Topic 1: Site-to-site Virtual Private Networks on Routers and Firewall
Which two parameters help to map a VPN session to a tunnel group without using the
tunnel-group list? (Choose two.)
A.
group-alias
B.
certificate map
C.
optimal gateway selection
D.
group-url
E.
AnyConnect client version
certificate map
group-url
Refer to the exhibit.
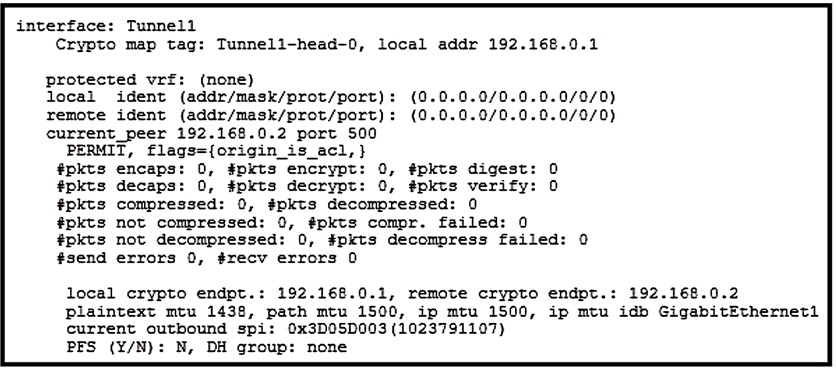
Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit?
(Choose two.)
A.
crypto map
B.
DMVPN
C.
GRE
D.
FlexVPN
E.
VTI
DMVPN
VTI
Which two changes must be made in order to migrate from DMVPN Phase 2 to Phase 3
when EIGRP is configured? (Choose two.)
A.
Add NHRP shortcuts on the hub.
B.
Add NHRP redirects on the spoke.
C.
Disable EIGRP next-hop-self on the hub.
D.
Enable EIGRP next-hop-self on the hub.
E.
Add NHRP redirects on the hub.
Disable EIGRP next-hop-self on the hub.
Add NHRP redirects on the hub.
Refer to the exhibit.

A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
Which statement about GETVPN is true?
A.
The configuration that defines which traffic to encrypt originates from the key server.
B.
TEK rekeys can be load-balanced between two key servers operating in COOP.
C.
The pseudotime that is used for replay checking is synchronized via NTP.
D.
Group members must acknowledge all KEK and TEK rekeys, regardless of
configuration.
The configuration that defines which traffic to encrypt originates from the key server.
On a FlexVPN hub-and-spoke topology where spoke-to-spoke tunnels are not allowed,
which command is needed for the hub to be able to terminate FlexVPN tunnels?
A.
interface virtual-access
B.
ip nhrp redirect
C.
interface tunnel
D.
interface virtual-template
interface virtual-template
Which method dynamically installs the network routes for remote tunnel endpoints?
A.
policy-based routing
B.
CEF
C.
reverse route injection
D.
