Topic 2: Exam Pool B
What type of analysis is performed when an attacker has partial knowledge of innerworkings
of the application?
A.
Black-box
B.
Announced
C.
White-box
D.
Grey-box
Grey-box
Which file is a rich target to discover the structure of a website during web-server
footprinting?
A.
Document root
B.
Robots.txt
C.
domain.txt
D.
index.html
Robots.txt
Richard, an attacker, aimed to hack loT devices connected to a target network. In this
process. Richard recorded the frequency required to share information between connected
devices. After obtaining the frequency, he captured the original data when commands were
initiated by the connected devices. Once the original data were collected, he used free
tools such as URH to segregate the command sequence. Subsequently, he started
injecting the segregated command sequence on the same frequency into the loT network,
which repeats the captured signals of the devices. What Is the type of attack performed by
Richard In the above scenario?
A.
Side-channel attack
B.
Replay attack
C.
CrypTanalysis attack
D.
Reconnaissance attack
Replay attack
Explanation: Replay Attack could be a variety of security attack to the info sent over a
network.In this attack, the hacker or a person with unauthorized access, captures the traffic
and sends communication to its original destination, acting because the original sender.
The receiver feels that it’s Associate in Nursing genuine message however it’s really the
message sent by the aggressor. the most feature of the Replay Attack is that the consumer
would receive the message double, thence the name, Replay Attack.
Prevention from Replay Attack : 1. Timestamp technique –Prevention from such attackers
is feasible, if timestamp is employed at the side of the info. Supposedly, the timestamp on
an information is over a precise limit, it may be discarded, and sender may be asked to
send the info once more.2. Session key technique –Another way of hindrance, is by
victimisation session key. This key may be used one time (by sender and receiver) per
dealing, and can’t be reused.
Sam is working as a system administrator In an organization. He captured the principal characteristics of a vulnerability and produced a numerical score to reflect Its severity using
CVSS v3.0 to property assess and prioritize the organization's vulnerability management
processes. The base score that Sam obtained after performing cvss rating was 4.0. What is
the CVSS severity level of the vulnerability discovered by Sam in the above scenario?
A.
Medium
B.
Low
C.
Critical
D.
High
Medium
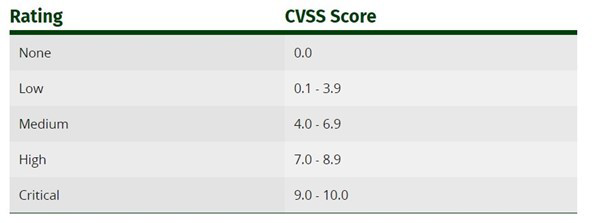
Explanation: Rating CVSS Score
None 0.0
Low 0.1 - 3.9
Medium 4.0 - 6.9
High 7.0 - 8.9
Critical 9.0 - 10.0
https://www.first.org/cvss/v3.0/specification-document
The Common Vulnerability Scoring System (CVSS) is an open framework for
communicating the characteristics and severity of software vulnerabilities. CVSS consists
of three metric groups: Base, Temporal, and Environmental. The Base metrics produce a
score ranging from 0 to 10, which can then be modified by scoring the Temporal and
Environmental metrics. A CVSS score is also represented as a vector string, a compressed
textual representation of the values used to derive the score. Thus, CVSS is well suited as
a standard measurement system for industries, organizations, and governments that need
accurate and consistent vulnerability severity scores. Two common uses of CVSS are
calculating the severity of vulnerabilities discovered on one's systems and as a factor in
prioritization of vulnerability remediation activities. The National Vulnerability Database
(NVD) provides CVSS scores for almost all known vulnerabilities.
Qualitative Severity Rating Scale
For some purposes, it is useful to have a textual representation of the numeric Base,
Temporal and Environmental scores.
