Which two uses of the YANG data modeling language are true? (Choose two)
A.
It can be used to shape slats data of network elements
B.
It can be used to access a device by HTTP
C.
It can be used to model the configuration used by NETCONF operations
D.
It can be used to replace the OSI model for troubleshooting
E.
It can be used to replace RESTCONF as a mechanism to install and manipulate
configuration
It can be used to shape slats data of network elements
It can be used to access a device by HTTP
Refer to the exhibit.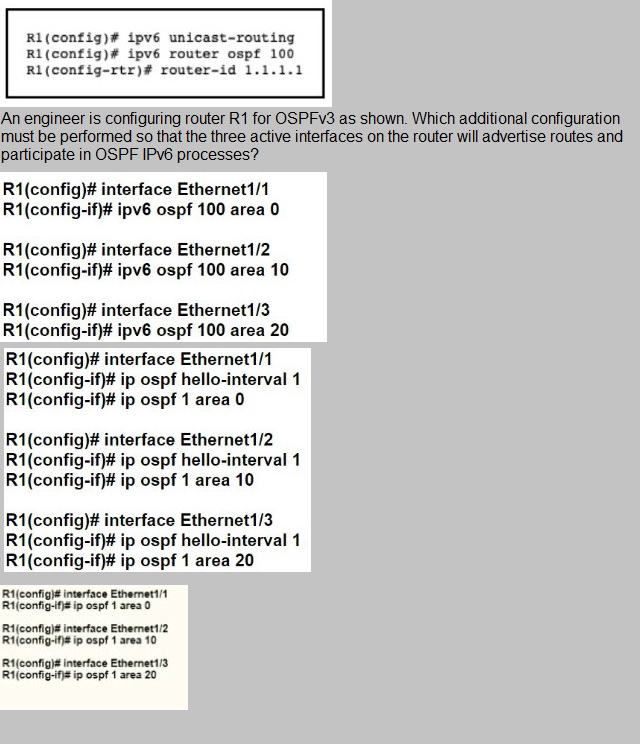
Answer: A
Which regular expression query modifier function indicates the start of a string?
A.
^
B.
[^]
C.
+
D.
$
^
Which control plane protocol is used between Cisco SD-WAN routers and vSmart
controllers?
A.
OTCP
B.
OMP
C.
UDP
D.
BGP
OMP
An network engineer is deploying VRF on ASBR router R1. The interface must have
connectivity over an MPLS VPN inter-AS Option AB network. Which configuration must the
engineer apply on the router to accomplish this task?
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
Which statement about Network Services Orchestrator (NSO) is true?
A.
It is used only in service provider environments
B.
It can be used only with XML coding
C.
It uses YANG modeling language to automate devices
D.
It must use SDN as an overlay for addressing
It uses YANG modeling language to automate devices
Which utility can you use to locate MPLS faults?
A.
MPLS traceroute
B.
EEM
C.
MPLS LSP ping
D.
QoS
MPLS LSP ping
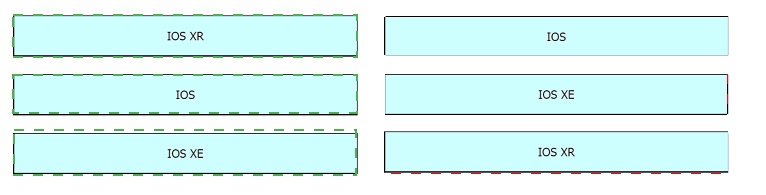
Drag and drop the OSs from the left onto the correct deceptions on the right.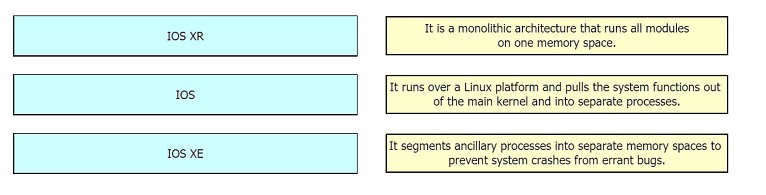
How does model-driven telemetry use YANG?
A.
to reset network devices that malfunction
B.
to set informs and traps on clients to report back to a centralized server
C.
to subscribe to data that is streamed from a device
D.
to poll network devices on a 30-minute interval
to subscribe to data that is streamed from a device

BGPsec is implemented on R1. R2. R3. and R4 BGP peering is established between
neighboring autonomous systems Which statement about implementation is true?
A.
BGP updates from the eBGP peers are appended with an additional AS path value that
is statically set by the domain administrator
B.
BGP updates from the iBGP peers are appended with a community of local-as
C.
BGP updates from the all BGP peers are appended with a community of no export
D.
BGP updates from the eBGP peers are appended with a BGPsec attribute sequence
that includes a public key hash and digital signature
BGP updates from the eBGP peers are appended with a BGPsec attribute sequence
that includes a public key hash and digital signature