route filtering
reverse route injection
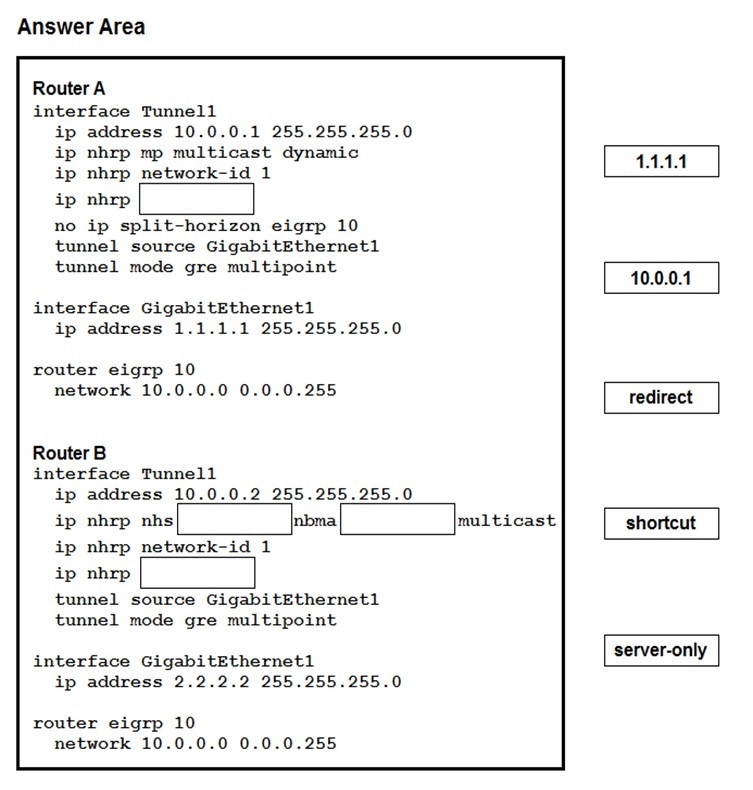
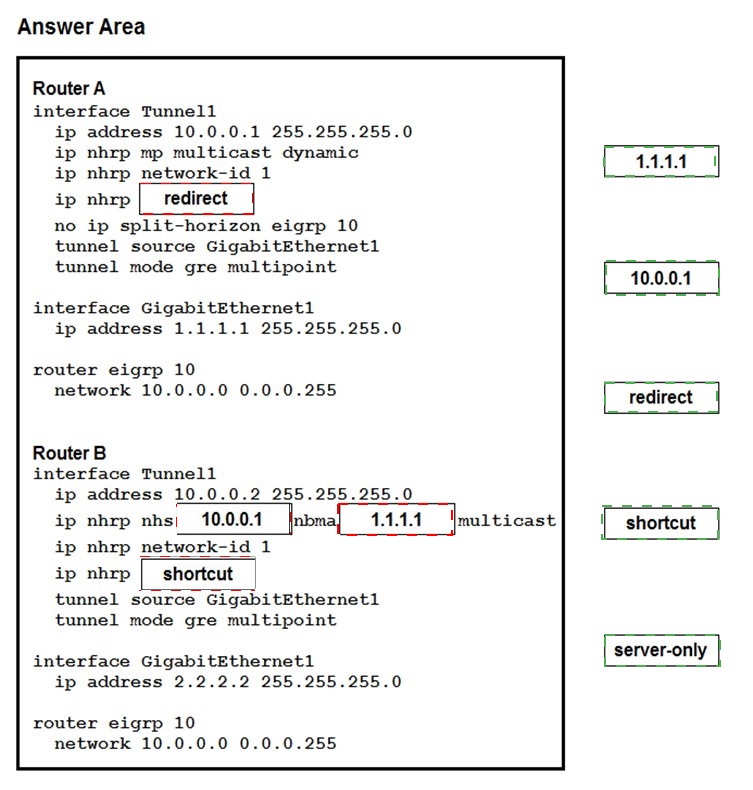
Drag and drop the correct commands from the night onto the blanks within the code on the
left to implement a design that allow for dynamic spoke-to-spoke communication. Not all
comments are used.
Refer to the exhibit.
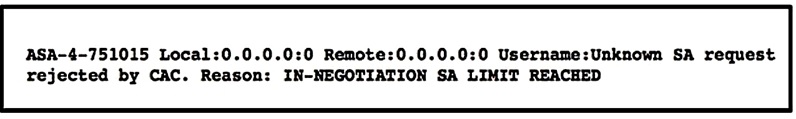
A customer cannot establish an IKEv2 site-to-site VPN tunnel between two Cisco ASA devices. Based on the syslog message, which action brings up the VPN tunnel?
A.
Reduce the maximum SA limit on the local Cisco ASA.
B.
Increase the maximum in-negotiation SA limit on the local Cisco ASA.
C.
Remove the maximum SA limit on the remote Cisco ASA.
D.
Correct the crypto access list on both Cisco ASA devices.
Increase the maximum in-negotiation SA limit on the local Cisco ASA.
A second set of traffic selectors is negotiated between two peers using IKEv2. Which IKEv2
packet will contain details of the exchange?
A.
IKEv2 IKE_SA_INIT
B.
IKEv2 INFORMATIONAL
C.
IKEv2 CREATE_CHILD_SA
D.
IKEv2 IKE_AUTH
IKEv2 INFORMATIONAL