Topic 2: Exam Pool B
A Cisco Firepower administrator needs to configure a rule to allow a new application that
has never been seen
on the network. Which two actions should be selected to allow the traffic to pass without
inspection? (Choose
two)
A.
permit
B.
trust
C.
reset
D.
allow
E.
monitor
trust
monitor
Each rule also has an action, which determines
whether you monitor, trust, block, or allow matching traffic.Note: With action “trust”,
Firepower does not do any more inspection on the traffic. There will be no intrusion
protection and also no file-policy on this traffic.
Refer to the exhibit.

An engineer configured wired 802.1x on the network and is unable to get a laptop to
authenticate. Which port configuration is missing?
A.
authentication open
B.
dotlx reauthentication
C.
cisp enable
D.
dot1x pae authenticator
dot1x pae authenticator
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint Protection Platform?
A.
when there is a need for traditional anti-malware detection
B.
when there is no need to have the solution centrally managed
C.
when there is no firewall on the network
D.
when there is a need to have more advanced detection capabilities
when there is a need to have more advanced detection capabilities
Endpoint protection platforms (EPP) prevent
endpoint security threats like known and unknown malware.Endpoint detection and
response (EDR) solutions can detect and respond to threats that your EPP and other
security tools did not catch.EDR and EPP have similar goals but are designed to fulfill
different purposes. EPP is designed to providedevice-level protection by identifying
malicious files, detecting potentially malicious activity, and providing tools for incident
investigation and response.The preventative nature of EPP complements proactive EDR.
EPP acts as the first line of defense, filtering out attacks that can be detected by the
organization’s deployed security solutions. EDR acts as a second layer of protection,
enabling security analysts to perform threat hunting and identify more subtle threats to the
endpoint.Effective endpoint defense requires a solution that integrates the capabilities of
both EDR and EPP to provide protection against cyber threats without overwhelming an
organization’s security team.
Which command enables 802.1X globally on a Cisco switch?
A.
dot1x system-auth-control
B.
dot1x pae authenticator
C.
authentication port-control aut
D.
aaa new-model
dot1x system-auth-control
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which probe must be enabled for this type of profiling to work?
A.
NetFlow
B.
NMAP
C.
SNMP
D.
DHCP
NMAP
http://www.network-node.com/blog/2016/1/2/ise-20-profiling
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from
the left onto the correct definitions on the right.

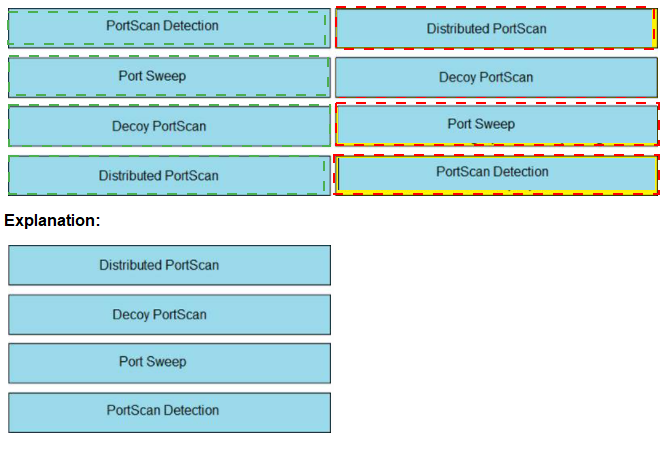
A picture containing table
Description automatically generated
What is a benefit of performing device compliance?
A.
Verification of the latest OS patches
B.
Device classification and authorization
C.
Providing multi-factor authentication
D.
Providing attribute-driven policies
Verification of the latest OS patches
A network engineer is configuring DMVPN and entered the crypto isakmp key
cisc0380739941 address 0.0.0.0 command on hostA. The tunnel is not being established to hostB. What action is needed to authenticate the VPN?
A.
Change isakmp to ikev2 in the command on hostA.
B.
Enter the command with a different password on hostB.
C.
Enter the same command on hostB.
D.
Change the password on hostA to the default password.
Enter the same command on hostB.
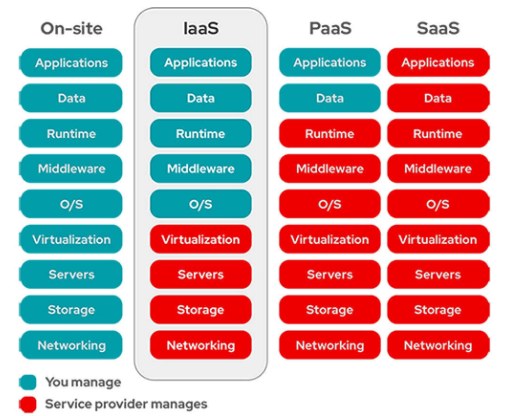
Which two aspects of the cloud PaaS model are managed by the customer but not the
provider? (Choose two)
A.
virtualization
B.
middleware
C.
operating systems
D.
applications
E.
data
applications
data
Customers must manage applications and data in PaaS.
Which type of attack is social engineering?
A.
trojan
B.
phishing
C.
malware
D.
MITM
phishing
Phishing is a form of social engineering. Phishing attacks use
email or malicious web sites to solicit personal,often financial, information. Attackers may send email seemingly from a reputable credit card company orfinancial institution that requests account information, often suggesting that there is a problem.
| Page 11 out of 63 Pages |
| Previous |