A friend of yours tells you that he downloaded and executed a file that was sent to him by a
coworker. Since the file did nothing when executed, he asks you for help because he
suspects that he may have installed a trojan on his computer.
what tests would you perform to determine whether his computer Is Infected?
A.
Use ExifTool and check for malicious content.
B.
You do not check; rather, you immediately restore a previous snapshot of the operating
system.
C.
Upload the file to VirusTotal
D.
Use netstat and check for outgoing connections to strange IP addresses or domains.
Use netstat and check for outgoing connections to strange IP addresses or domains.
Bella, a security professional working at an it firm, finds that a security breach has occurred
while transferring important files. Sensitive data, employee usernames. and passwords are
shared In plaintext, paving the way for hackers 10 perform successful session hijacking. To
address this situation. Bella Implemented a protocol that sends data using encryption and
digital certificates. Which of the following protocols Is used by Bella?
A.
FTP
B.
HTTPS
C.
FTPS
D.
IP
FTPS
Techno Security Inc. recently hired John as a penetration tester. He was tasked with
identifying open ports in the target network and determining whether the ports are online
and any firewall rule sets are encountered. John decided to perform a TCP SYN ping scan
on the target network. Which of the following Nmap commands must John use to perform
the TCP SYN ping scan?
A.
nmap -sn -pp < target ip address >
B.
nmap -sn -PO < target IP address >
C.
nmap -sn -PS < target IP address >
D.
nmap -sn -PA < target IP address >
nmap -sn -PS < target IP address >
Explanation: https://hub.packtpub.com/discovering-network-hosts-with-tcp-syn-and-tcpack-
ping-scans-in-nmaptutorial/
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients.
You are requested to accept the offer and you oblige. After 2 days. Bob denies that he had
ever sent a mail. What do you want to ""know"" to prove yourself that it was Bob who had
send a mail?
A.
Authentication
B.
Confidentiality
C.
Integrity
D.
Non-Repudiation
Non-Repudiation
Explanation:
Non-repudiation is the assurance that someone cannot deny the validity of something.
Non-repudiation is a legal concept that is widely used in information security and refers to a
service, which provides proof of the origin of data and the integrity of the data. In other
words, non-repudiation makes it very difficult to successfully deny who/where a message
came from as well as the authenticity and integrity of that message.
joe works as an it administrator in an organization and has recently set up a cloud
computing service for the organization. To implement this service, he reached out to a
telecom company for providing Internet connectivity and transport services between the
organization and the cloud service provider, in the NIST cloud deployment reference
architecture, under which category does the telecom company fall in the above scenario?
A.
Cloud booker
B.
Cloud consumer
C.
Cloud carrier
D.
Cloud auditor
Cloud carrier
A cloud carrier acts as an intermediary that provides connectivity and transport of cloud
services between cloud consumers and cloud providers.
Cloud carriers provide access to consumers through network, telecommunication and other
access devices. for instance, cloud consumers will obtain cloud services through network
access devices, like computers, laptops, mobile phones, mobile web devices (MIDs), etc.
The distribution of cloud services is often provided by network and telecommunication
carriers or a transport agent, wherever a transport agent refers to a business organization
that provides physical transport of storage media like high-capacity hard drives.
Note that a cloud provider can started SLAs with a cloud carrier to provide services consistent with the level of SLAs offered to cloud consumers, and will require the cloud
carrier to provide dedicated and secure connections between cloud consumers and cloud
providers.
E-mail scams and mail fraud are regulated by which of the following?
A.
18 U.S.C. par. 1030 Fraud and Related activity in connection with Computers
B.
18 U.S.C. par. 1029 Fraud and Related activity in connection with Access Devices
C.
18 U.S.C. par. 1362 Communication Lines, Stations, or Systems
D.
18 U.S.C. par. 2510 Wire and Electronic Communications Interception and Interception
of Oral Communication
18 U.S.C. par. 1030 Fraud and Related activity in connection with Computers
| Page 19 out of 57 Pages |
| Previous |