Topic 2: Exam Pool B
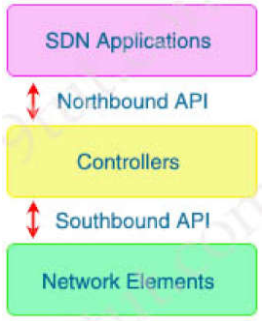
Which type of API is being used when a controller within a software-defined network
architecture dynamically
makes configuration changes on switches within the network?
A.
westbound AP
B.
southbound API
C.
northbound API
D.
eastbound API
southbound API
Southbound APIs enable SDN controllers to
dynamically make changes based on real-time demands andscalability needs.
Which factor must be considered when choosing the on-premise solution over the cloudbased one?
A.
With an on-premise solution, the provider is responsible for the installation and
maintenance of the product, whereas with a cloud-based solution, the customer is
responsible for it
B.
With a cloud-based solution, the provider is responsible for the installation, but the
customer is responsible for the maintenance of the product.
C.
With an on-premise solution, the provider is responsible for the installation, but the
customer is responsible for the maintenance of the product.
D.
With an on-premise solution, the customer is responsible for the installation and
maintenance of the
product, whereas with a cloud-based solution, the provider is responsible for it.
With an on-premise solution, the customer is responsible for the installation and
maintenance of the
product, whereas with a cloud-based solution, the provider is responsible for it.
What is the benefit of installing Cisco AMP for Endpoints on a network?
A.
It provides operating system patches on the endpoints for security.
B.
It provides flow-based visibility for the endpoints network connections.
C.
It enables behavioral analysis to be used for the endpoints.
D.
It protects endpoint systems through application control and real-time scanning
It protects endpoint systems through application control and real-time scanning
With which components does a southbound API within a software-defined network
architecture communicate?
A.
controllers within the network
B.
applications
C.
appliances
D.
devices such as routers and switches
devices such as routers and switches
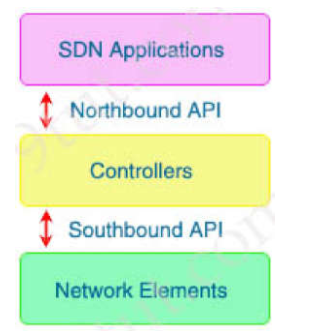
The Southbound API is used to communicate between Controllers and network devices.
Refer to the exhibit.
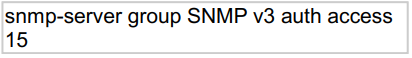
What does the number 15 represent in this configuration?
A.
privilege level for an authorized user to this router
B.
access list that identifies the SNMP devices that can access the router
C.
interval in seconds between SNMPv3 authentication attempts
D.
number of possible failed attempts until the SNMPv3 user is locked out
access list that identifies the SNMP devices that can access the router
The syntax of this command is shown below:
snmp-server group [group-name {v1 | v2c | v3 [auth | noauth | priv]}] [read read-view] [
write write-view] [notify notify-view] [access access-list]
The command above restricts which IP source addresses are allowed to access SNMP
functions on the router. You could restrict SNMP access by simply applying an interface
ACL to block incoming SNMP packets that don’t come from trusted servers. However, this
would not be as effective as using the global SNMP commands shown in this recipe.
Because you can apply this method once for the whole router, it is much simpler than
applying ACLs to block SNMP on all interfaces separately. Also, using interface ACLs
would block not only SNMP packets intended for this router, but also may stop SNMP
packets that just happened to be passing through on their way to some other destination
device.
Which public cloud provider supports the Cisco Next Generation Firewall Virtual?
A.
Google Cloud Platform
B.
Red Hat Enterprise Visualization
C.
VMware ESXi
D.
Amazon Web Services
Amazon Web Services
Which benefit does endpoint security provide the overall security posture of an
organization?
A.
It streamlines the incident response process to automatically perform digital forensics on the endpoint.
B.
It allows the organization to mitigate web-based attacks as long as the user is active in the domain.
C.
It allows the organization to detect and respond to threats at the edge of the network.
D.
It allows the organization to detect and mitigate threats that the perimeter security
devices do not detect.
It allows the organization to detect and mitigate threats that the perimeter security
devices do not detect.
Using Cisco Firepower’s Security Intelligence policies, upon which two criteria is Firepower
block based?
(Choose two)
A.
URLs
B.
protocol IDs
C.
IP addresses
D.
MAC addresses
E.
port numbers
URLs
IP addresses
What is a prerequisite when integrating a Cisco ISE server and an AD domain?
A.
Place the Cisco ISE server and the AD server in the same subnet
B.
Configure a common administrator account
C.
Configure a common DNS server
D.
Synchronize the clocks of the Cisco ISE server and the AD server
Synchronize the clocks of the Cisco ISE server and the AD server
What provides visibility and awareness into what is currently occurring on the network?
A.
CMX
B.
WMI
C.
Prime Infrastructure
D.
Telemetry
Telemetry
https://www.cisco.com/c/dam/en_us/about/doing_business/legal/service_descriptions/docs/
activethreat-analytics-premier.pdf
| Page 18 out of 63 Pages |
| Previous |