Topic 1: Exam Pool A
Refer to the exhibit.

A network engineer must simplify the IPsec configuration by enabling IPsec over GRE using IPsec profiles. Which two configuration changes accomplish this? (Choose two).
A.
Create an IPsec profile, associate the transform-set ACL, and apply the profile to the tunnel interface.
B.
Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4.
C.
Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL.
D.
Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface.
E.
Remove the crypto map and modify the ACL to allow traffic between 10.10.0.0/24 to 10.20.0.0/24.
Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL.
Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface.
A company plans to implement intent-based networking in its campus infrastructure. Which design facilities a migrate from a traditional campus design to a programmer fabric designer?
A.
Layer 2 access
B.
three-tier
C.
two-tier
D.
routed access
two-tier
A network engineer configures BGP between R1 and R2. Both routers use BGP peer group CORP and are set up to use MD5 authentication. This message is logged to the console of router R1:

Which two configuration allow peering session to from between R1 and R2? Choose two.)
A.
R1(config-router)#neighbor 10.10.10.1 peer-group CORP R1(config-router)#neighbor CORP password Cisco
B.
R2(config-router)#neighbor 10.120.10.1 peer-group CORP R2(config-router)#neighbor CORP password Cisco
C.
R2(config-router)#neighbor 10.10.10.1 peer-group CORP R2(config-router)#neighbor PEER password Cisco
D.
R1(config-router)#neighbor 10.120.10.1 peer-group CORP R1(config-router)#neighbor CORP password Cisco
E.
R2(config-router)#neighbor 10.10.10.1 peer-group CORP R2(config-router)#neighbor CORP password Cisco
R1(config-router)#neighbor 10.10.10.1 peer-group CORP R1(config-router)#neighbor CORP password Cisco
R2(config-router)#neighbor 10.120.10.1 peer-group CORP R2(config-router)#neighbor CORP password Cisco
Refer to the exhibit.

A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C
Explanation: We cannot filter traffic that is originated from the local router (R3 in this case) so we can only configure the ACL on R1 or R2. “Weekend hours” means from Saturday morning through Sunday night so we have to configure: “periodic weekend 00:00 to 23:59”.
Note: The time is specified in 24-hour time (hh:mm), where the hours range from 0 to 23 and the minutes range from 0 to 59.
An engineer has deployed a single Cisco 5520 WLC with a management IP address of 172.16.50.5/24. The engineer must register 50 new Cisco AIR-CAP2802I-E-K9 access points to the WLC using DHCP option 43. The access points are connected to a switch in VLAN 100 that uses the 172.16.100.0/24 subnet. The engineer has configured the DHCP scope on the switch as follows:

