories that the
organization wants blocked into the access policy. Which solution should be used to meet
this requirement?
A.
Cisco ASA because it enables URL filtering and blocks malicious URLs by default,
whereas Cisco FTD
does not
B.
Cisco ASA because it includes URL filtering in the access control policy capabilities,
whereas Cisco FTD does not
C.
Cisco FTD because it includes URL filtering in the access control policy capabilities,
whereas Cisco ASA does not
D.
Cisco FTD because it enables URL filtering and blocks malicious URLs by default,
whereas Cisco ASA does not
Cisco FTD because it includes URL filtering in the access control policy capabilities,
whereas Cisco ASA does not
Which RADIUS feature provides a mechanism to change the AAA attributes of a session after it is authenticated?
A.
Authorization
B.
Accounting
C.
Authentication
D.
CoA
CoA
| Page 23 out of 63 Pages |
| Previous |