Topic 2: Exam Pool B
For Cisco IOS PKI, which two types of Servers are used as a distribution point for CRLs?
(Choose two)
A.
SDP
B.
LDAP
C.
subordinate CA
D.
SCP
E.
HTTP
LDAP
HTTP
Under which two circumstances is a CoA issued? (Choose two)
A.
A new authentication rule was added to the policy on the Policy Service node.
B.
An endpoint is deleted on the Identity Service Engine server.
C.
A new Identity Source Sequence is created and referenced in the authentication policy
D.
An endpoint is profiled for the first time.
E.
A new Identity Service Engine server is added to the deployment with the Administration persona
An endpoint is deleted on the Identity Service Engine server.
An endpoint is profiled for the first time.
ExplanationThe profiling service issues the change of authorization in the
following cases:– Endpoint deleted—When an endpoint is deleted from the Endpoints
page and the endpoint is disconnectedor removed from the network.An exception action is
configured—If you have an exception action configured per profile that leads to anunusual
or an unacceptable event from that endpoint. The profiling service moves the endpoint to
thecorresponding static profile by issuing a CoA.– An endpoint is profiled for the first
time—When an endpoint is not statically assigned and profiled for the first time; for
example, the profile changes from an unknown to a known profile.+ An endpoint identity
group has changed—When an endpoint is added or removed from an endpoint identity
group that is used by an authorization policy.The profiling service issues a CoA when there
is any change in an endpoint identity group, and the endpoint identity group is used in the authorization policy for the following:
Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-
1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010100.html
What is a function of 3DES in reference to cryptography?
A.
It hashes files
B.
It creates one-time use passwords.
C.
It encrypts traffic
D.
It generates private keys
It encrypts traffic
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
A.
Nexus
B.
Stealthwatch
C.
Firepower
D.
Tetration
Tetration
What is the difference between Cross-site Scripting and SQL Injection, attacks?
A.
Cross-site Scripting is an attack where code is injected into a database, whereas SQL
Injection is an attack where code is injected into a browser.
B.
Cross-site Scripting is a brute force attack targeting remote sites, whereas SQL Injection is a social
engineering attack.
C.
Cross-site Scripting is when executives in a corporation are attacked, whereas SQL
Injection is when a
database is manipulated.
D.
Cross-site Scripting is an attack where code is executed from the server side, whereas
SQL Injection is an attack where code is executed from the client side.
Cross-site Scripting is an attack where code is injected into a database, whereas SQL
Injection is an attack where code is injected into a browser.
Answer B is not correct because Cross-site Scripting (XSS) is
not a brute force attack.Answer C is not correct because the statement “Cross-site
Scripting is when executives in a corporation are attacked” is not true. XSS is a client-side
vulnerability that targets other application users.Answer D is not correct because the
statement “Cross-site Scripting is an attack where code is executed from the server side”.
In fact, XSS is a method that exploits website vulnerability by injecting scripts that will run
at client’s side.Therefore only answer A is left. In XSS, an attacker will try to inject his
malicious code (usually malicious links) into a database. When other users follow his links,
their web browsers are redirected to websites whereattackers can steal data from them. In
a SQL Injection, an attacker will try to inject SQL code (via his browser) into forms, cookies,
or HTTP headers that do not use data sanitizing or validation methods of
GET/POSTparameters.Note: The main difference between a SQL and XSS injection attack
is that SQL injection attacks are used to steal information from databases whereas XSS
attacks are used to redirect users to websites where attackers can steal data from them.
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the corporate network. The endpoints must have the corporate antivirus application installed and be running the
latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?
A.
Cisco Identity Services Engine and AnyConnect Posture module
B.
Cisco Stealthwatch and Cisco Identity Services Engine integration
C.
Cisco ASA firewall with Dynamic Access Policies configured
D.
Cisco Identity Services Engine with PxGrid services enabled
Cisco Identity Services Engine and AnyConnect Posture module
Drag and drop the descriptions from the left onto the encryption algorithms on the right.
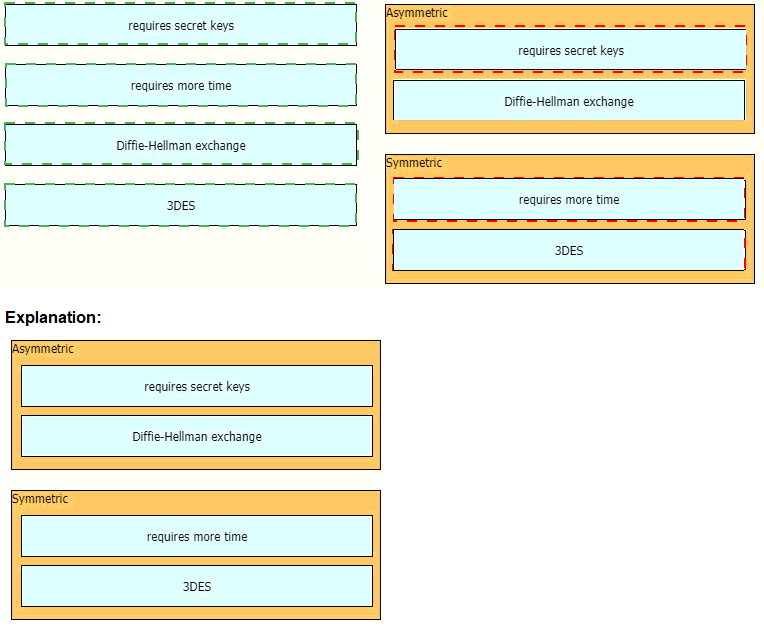
Symmetric encryption uses a single key that needs to be shared among the
people who need to receive the message while asymmetric encryption uses a pair of public
key and a private key to encrypt and decrypt messages when communicating.Asymmetric
encryption takes relatively more time than the symmetric encryption.Diffie Hellman
algorithm is an asymmetric algorithm used to establish a shared secret for a symmetric
keyalgorithm. Nowadays most of the people uses hybrid crypto system i.e, combination of
symmetric andasymmetric encryption. Asymmetric Encryption is used as a technique in key
exchange mechanism to share secret key and after the key is shared between sender and
receiver, the communication will take place using symmetric encryption. The shared secret
key will be used to encrypt the communication.Triple DES (3DES), a symmetric-key
algorithm for the encryption of electronic data, is the successor of DES (Data Encryption
Standard) and provides more secure encryption then DES.Note: Although “requires secret keys” option in this question is a bit unclear but it can only be assigned to Symmetric
algorithm.
Which type of API is being used when a security application notifies a controller within a
software-defined
network architecture about a specific security threat? (Choose two)
A.
westbound AP
B.
southbound API
C.
northbound API
D.
eastbound API
southbound API
northbound API
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
A.
hypervisor
B.
virtual machine
C.
network
D.
application
application
An organization wants to secure users, data, and applications in the cloud. The solution
must be API-based and
operate as a cloud-native CASB. Which solution must be used for this implementation?
A.
Cisco Cloudlock
B.
Cisco Cloud Email Security
C.
Cisco Firepower Next-Generation Firewall
D.
Cisco Umbrella
Cisco Cloudlock
| Page 17 out of 63 Pages |
| Previous |