The access points are failing to join the wireless LAN controller. Which action resolves the issue?
A.
configure option 43 Hex F104.AC10.3205
B.
configure option 43 Hex F104.CA10.3205
C.
configure dns-server 172.16.50.5
D.
configure dns-server 172.16.100.1
configure option 43 Hex F104.AC10.3205
Explanation:
The Option 43 hexadecimal string is assembled as a sequence of the TLV values for the Option 43 suboption: Type + Length + Value. Type is always the suboption code 0xf1. Length is the number of controller management IP addresses times 4 in hex. Value is the IP address of the controller listed sequentially in hex.
On this question, there is 1 controller with management interface IP addresses 172.16.50.5/24. The type is 0xf1. The length is 1 * 4 = 8 = 0x04. The mgmt IP addresses 172.16.50.5 translate to ac.10.32.05 (0xac103205). When the string is assembled, it yields f108c0a80a05c0a80a14. The Cisco IOS command that is added to the DHCP scope is: option 43 hex f104ac103205
Which configuration restricts the amount of SSH that a router accepts 100 kbps?
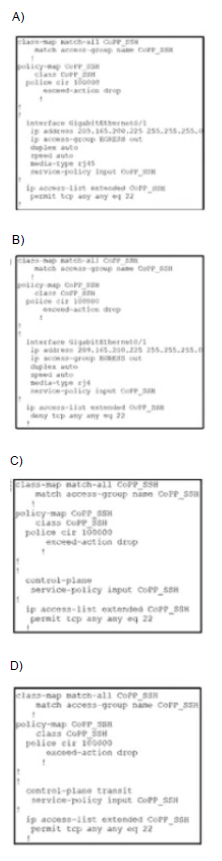
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C
Explanation:
CoPP protects the route processor on network devices by treating route processor resources as a separate entity with its own ingress interface (and in some implementations, egress also). CoPP is used to police traffic that is destined to the route processor of the router such as:
+ routing protocols like OSPF, EIGRP, or BGP.
+ Gateway redundancy protocols like HSRP, VRRP, or GLBP.
+ Network management protocols like telnet, SSH, SNMP, or RADIUS.
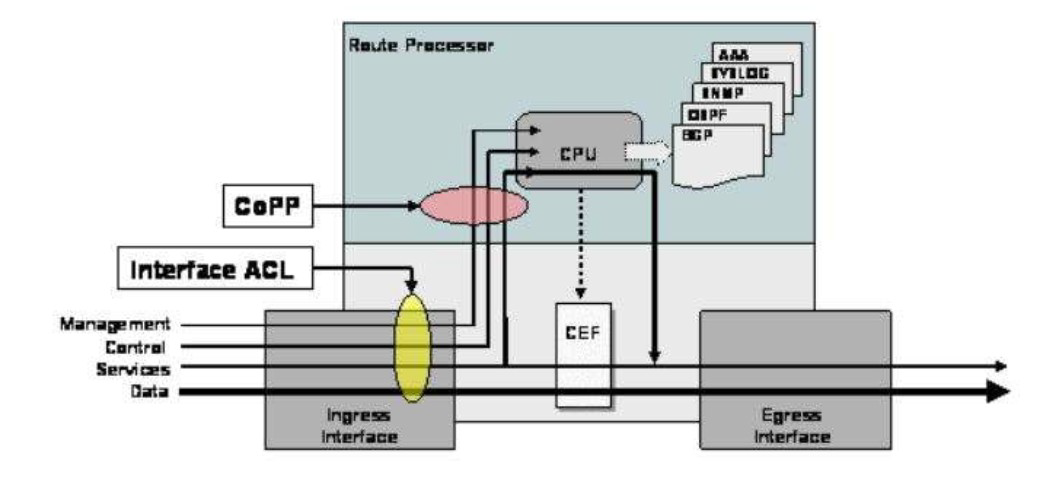
Therefore we must apply the CoPP to deal with SSH because it is in the management plane. CoPP must be put under “control-plane” command.
While configuring an IOS router for HSRP with a virtual IP of 10 1.1.1. an engineer sees this log message.

Which configuration change must the engineer make?
A.
Change the HSRP group configuration on the local router to 1.
B.
Change the HSRP virtual address on the local router to 10.1.1.1.
C.
Change the HSRP virtual address on the remote router to 10.1.1.1.
D.
Change the HSRP group configuration on the remote router to 1.
Change the HSRP virtual address on the local router to 10.1.1.1.
Wireless users report frequent disconnections from the wireless network. While troubleshooting a network engineer finds that after the user a disconnect, the connection re-establishes automatically without any input required. The engineer also notices these message logs.

