Topic 1: Exam Pool A
What is a characteristic of a next-generation firewall?
A.
only required at the network perimeter
B.
required in each layer of the network
C.
filters traffic using Layer 3 and Layer 4 information only
D.
provides intrusion prevention
provides intrusion prevention
Explanation:
The feature set for NGFWs build upon traditional firewall features by including critical security functions like intrusion prevention, VPN, and anti-virus, and even encrypted web traffic inspection to help prevent packets containing malicious content from entering the network.
Refer to exhibit.
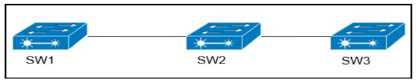
VLANs 50 and 60 exist on the trunk links between all switches All access ports on SW3 are configured for VLAN 50 and SW1 is the VTP server Which command ensures that SW3 receives frames only from VLAN 50?
A.
SW1 (config)#vtp pruning
B.
SW3(config)#vtp mode transparent
C.
SW2(config)=vtp pruning
D.
SW1 (config >»vtp mode transparent
SW1 (config)#vtp pruning
Explanation: SW3 does not have VLAN 60 so it should not receive traffic for this VLAN (sent from SW2).
Therefore we should configure VTP Pruning on SW3 so that SW2 does not forward VLAN 60 traffic to SW3. Also notice that we need to configure pruning on SW1 (the VTP Server), not SW2.
What is used to perform OoS packet classification?
A.
the Options field in the Layer 3 header
B.
the Type field in the Layer 2 frame
C.
the Flags field in the Layer 3 header
D.
the TOS field in the Layer 3 header
the TOS field in the Layer 3 header
Explanation: Type of service, when we talk about PACKET, means layer 3
Which method should an engineer use to deal with a long-standing contention issue between any two VMs on the same host?
A.
Adjust the resource reservation limits
B.
Live migrate the VM to another host
C.
Reset the VM
D.
Reset the host
Adjust the resource reservation limits
What is the function of a VTEP in VXLAN?
A.
provide the routing underlay and overlay for VXLAN headers
B.
dynamically discover the location of end hosts in a VXLAN fabric
C.
encapsulate and de-encapsulate traffic into and out of the VXLAN fabric
D.
statically point to end host locations of the VXLAN fabric
encapsulate and de-encapsulate traffic into and out of the VXLAN fabric
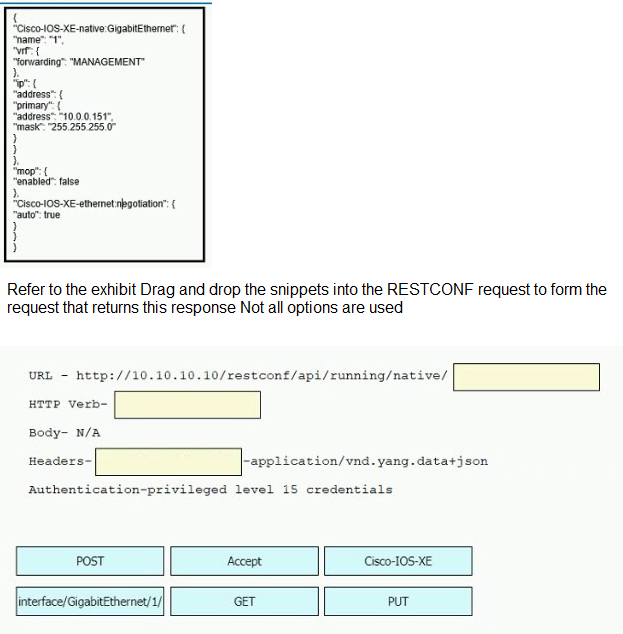

What does the cisco DNA REST response indicate?
A.
Cisco DNA Center has the Incorrect credentials for cat3850-1
B.
Cisco DNA Center is unable to communicate with cat9000-1
C.
Cisco DNA Center has the incorrect credentials for cat9000-1
D.
Cisco DNA Center has the Incorrect credentials for RouterASR-1
Cisco DNA Center has the incorrect credentials for cat9000-1
What is one benefit of implementing a VSS architecture?
A.
It provides multiple points of management for redundancy and improved support
B.
It uses GLBP to balance traffic between gateways.
C.
It provides a single point of management for improved efficiency.
D.
It uses a single database to manage configuration for multiple switches
It provides a single point of management for improved efficiency.
Explanation: Support Virtual Switching System (VSS) to provide resiliency, and increased operational efficiency with a single point of management;
VSS increases operational efficiency by simplifying the network, reducing switch management overhead by at least 50 percent. – Single configuration file and node to manage. Removes the need to configure redundant switches twice with identical policies.
Refer to the exhibit.

