Refer to the exhibit:
What is the URL used for with REST API?
A.
It is used to contact a URL filter to determine the efficacy of a web address
B.
It is used to send a TACACS+ authentication request to a server
C.
It is used to send a message to the APIC to perform an operation on a managed object
or class operator
D.
It is used to initiate an FTP session to save a running configuration of a device
It is used to send a message to the APIC to perform an operation on a managed object
or class operator
Which MPLS design attribute can you use to provide Internet access to a major customer
through a separate dedicated VPN?
A.
The customer that needs the Internet access service is assigned to the same RTs as the
Internet gateway
B.
The Internet gateway inserts the full Internet BGP routing table into the Internet access
VPN
C.
The Internet gateway router is connected as a PE router to the MPLS backbone
D.
The CE router supports VRF-Ute and the full BGP routing table.
The customer that needs the Internet access service is assigned to the same RTs as the
Internet gateway
Refer to the exhibit: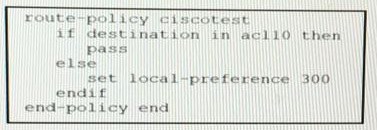
A network engineer is implementing a BGP routing policy.
Which effect of this configuration is true?
A.
All traffic that matches acl10 is allowed without any change to its local-preference
B.
All traffic that matches acl10 is dropped without any change to its local-preference
C.
If traffic matches acl10, it is allowed and its local-preference is set to 300
D.
All traffic is assigned a local-preference of 30O regardless of its destination
All traffic that matches acl10 is allowed without any change to its local-preference
What are two factors to consider when implementing NSR High Availability on an MPLS PE
router? (Choose two.)
A.
It consumes more memory and CPU resources than NSF
B.
It operates normally without NSR support on the PE peers.
C.
It requires all PE-CE sessions to support NSR
D.
It requires routing protocol extensions
E.
It cannot sync state information across redundant RPs
It consumes more memory and CPU resources than NSF
It operates normally without NSR support on the PE peers.
Refer to the exhibit.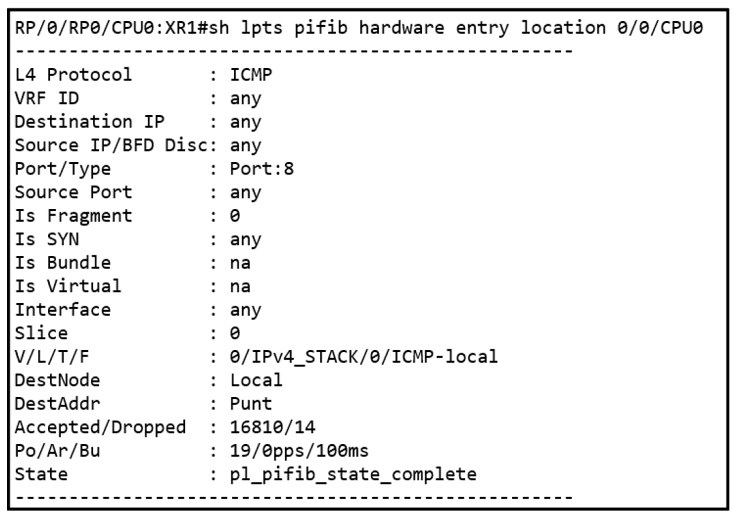
While troubleshooting the network, a network operator with an employee id: 3812:12:993 is
trying to ping XR1. Which result should the operator expect when trying to ping to an XR1
local address?
A.
ICMP traffic works at a policed rate of 19 bytes per second every 100 ms
B.
All ICMP traffic responds successfully.
C.
All ICMP traffic is dropped.
D.
ICMP traffic works at a policed rate of 19 packets every 100 ms.
All ICMP traffic responds successfully.
After you analyze your network environment, you decide to implement a full separation
model for Internet access and MPLS L3VPN services For which reason do you make this
decision?
A.
It enables you to choose whether to separate or centralize each individual service.
B.
It is easier to manage a system in which services are mixed
C.
It requires only one edge router
D.
It enables EGP and IGP to operate independently
It enables EGP and IGP to operate independently
Which service is a VNF role?
A.
Compute
B.
Network
C.
Firewall
D.
Storage
Network
While implementing TTL security, you issue the PE(config-router-af)#neighbor 2.2.2.2 ttlsecurity
hops 2 command.
After you issue this command, which BGP packets does the PE accept?
A.
from 2.2.2.2, with a TTL ol 253 Of more
B.
from 2.2.2.2, with a TTL of less than 2
C.
to 2.2.2.2, with a TTL of less than 253
D.
to 2.2.2.2, with a TTL of 2 or more
from 2.2.2.2, with a TTL ol 253 Of more
Refer to the exhibit.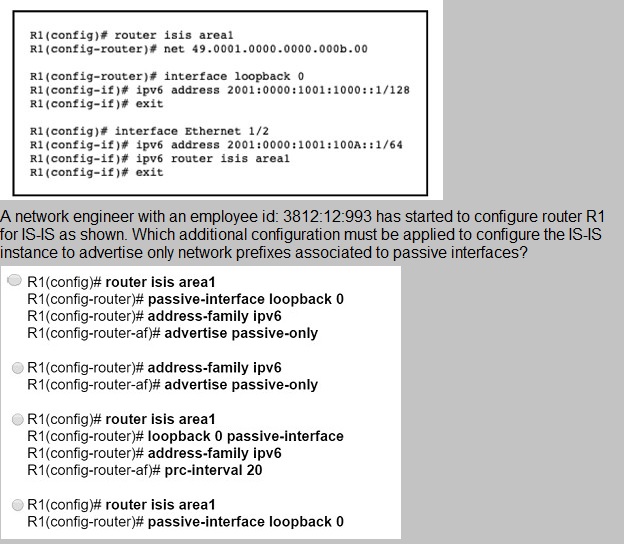
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
Refer to the exhibit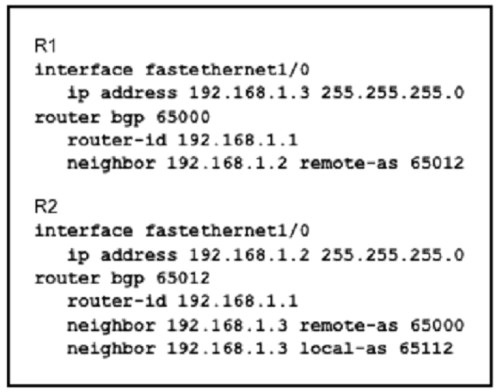
Assume all other configurations are correct and the network is otherwise operating
normally. Which conclusion can you draw about the neighbor relationship between routers
R1 and R2?
A.
The neighbor relationship will be up only if the two devices have activated the correct
neighbor relationships under the IPv4 address family
B.
The neighbor relationship is down because R1 believes R2 is in AS 65012.
C.
The neighbor relationship is up
D.
The neighbor relationship is down because the loco I-as value for R2 is missing in the
R1 neighbor statement
The neighbor relationship is down because R1 believes R2 is in AS 65012.
| Page 10 out of 38 Pages |
| Previous |