Topic 1: Exam Pool A
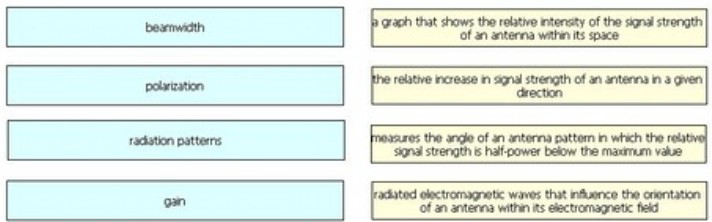
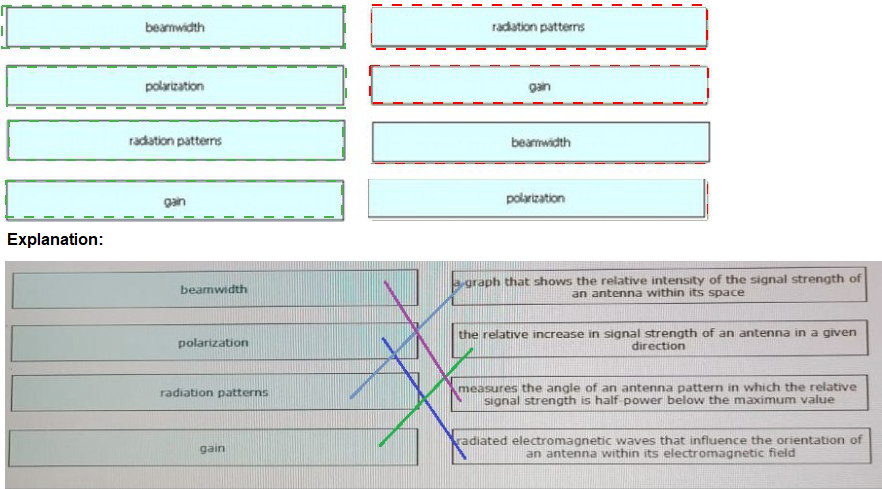
Drag and drop the wireless elements on the left to their definitions on the right.

Refer to the exhibit. An engineer must create a script that appends the output of the show process cpu sorted command to a file.
A.
action 4.0 syslog command “show process cpu sorted | append flash:high-cpu-file”
B.
action 4.0 publish-event “show process cpu sorted | append flash:high-cpu-file”
C.
action 4.0 ens-event “show process cpu sorted | append flash:high-cpu-file”
D.
action 4.0 cli command “show process cpu sorted | append flash:high-cpu-file”
action 4.0 cli command “show process cpu sorted | append flash:high-cpu-file”
Which benefit is offered by a cloud infrastructure deployment but is lacking in an onpremises deployment?
A.
efficient scalability
B.
virtualization
C.
storage capacity
D.
supported systems
efficient scalability
Refer to the exhibit.
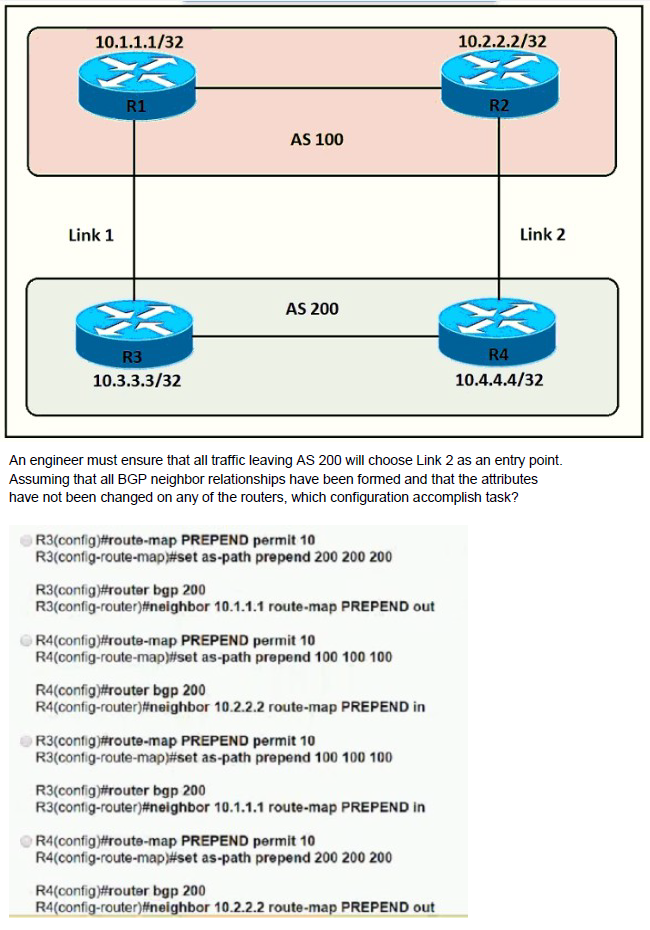
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
Explanation: R3 advertises BGP updates to R1 with multiple AS 100 so R3 believes the path to reach AS 200 via R3 is farther than R2 so R3 will choose R2 to forward traffic to AS 200.