A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
Explanation: With BGP, we must advertise the correct network and subnet mask in the “network” command (in this case network 10.1.1.0/24 on R1 and network 10.2.2.0/24 on R2). BGP is very strict in the routing advertisements. In other words, BGP only advertises the network which exists exactly in the routing table. In this case, if you put the command “network x.x.0.0 mask 255.255.0.0” or “network x.0.0.0 mask 255.0.0.0” or “network x.x.x.x mask 255.255.255.255” then BGP will
not advertise anything.
It is easy to establish eBGP neighborship via the direct link. But let’s see what are required when we want to establish eBGP neighborship via their loopback interfaces. We will need two commands:
+ the command “neighbor 10.1.1.1 ebgp-multihop 2” on R1 and “neighbor 10.2.2.2 ebgpmultihop 2” on R1. This command increases the TTL value to 2 so that BGP updates can reach the BGP neighbor which is two hops away.
+ Answer ‘R1 (config) #router bgp 1
R1 (config-router) #neighbor 192.168.10.2 remote-as 2
R1 (config-router) #network 10.1.1.0 mask 255.255.255.0
R2 (config) #router bgp 2
R2 (config-router) #neighbor 192.168.10.1 remote-as 1
R2 (config-router) #network 10.2.2.0 mask 255.255.255.0
Quick Wireless Summary
Cisco Access Points (APs) can operate in one of two modes: autonomous or lightweight
+ Autonomous: self-sufficient and standalone. Used for small wireless networks.
+ Lightweight: A Cisco lightweight AP (LAP) has to join a Wireless LAN Controller (WLC) to function.
LAP and WLC communicate with each other via a logical pair of CAPWAP tunnels.
– Control and Provisioning for Wireless Access Point (CAPWAP) is an IETF standard for control messaging for setup, authentication and operations between APs and WLCs. CAPWAP is similar to LWAPP except the following differences:
+CAPWAP uses Datagram Transport Layer Security (DTLS) for authentication and encryption to protect traffic between APs and controllers. LWAPP uses AES.
+ CAPWAP has a dynamic maximum transmission unit (MTU) discovery mechanism.
+ CAPWAP runs on UDP ports 5246 (control messages) and 5247 (data messages) An LAP operates in one of six different modes:
+ Local mode (default mode): measures noise floor and interference, and scans for intrusion detection (IDS) events every 180 seconds on unused channels
+ FlexConnect, formerly known as Hybrid Remote Edge AP (H-REAP), mode: allows data traffic to be switched locally and not go back to the controller. The FlexConnect AP can perform standalone client authentication and switch VLAN traffic locally even when it’s disconnected to the WLC (Local Switched). FlexConnect AP can also tunnel (via CAPWAP) both user wireless data and control traffic to a centralized WLC (Central Switched).
+ Monitor mode: does not handle data traffic between clients and the infrastructure. It acts like a sensor for location-based services (LBS), rogue AP detection, and IDS
+ Rogue detector mode: monitor for rogue APs. It does not handle data at all.
+ Sniffer mode: run as a sniffer and captures and forwards all the packets on a particular channel to a remote machine where you can use protocol analysis tool (Wireshark, Airopeek, etc) to review the packets and diagnose issues. Strictly used for troubleshooting purposes.
+ Bridge mode: bridge together the WLAN and the wired infrastructure together.
Mobility Express is the ability to use an access point (AP) as a controller instead of a real WLAN controller. But this solution is only suitable for small to midsize, or multi-site branch locations where you might not want to invest in a dedicated WLC. A Mobility Express WLC can support up to 100 Aps.
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:

Which two statements does the engineer use to explain these values to the customer?
(Choose two)
A.
The signal strength at location C is too weak to support web surfing
B.
Location D has the strongest RF signal strength
C.
The RF signal strength at location B is 50% weaker than location A
D.
The signal strength at location B is 10 dB better than location C
E.
The RF signal strength at location C is 10 times stronger than location B
The RF signal strength at location B is 50% weaker than location A
The RF signal strength at location C is 10 times stronger than location B
| Page 7 out of 84 Pages |
| Previous |