Topic 2: Exam Pool B
A newly joined employee. Janet, has been allocated an existing system used by a previous
employee. Before issuing the system to Janet, it was assessed by Martin, the
administrator. Martin found that there were possibilities of compromise through user
directories, registries, and other system parameters. He also Identified vulnerabilities such
as native configuration tables, incorrect registry or file permissions, and software
configuration errors. What is the type of vulnerability assessment performed by Martin?
A.
Credentialed assessment
B.
Database assessment
C.
Host-based assessment
D.
Distributed assessment
Host-based assessment
Explanation: The host-based vulnerability assessment (VA) resolution arose from the
auditors’ got to periodically review systems. Arising before the net becoming common,
these tools typically take an “administrator’s eye” read of the setting by evaluating all of the knowledge that an administrator has at his or her disposal.
UsesHost VA tools verify system configuration, user directories, file systems, registry
settings, and all forms of other info on a number to gain information about it. Then, it
evaluates the chance of compromise. it should also live compliance to a predefined
company policy so as to satisfy an annual audit. With administrator access, the scans area
unit less possible to disrupt traditional operations since the computer code has the access
it has to see into the complete configuration of the system.
What it Measures Host
VA tools will examine the native configuration tables and registries to spot not solely
apparent vulnerabilities, however additionally “dormant” vulnerabilities – those weak or
misconfigured systems and settings which will be exploited when an initial entry into the
setting. Host VA solutions will assess the safety settings of a user account table; the
access management lists related to sensitive files or data; and specific levels of trust
applied to other systems. The host VA resolution will a lot of accurately verify the extent of
the danger by determinant however way any specific exploit could also be ready to get.
Vlady works in a fishing company where the majority of the employees have very little
understanding of IT let alone IT Security. Several information security issues that Vlady
often found includes, employees sharing password, writing his/her password on a post it
note and stick it to his/her desk, leaving the computer unlocked, didn’t log out from emails
or other social media accounts, and etc.
After discussing with his boss, Vlady decided to make some changes to improve the
security environment in his company. The first thing that Vlady wanted to do is to make the
employees understand the importance of keeping confidential information, such as
password, a secret and they should not share it with other persons.
Which of the following steps should be the first thing that Vlady should do to make the
employees in his company understand to importance of keeping confidential information a
secret?
A.
Warning to those who write password on a post it note and put it on his/her desk
B.
Developing a strict information security policy
C.
Information security awareness training
D.
Conducting a one to one discussion with the other employees about the importance of information security
Warning to those who write password on a post it note and put it on his/her desk
You are trying to break into a highly classified top-secret mainframe computer with highest
security system in place at Merclyn Barley Bank located in Los Angeles.
You know that conventional hacking doesn't work in this case, because organizations such
as banks are generally tight and secure when it comes to protecting their systems.
In other words, you are trying to penetrate an otherwise impenetrable system.
How would you proceed?
A.
Look for "zero-day" exploits at various underground hacker websites in Russia and
China and buy the necessary exploits from these hackers and target the bank's network
B.
Try to hang around the local pubs or restaurants near the bank, get talking to a poorlypaid
or disgruntled employee, and offer them money if they'll abuse their access privileges
by providing you with sensitive information
C.
Launch DDOS attacks against Merclyn Barley Bank's routers and firewall systems using
100, 000 or more "zombies" and "bots"Try to conduct Man-in-the-Middle (MiTM) attack and divert the network traffic going to
the Merclyn Barley Bank's Webserver to that of your machine using DNS Cache Poisoning
techniques
D.
Try to conduct Man-in-the-Middle (MiTM) attack and divert the network traffic going to
the Merclyn Barley Bank's Webserver to that of your machine using DNS Cache Poisoning
techniques
Try to hang around the local pubs or restaurants near the bank, get talking to a poorlypaid
or disgruntled employee, and offer them money if they'll abuse their access privileges
by providing you with sensitive information
There are multiple cloud deployment options depending on how isolated a customer's
resources are from those of other customers. Shared environments share the costs and
allow each customer to enjoy lower operations expenses. One solution Is for a customer to
Join with a group of users or organizations to share a cloud environment. What is this cloud
deployment option called?
