Topic 1: Exam Pool A
What is the primary benefit of deploying an ESA in hybrid mode?
A.
You can fine-tune its settings to provide the optimum balance between security and
performance for your environment
B.
It provides the lowest total cost of ownership by reducing the need for physical
appliances
C.
It provides maximum protection and control of outbound messages
D.
It provides email security while supporting the transition to the cloud
It provides email security while supporting the transition to the cloud
Cisco Hybrid Email Security is a unique service offering that
facilitates the deployment of your email securityinfrastructure both on premises and in the
cloud. You can change the number of on-premises versus cloudusers at any time
throughout the term of your contract, assuming the total number of users does not
change.This allows for deployment flexibility as your organization’s needs change.
Which policy represents a shared set of features or parameters that define the aspects of a
managed device that are likely to be similar to other managed devices in a deployment?
A.
Group Policy
B.
Access Control Policy
C.
Device Management Policy
D.
Platform Service Policy
Platform Service Policy
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmcconfigguide-
v62/platform_settings_policies_for_managed_devices.htmlTherefore the
answer should be “Platform Settings Policy”, not “Platform Service Policy” but it is the
bestanswer here so we have to choose it.
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is
configuring the
organization’s public cloud to send telemetry using the cloud provider’s mechanisms to a
security device. Which
mechanism should the engineer configure to accomplish this goal?
A.
mirror port
B.
Flow
C.
NetFlow
D.
VPC flow logs
NetFlow
What is the role of an endpoint in protecting a user from a phishing attack?
A.
Use Cisco Stealthwatch and Cisco ISE Integration
B.
Utilize 802.1X network security to ensure unauthorized access to resources
C.
Use machine learning models to help identify anomalies and determine expected
sending behavior
D.
Ensure that antivirus and anti malware software is up to date
Use machine learning models to help identify anomalies and determine expected
sending behavior
In which form of attack is alternate encoding, such as hexadecimal representation, most
often observed?
A.
Smurf
B.
distributed denial of service
C.
cross-site scripting
D.
rootkit exploit
cross-site scripting
ExplanationCross site scripting (also known as XSS) occurs when a web
application gathers malicious data from a user. The data is usually gathered in the form of
a hyperlink which contains malicious content within it. The user will most likely click on this
link from another website, instant message, or simply just reading a web board or email
message.Usually the attacker will encode the malicious portion of the link to the site in HEX
(or other encoding methods) so the request is less suspicious looking to the user when
clicked on.For example the code below is written in hex:
<ahref=javascript:alert('XSS')>Click Here</a>is equivalent to:<a
href=javascript:alert('XSS')>Click Here</a>Note: In the format “&#xhhhh“, hhhh is the code
point in hexadecimal form.
A Cisco ESA network administrator has been tasked to use a newly installed service to
help create policy based on the reputation verdict. During testing, it is discovered that the
Cisco ESA is not dropping files that have an undetermined verdict. What is causing this
issue?
A.
The policy was created to send a message to quarantine instead of drop
B.
The file has a reputation score that is above the threshold
C.
The file has a reputation score that is below the threshold
D.
The policy was created to disable file analysis
The policy was created to disable file analysis
Maybe the “newly installed service” in this Qmentions about
Advanced Malware Protection (AMP) which can be used along with ESA. AMP allows
superior protection across the attack continuum.+ File Reputation – captures a fingerprint
of each file as it traverses the ESA and sends it to AMP’s cloudbased intelligence network
for a reputation verdict. Given these results, you can automatically block malicious files and
apply administrator-defined policy.+ File Analysis – provides the ability to analyze
unknown files that are traversing the ESA. A highly secure sandbox environment enables
AMP to glean precise details about the file’s behavior and to combine that data with
detailed human and machine analysis to determine the file’s threat level. This disposition is
then fed into AMP cloud-based intelligence network and used to dynamically update and
expand the AMP cloud data set for enhanced protection
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
A.
DNS tunneling
B.
DNSCrypt
C.
DNS security
D.
DNSSEC
DNS tunneling
DNS Tunneling is a method of cyber attack that encodes the
data of other programs or protocols in DNSqueries and responses. DNS tunneling often
includes data payloads that can be added to an attacked DNSserver and used to control a
remote server and applications.
