Topic 1: Exam Pool A
Which capability is exclusive to a Cisco AMP public cloud instance as compared to a private cloud instance?
A.
RBAC
B.
ETHOS detection engine
C.
SPERO detection engine
D.
TETRA detection engine
ETHOS detection engine
Which Cisco Advanced Malware protection for Endpoints deployment architecture is designed to keep data within a network perimeter?
A.
cloud web services
B.
network AMP
C.
private cloud
D.
public cloud
private cloud
Which two preventive measures are used to control cross-site scripting? (Choose two)
A.
Enable client-side scripts on a per-domain basis.
B.
Incorporate contextual output encoding/escaping.
C.
Disable cookie inspection in the HTML inspection engine.
D.
Run untrusted HTML input through an HTML sanitization engine.
E.
Same Site cookie attribute should not be used.
Enable client-side scripts on a per-domain basis.
Incorporate contextual output encoding/escaping.
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
A.
Cisco SDA
B.
Cisco Firepower
C.
Cisco HyperFlex
D.
Cisco Cloudlock
Cisco Cloudlock
A company is experiencing exfiltration of credit card numbers that are not being stored onpremise. The company needs to be able to protect sensitive data throughout the full environment. Which tool should be used to accomplish this goal?
A.
Security Manager
B.
Cloudlock
C.
Web Security Appliance
D.
Cisco ISE
Cloudlock
Cisco Cloudlock is a cloud-native cloud access security broker
(CASB) that helps you move to the cloud safely. It protects your cloud users, data, and
apps. Cisco Cloudlock provides visibility and compliance checks, protects data against
misuse and exfiltration, and provides threat protections against malware like ransomware.
What are two reasons for implementing a multifactor authentication solution such as Duo Security provide to an organization? (Choose two)
A.
flexibility of different methods of 2FA such as phone callbacks, SMS passcodes, and push notifications
B.
single sign-on access to on-premises and cloud applications
C.
integration with 802.1x security using native Microsoft Windows supplicant
D.
secure access to on-premises and cloud applications
E.
identification and correction of application vulnerabilities before allowing access to
resources
flexibility of different methods of 2FA such as phone callbacks, SMS passcodes, and push notifications
secure access to on-premises and cloud applications
Two-factor authentication adds a second layer of security to
your online accounts. Verifying your identity using asecond factor (like your phone or other
mobile device) prevents anyone but you from logging in, even if theyknow your
password.Note: Single sign-on (SSO) is a property of identity and access management that
enables users to securelyauthenticate with multiple applications and websites by logging in
only once with just one set of credentials(username and password). With SSO, the
application or website that the user is trying to access relies on atrusted third party to verify
that users are who they say they are.
Refer to the exhibit.
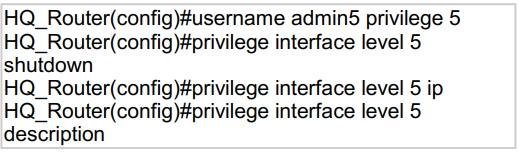
A network administrator configures command authorization for the admin5 user. What is
the admin5 user able to do on HQ_Router after this configuration?
A.
set the IP address of an interface
B.
complete no configurations
C.
complete all configurations
D.
add subinterfaces
complete no configurations
The user “admin5” was configured with privilege level 5. In order
to allow configuration (enter globalconfiguration mode), we must type this
command:(config)#privilege exec level 5 configure terminalWithout this command, this user
cannot do any configuration.Note: Cisco IOS supports privilege levels from 0 to 15, but the
privilege levels which are used by default are privilege level 1 (user EXEC) and level
privilege 15 (privilege EXEC)
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true?
A.
To view bandwidth usage for NetFlow records, the QoS feature must be enabled.
B.
A sysopt command can be used to enable NSEL on a specific interface.
C.
NSEL can be used without a collector configured.
D.
A flow-export event type must be defined under a policy
A flow-export event type must be defined under a policy
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
A.
DMVPN
B.
FlexVPN
C.
IPsec DVTI
D.
GET VPN
GET VPN
https://www.cisco.com/c/dam/en/us/products/collateral/security/groupencrypted-
transport-vpn/GETVPN_DIG_version_2_0_External.pdf
Which functions of an SDN architecture require southbound APIs to enable
communication?
A.
SDN controller and the network elements
B.
management console and the SDN controller
C.
management console and the cloud
D.
SDN controller and the cloud
SDN controller and the network elements
| Page 22 out of 63 Pages |
| Previous |