A.
Hybrid
B.
Community
C.
Public
D.
Private
Community
The purpose of this idea is to permit multiple customers to figure on joint projects and
applications that belong to the community, where it’s necessary to possess a centralized
clouds infrastructure. In other words, Community Cloud may be a distributed infrastructure
that solves the precise problems with business sectors by integrating the services provided
by differing types of clouds solutions.
The communities involved in these projects, like tenders, business organizations, and
research companies, specialise in similar issues in their cloud interactions. Their shared
interests may include concepts and policies associated with security and compliance
considerations, and therefore the goals of the project also .
Community Cloud computing facilitates its users to spot and analyze their business
demands better. Community Clouds could also be hosted during a data center, owned by
one among the tenants, or by a third-party cloud services provider and may be either onsite
or off-site.
Community Cloud Examples and Use CasesCloud providers have developed Community
Cloud offerings, and a few organizations are already seeing the advantages . the
subsequent list shows a number of the most scenarios of the Community Cloud model
that’s beneficial to the participating organizations.
Multiple governmental departments that perform transactions with each other can
have their processing systems on shared infrastructure. This setup makes it costeffective
to the tenants, and may also reduce their data traffic.
Benefits of Community CloudsCommunity Cloud provides benefits to organizations within
the community, individually also as collectively. Organizations don’t need to worry about
the safety concerns linked with Public Cloud due to the closed user group.
This recent cloud computing model has great potential for businesses seeking costeffective
cloud services to collaborate on joint projects, because it comes with multiple
advantages.
Openness and ImpartialityCommunity Clouds are open systems, and that they remove the
dependency organizations wear cloud service providers. Organizations are able to do
many benefits while avoiding the disadvantages of both public and personal clouds.
Ensures compatibility among each of its users, allowing them to switch properties
consistent with their individual use cases. They also enable companies to interact
with their remote employees and support the utilization of various devices, be it a
smartphone or a tablet. This makes this sort of cloud solution more flexible to
users’ demands.
Consists of a community of users and, as such, is scalable in several aspects like
hardware resources, services, and manpower. It takes under consideration
demand growth, and you simply need to increase the user-base.
Flexibility and ScalabilityHigh Availability and ReliabilityYour cloud service must be ready to
make sure the availability of knowledge and applications in the least times. Community
Clouds secure your data within the same way as the other cloud service, by replicating
data and applications in multiple secure locations to guard them from unforeseen
circumstances.
Cloud possesses redundant infrastructure to form sure data is out there whenever and wherever you would like it. High availability and reliability are critical concerns for any sort
of cloud solution.
Security and ComplianceTwo significant concerns discussed when organizations believe
cloud computing are data security and compliance with relevant regulatory authorities.
Compromising each other’s data security isn’t profitable to anyone during a Community
Cloud.
the power to dam users from editing and downloading specific datasets.
Making sensitive data subject to strict regulations on who has access to Sharing
sensitive data unique to a specific organization would bring harm to all or any the
members involved.
What devices can store sensitive data.
Users can configure various levels of security for his or her data. Common use
cases:Convenience and ControlConflicts associated with convenience and control don’t
arise during a Community Cloud. Democracy may be a crucial factor the Community Cloud
offers as all tenants share and own the infrastructure and make decisions collaboratively.
This setup allows organizations to possess their data closer to them while avoiding the
complexities of a personal Cloud.
Less Work for the IT DepartmentHaving data, applications, and systems within the cloud
means you are doing not need to manage them entirely. This convenience eliminates the
necessity for tenants to use extra human resources to manage the system. Even during a
self-managed solution, the work is split among the participating organizations.
Environment SustainabilityIn the Community Cloud, organizations use one platform for all
their needs, which dissuades them from investing in separate cloud facilities. This shift
introduces a symbiotic relationship between broadening and shrinking the utilization of
cloud among clients. With the reduction of organizations using different clouds, resources
are used more efficiently, thus resulting in a smaller carbon footprint.