When using TLS for syslog, which configuration allows for secure and reliable transportation of messages to its default port?
A.
logging host 10.2.3.4 vrf mgmt transport tcp port 6514
B.
logging host 10.2.3.4 vrf mgmt transport udp port 6514
C.
logging host 10.2.3.4 vrf mgmt transport tcp port 514
D.
logging host 10.2.3.4 vrf mgmt transport udp port 514
logging host 10.2.3.4 vrf mgmt transport tcp port 6514
Explanation: The TCP port 6514 has been allocated as the default port for syslog over Transport Layer Security (TLS).
Reference: https://tools.ietf.org/html/rfc5425
What is a characteristic of MACsec?
A.
802.1AE provides encryption and authentication services
B.
802.1AE is bult between the host and switch using the MKA protocol, which negotiates encryption keys based on the master session key from a successful 802.1X session
C.
802.1AE is bult between the host and switch using the MKA protocol using keys
generated via the Diffie-Hellman algorithm (anonymous encryption mode)
D.
802.1AE is negotiated using Cisco AnyConnect NAM and the SAP protocol
802.1AE is bult between the host and switch using the MKA protocol, which negotiates encryption keys based on the master session key from a successful 802.1X session
Explanation: MACsec, defined in 802.1AE, provides MAC-layer encryption over wired networks by using out-of-band methods for encryption keying. The MACsec Key Agreement (MKA) Protocol provides the required session keys and manages the required encryption keys. MKA and MACsec are implemented after successful authentication using the 802.1x Extensible Authentication Protocol (EAP-TLS) or Pre Shared Key (PSK) framework.
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9300/software/release/16-9/configuration_guide/sec/b_169_sec_9300_cg/macsec_encryption.html

Refer to the exhibit. Which action completes the configuration to achieve a dynamic continuous mapped NAT for all users?
A.
Configure a match-host type NAT pool
B.
Reconfigure the pool to use the 192.168 1 0 address range
C.
Increase the NAT pool size to support 254 usable addresses
D.
Configure a one-to-one type NAT pool
Increase the NAT pool size to support 254 usable addresses
Running the script causes the output in the exhibit. Which change to the first line of the script resolves the error?
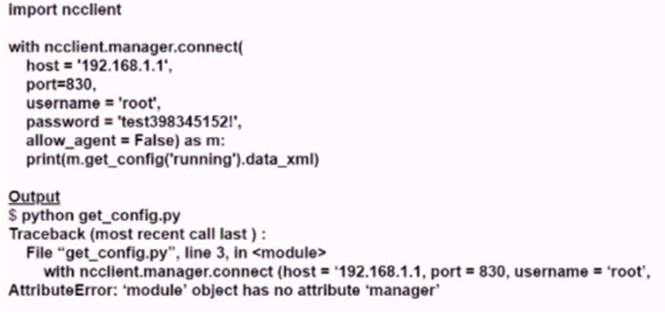
A.
from ncclient import
B.
import manager
C.
from ncclient import*
D.
import ncclient manager
from ncclient import*
Refer to the exhibit.
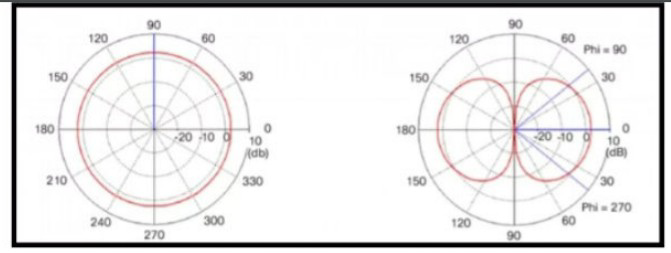
Which type of antenna is show on the radiation patterns?
A.
Dipole
B.
Yagi
C.
Patch
D.
Omnidirectional
Dipole
Which two methods are used to reduce the AP coverage area? (Choose two)
A.
Reduce channel width from 40 MHz to 20 MHz
B.
Disable 2.4 GHz and use only 5 GHz.
C.
Reduce AP transmit power
D.
Increase minimum mandatory data rate
E.
Enable Fastlane
Reduce AP transmit power
Increase minimum mandatory data rate
| Page 6 out of 84 Pages |
| Previous |