Topic 2: Exam Pool B
What is a benefit of using Cisco FMC over Cisco ASDM?
A.
Cisco FMC uses Java while Cisco ASDM uses HTML5.
B.
Cisco FMC provides centralized management while Cisco ASDM does not.
C.
Cisco FMC supports pushing configurations to devices while Cisco ASDM does not.
D.
Cisco FMC supports all firewall products whereas Cisco ASDM only supports Cisco ASA
devices
Cisco FMC provides centralized management while Cisco ASDM does not.
Reference: https://www.cisco.com/c/en/us/products/collateral/security/firesightmanagement-
center/datasheetc78-736775.html
What is a capability of Cisco ASA Netflow?
A.
It filters NSEL events based on traffic
B.
It generates NSEL events even if the MPF is not configured
C.
It logs all event types only to the same collector
D.
It sends NetFlow data records from active and standby ASAs in an active standby
failover pair
It filters NSEL events based on traffic
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
A.
authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key
ciscXXXXXXXX
B.
authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX
C.
authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key
ciscXXXXXXXX
D.
secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX
authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key
ciscXXXXXXXX
Configure a Crypto ISAKMP Key
In order to configure a preshared authentication key, enter the crypto isakmp key
command in global configuration mode:
crypto isakmp key cisco123 address 172.16.1.1
https://community.cisco.com/t5/vpn/isakmp-with-0-0-0-0-dmvpn/td-p/4312380
It is a bad practice but it is valid. 172.16.0.0/16 the full range will be accepted as possible
PEER
https://www.examtopics.com/discussions/cisco/view/46191-exam-350-701-topic-1-
question-71-
discussion/#:~:text=Command-reference-is-not-decisive,172.16.1.128-ci
sco123%0ACSR%2D1(config)%23
Testing without a netmask shows that command interpretation has a preference for /16 and
/24. CSR-1(config)#crypto isakmp key cisco123 address 172.16.0.0
CSR-1(config)#do show crypto isakmp key | i cisco
default 172.16.0.0 [255.255.0.0] cisco123
CSR-1(config)#no crypto isakmp key cisco123 address 172.16.0.0
CSR-1(config)#crypto isakmp key cisco123 address 172.16.1.0
CSR-1(config)#do show crypto isakmp key | i cisco
default 172.16.1.0 [255.255.255.0] cisco123
CSR-1(config)#no crypto isakmp key cisco123 address 172.16.1.0
CSR-1(config)#crypto isakmp key cisco123 address 172.16.1.128
CSR-1(config)#do show crypto isakmp key | i cisco default 172.16.1.128 cisco123
CSR-1(config)#
What is provided by the Secure Hash Algorithm in a VPN?
A.
integrity
B.
key exchange
C.
encryption
D.
authentication
integrity
What is a key difference between Cisco Firepower and Cisco ASA?
A.
Cisco ASA provides access control while Cisco Firepower does not.
B.
Cisco Firepower provides identity-based access control while Cisco ASA does not.
C.
Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA
does not.
D.
Cisco ASA provides SSL inspection while Cisco Firepower does not.
Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA
does not.
Refer to the exhibit.
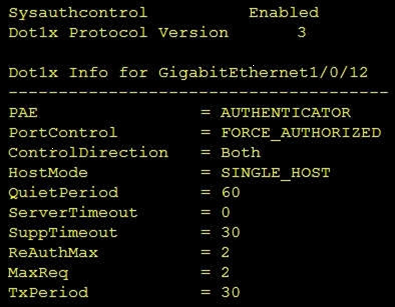
Which command was used to display this output?
A.
show dot1x all
B.
show dot1x
C.
show dot1x all summary
D.
show dot1x interface gi1/0/12
show dot1x all
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for
analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files
which need analysis?
A.
AMP calculates the SHA-256 fingerprint, caches it, and periodically attempts the upload
B.
The file is queued for upload when connectivity is restored
C.
The file upload is abandoned
D.
The ESA immediately makes another attempt to upload the file
The file upload is abandoned
https://www.cisco.com/c/en/us/support/docs/security/email-securityappliance/
118796-technoteesa-00.htmlIn this question, it stated “the network is congested”
(not the file analysis server was overloaded) so theappliance will not try to upload the file again.
A user has a device in the network that is receiving too many connection requests from
multiple machines.
Which type of attack is the device undergoing?
A.
phishing
B.
slowloris
C.
pharming
D.
SYN flood
SYN flood
Which license is required for Cisco Security Intelligence to work on the Cisco Next
Generation Intrusion Prevention System?
A.
control
B.
malware
C.
URL filtering
D.
protect
protect
What is the Cisco API-based broker that helps reduce compromises, application risks, and
data breaches in an environment that is not on-premise?
A.
Cisco Cloudlock
B.
Cisco Umbrella
C.
Cisco AMP
D.
Cisco App Dynamics
Cisco Cloudlock
Cisco Cloudlock is a cloud-native cloud access
security broker (CASB) that helps you move to the cloud safely.It protects your cloud users,
data, and apps. Cisco Cloudlock provides visibility and compliance checks,protects data
against misuse and exfiltration, and provides threat protections against malware like
ransomware.
| Page 15 out of 63 Pages |
| Previous |