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.
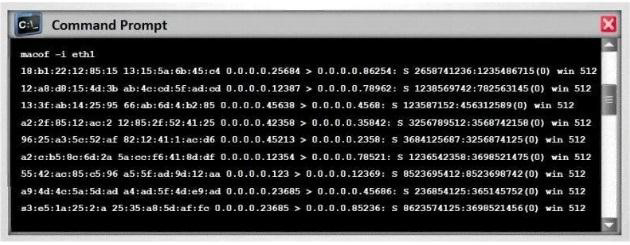
In MAC flooding attack, a switch is fed with many Ethernet frames, each containing
different source MAC addresses, by the attacker. Switches have a limited memory for
mapping various MAC addresses to physical ports. What happens when the CAM table
becomes full?
A.
Switch then acts as hub by broadcasting packets to all machines on the network
B.
The CAM overflow table will cause the switch to crash causing Denial of Service
C.
The switch replaces outgoing frame switch factory default MAC address of
FF:FF:FF:FF:FF:FF
D.
Every packet is dropped and the switch sends out SNMP alerts to the IDS port
Switch then acts as hub by broadcasting packets to all machines on the network
Widespread fraud ac Enron. WorldCom, and Tyco led to the creation of a law that was
designed to improve the accuracy and accountability of corporate disclosures. It covers
accounting firms and third parties that provide financial services to some organizations and
came into effect in 2002. This law is known by what acronym?
A.
Fed RAMP
B.
PCIDSS
C.
SOX
D.
HIPAA
SOX
Explanation: The Sarbanes-Oxley Act of 2002 could be a law the U.S. Congress passed
on July thirty of that year to assist defend investors from fallacious money coverage by
companies.Also called the SOX Act of 2002 and also the company Responsibility Act of
2002, it mandated strict reforms to existing securities rules and obligatory powerful new
penalties on law breakers.
The Sarbanes-Oxley law Act of 2002 came in response to money scandals within the early
2000s involving in public listed corporations like Enron Corporation, Tyco International plc,
and WorldCom. The high-profile frauds cask capitalist confidence within the trustiness of
company money statements Associate in Nursingd light-emitting diode several to demand
an overhaul of decades-old restrictive standards.
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the
ARP cache of these switches.
If these switches' ARP cache is successfully flooded, what will be the result?
A.
The switches will drop into hub mode if the ARP cache is successfully flooded
B.
If the ARP cache is flooded, the switches will drop into pix mode making it less
susceptible to attacks.
C.
Depending on the switch manufacturer, the device will either delete every entry in its
ARP cache or reroute packets to the nearest switch.
D.
The switches will route all traffic to the broadcast address created collisions
The switches will drop into hub mode if the ARP cache is successfully flooded
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in
subnet to. 1.4.0/23. Which of the following IP addresses could be teased as a result of the
new configuration?
A.
210.1.55.200
B.
10.1.4.254
C.
10..1.5.200
D.
10.1.4.156
10..1.5.200
During the process of encryption and decryption, what keys are shared?
A.
Private keys
B.
User passwords
C.
Public keys
D.
Public and private keys
Public keys
An organization is performing a vulnerability assessment tor mitigating threats. James, a
pen tester, scanned the organization by building an inventory of the protocols found on the
organization's machines to detect which ports are attached to services such as an email
server, a web server or a database server. After identifying the services, he selected the
vulnerabilities on each machine and started executing only the relevant tests. What is the
type of vulnerability assessment solution that James employed in the above scenario?
A.
Product-based solutions
B.
Tree-based assessment
C.
Service-based solutions
D.
inference-based assessment
inference-based assessment
Explanation: In an inference-based assessment, scanning starts by building an inventory
of the protocols found on the machine. After finding a protocol, the scanning process starts
to detect which ports are attached to services, such as an email server, web server, or
database server. After finding services, it selects vulnerabilities on each machine and starts
to execute only those relevant tests.
| Page 21 out of 57 Pages |
| Previous |