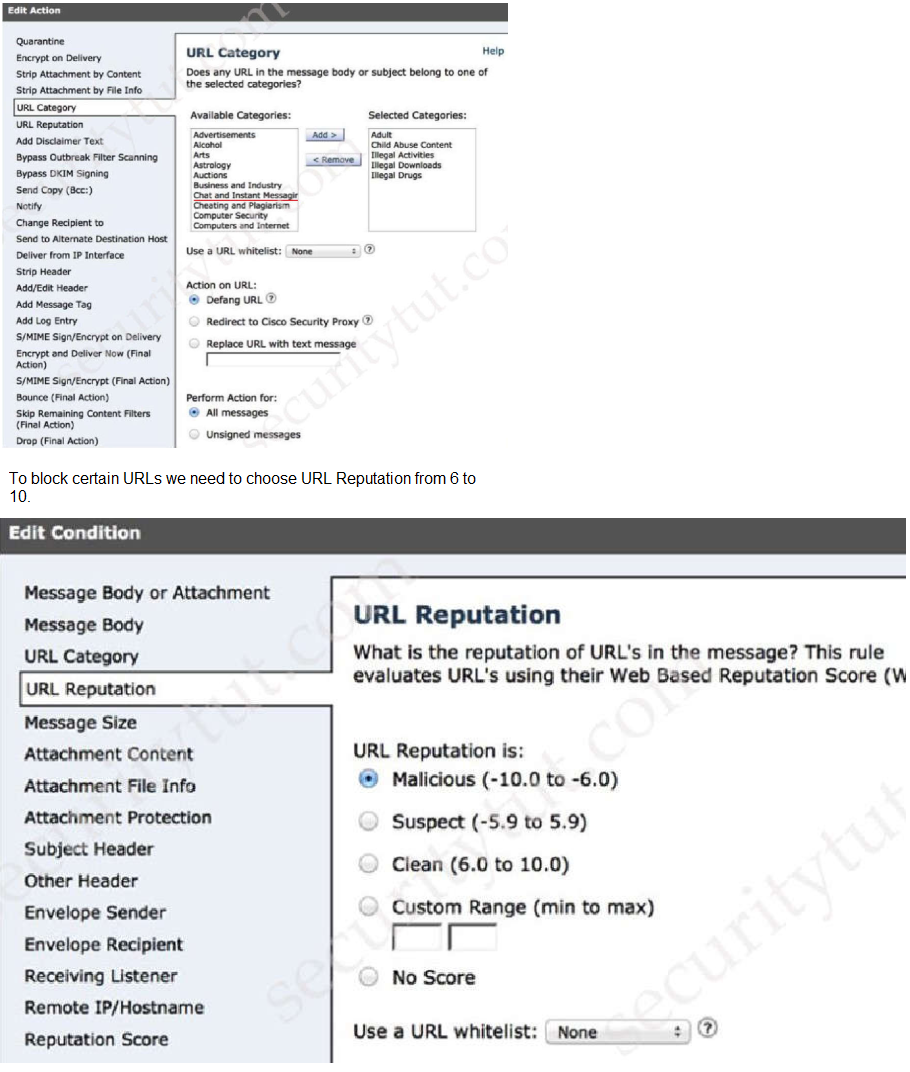
A network administrator is configuring a rule in an access control policy to block certain
URLs and selects the “Chat and Instant Messaging” category. Which reputation score
should be selected to accomplish this goal?
A.
1
B.
3
C.
5
D.
10
10
We choose “Chat and Instant Messaging” category in “URL
Category”:
What provides the ability to program and monitor networks from somewhere other than the
DNAC GUI?
A.
NetFlow
B.
desktop client
C.
ASDM
D.
API
API
Which two capabilities does TAXII support? (Choose two)
A.
Exchange
B.
Pull messaging
C.
Binding
D.
Correlation
E.
Mitigating
Pull messaging
Binding
The Trusted Automated eXchangeof Indicator Information
(TAXII) specifies mechanisms for exchangingstructured cyber threat information between
parties over the network.TAXII exists to provide specific capabilities to those interested in
sharing structured cyber threat information.TAXII Capabilities are the highest level at which TAXII actions can be described. There are three capabilitiesthat this version of TAXII
supports: push messaging, pull messaging, and discovery.Although there is no “binding”
capability in the list but it is the best answer here.
| Page 2 out of 63 Pages |
| Previous |