Refer to the exhibit.
A network operator needs to shut down interface Gi0/0/0/2 for maintenance. What occurs
to the interface states of Gi0/0/0/0 and Gi0/0/0/1?
A.
Gi0/0/0/1 and Gi0/0/0/0 become active
B.
Gi0/0/0/1 and Gi0//0/0 remains standby
C.
Gi0/0/0/0 becomes active. Gi0/00/1 remains standby
D.
Gi0/0/0/1 becomes active Gi0/0/0/0 remains standby
Gi0/0/0/0 becomes active. Gi0/00/1 remains standby
Refer to the exhibit:
Which two statements about the ISIS topology are true? (Choose two.)
A.
All four routers are operating as Level 1 routers only.
B.
All four routers are operating as Level 2 routers only.
C.
All four routers are operating as Level 1-2 routers.
D.
R1 and R2 are Level 2 neighbors.
E.
R1 and R4 are Level 2 neigh
All four routers are operating as Level 1-2 routers.
R1 and R2 are Level 2 neighbors.
Refer to the exhibit.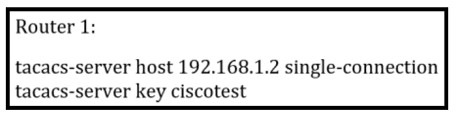
What is the result of this configuration?
A.
Router 1 opens and closes a TCP connection to the TACACS+ server every time a user requires authorization.
B.
Router 1 and the TACACS+ server maintain one open connection between them only
when network administrator is accessing the router with password ciscotest.
C.
Router 1 and the TACACS+ server maintain one open connection between them.
D.
Router 1 opens and closes a TCP connection to the TACACS+ server every time a user
requires authentication
Router 1 and the TACACS+ server maintain one open connection between them only
when network administrator is accessing the router with password ciscotest.
Which component is similar to an EVPN instance?
A.
MPLS label
B.
IGP router ID
C.
VRF
D.
router distinguisher
VRF
While implementing TTL security, an engineer issues the PE(config-router-af)#neighbor
2.2.2.2 ttl-security hops 2 command. After issuing this command, which BGP packets does
the PE accept?
A.
from 2.2.2.2, with a TTL of less than 2
B.
to 2.2.2.2, with a TTL of less than 253
C.
from 2.2.2.2, with a TTL of 253 or more
D.
to 2.2.2.2, with a TTL of 2 or more
from 2.2.2.2, with a TTL of 253 or more
Refer to the exhibit
A network administrator wants to enhance the security for SNMP for this configuration.
Which action can the network administrator implement?
A.
Re-configure to use SNMPv2 with MD5 authentication
B.
Add a community string to the existing entry
C.
Re-configure to use SNMPv3.
D.
Maintain the configuration but switch to an encrypted password for device access
through SSH
Re-configure to use SNMPv3.
Refer to the exhibit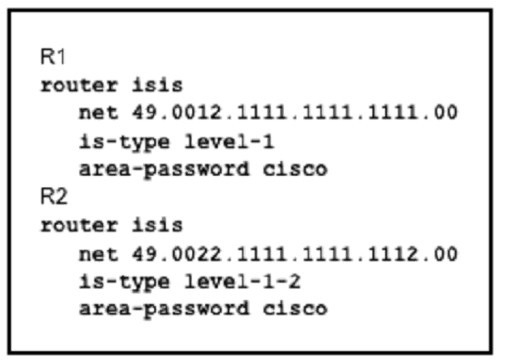
Which effect of this configuration is true?
A.
The two routers fail to form a neighbor relationship because their system IDs are
different.
B.
The two routers successfully form a neighbor relationship
C.
The two routers fail to form a neighbor relationship because the authentication
configuration is missing
D.
The two routers fail to form a neighbor relationship because they have different ISI
The two routers successfully form a neighbor relationship
Refer to the exhibit.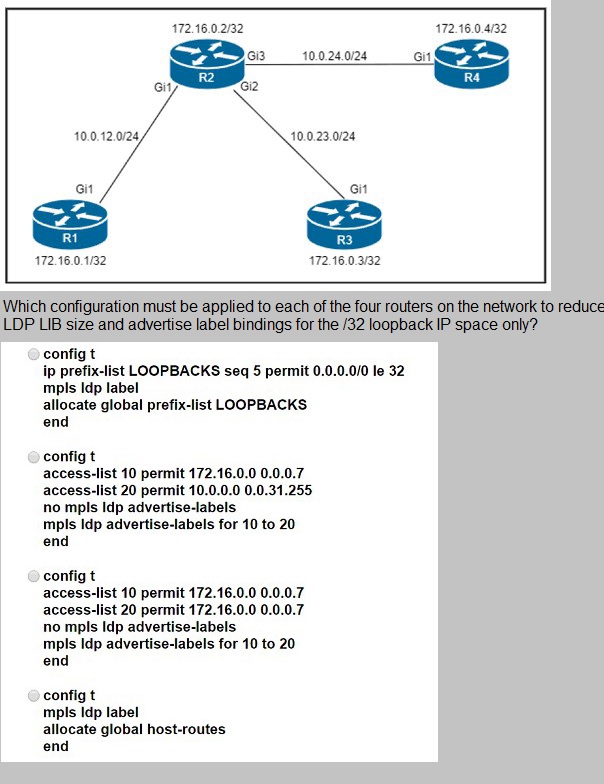
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
Refer to the exhibit: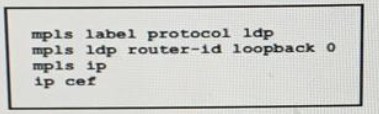
A network operator working for service provider with an employee id 3715 15:021 applied
this configuration to a router.
Which additional step should the engineer use to enable LDP?
A.
Disable Cisco Express Forwarding globally
B.
Delete the static router ID
C.
Enable MPLS LDP on the interface
D.
Configure the both keyword to enable LDP globally
Enable MPLS LDP on the interface
Refer to the exhibit.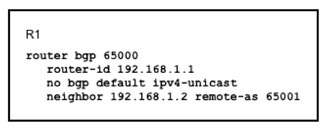
Which task completes the configuration?
A.
Specify the maximum number of prefixes that R1 receives from neighbor 192.168.1.2.
B.
Specify the source interface in the neighbor statement.
C.
Specify the activate neighbor 192.168.1.2 under the IPv4 address family.
D.
Specify the local-as value in the neighbor statement
Specify the activate neighbor 192.168.1.2 under the IPv4 address family.
| Page 7 out of 38 Pages |
| Previous |