Which action reduces the user impact?
A.
increase the AP heartbeat timeout
B.
increase BandSelect
C.
enable coverage hole detection
D.
increase the dynamic channel assignment interval
increase the dynamic channel assignment interval
Explanation: These message logs inform that the radio channel has been reset (and the AP must be down briefly). With dynamic channel assignment (DCA), the radios can frequently switch from one channel to another but it also makes disruption. The default DCA interval is 10 minutes, which is matched with the time of the message logs. By increasing the DCA interval, we can reduce the number of times our users are disconnected for changing radio channels.
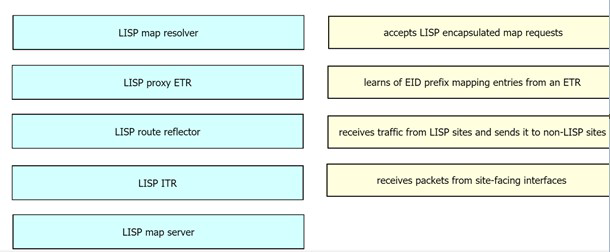
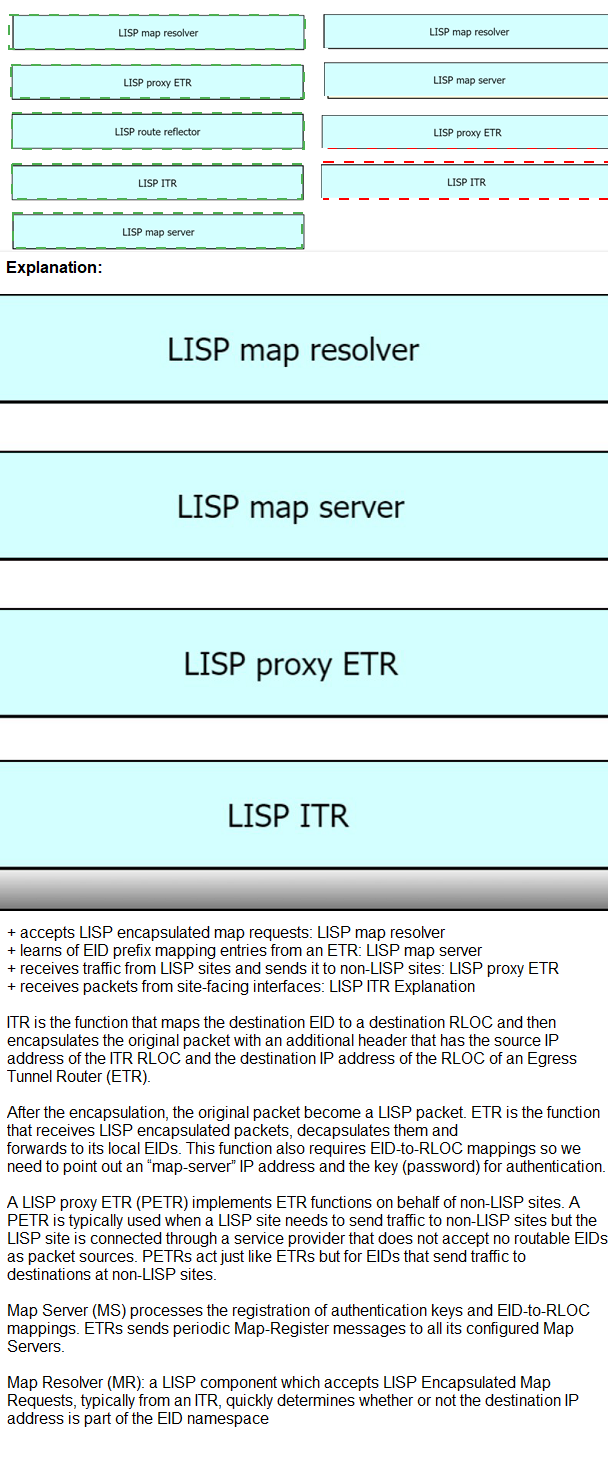
Drag and drop the LISP components from the left onto the function they perform on the right. Not all options are used.
What is the data policy in a Cisco SD-WAN deployment?
A.
list of ordered statements that define node configurations and authentication used within the SD-WAN overlay
B.
Set of statements that defines how data is forwarded based on IP packet information and specific VPNs
C.
detailed database mapping several kinds of addresses with their corresponding location
D.
group of services tested to guarantee devices and links liveliness within the SD-WAN overlay
Set of statements that defines how data is forwarded based on IP packet information and specific VPNs
| Page 1 out of 84 Pages |