An organization wants to split their Cisco ISE deployment to separate the device
administration functionalities from the mam deployment. For this to work, the administrator
must deregister any nodes that will become a part of the new deployment, but the button for this option is grayed out Which configuration is causing this behavior?
A.
One of the nodes is an active PSN.
B.
One of the nodes is the Primary PAN
C.
All of the nodes participate in the PAN auto failover.
D.
All of the nodes are actively being synched.
One of the nodes is the Primary PAN
An engineer is designing a BYOD environment utilizing Cisco ISE for devices that do not support native supplicants Which portal must the security engineer configure to accomplish
this task?
A.
MDM
B.
Client provisioning
C.
My devices
D.
BYOD
My devices
https://www.cisco.com/c/en/us/td/docs/security/ise/2-
2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_01111.html
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their Workstation from the corporate network Which CoA configuration meets this requirement?
A.
Port Bounce
B.
Reauth
C.
NoCoA
D.
Disconnect
NoCoA
An engineer is configuring web authentication using non-standard ports and needs the switch to redirect traffic to the correct port. Which command should be used to accomplish this task?
A.
permit tcp any any eq <port number>
B.
aaa group server radius proxy
C.
ip http port <port number>
D.
aaa group server radius
aaa group server radius
An engineer is working with a distributed deployment of Cisco ISE and needs to configure
various network probes to collect a set of attributes from the used to accomplish this task?
A.
policy service
B.
monitoring
C.
pxGrid
D.
primary policy administrator
monitoring
A company is attempting to improve their BYOD policies and restrict access based on
certain criteria. The company's subnets are organized by building. Which attribute should
be used in order to gain access based on location?
A.
static group assignment
B.
IP address
C.
device registration status
D.
MAC address
static group assignment
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-
1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010100.html
#ID1353
An organization is migrating its current guest network to Cisco ISE and has 1000 guest
users in the current database There are no resources to enter this information into the
Cisco ISE database manually. What must be done to accomplish this task effciently?
A.
Use a CSV file to import the guest accounts
B.
Use SOL to link me existing database to Ctsco ISE
C.
Use a JSON fie to automate the migration of guest accounts
D.
Use an XML file to change the existing format to match that of Cisco ISE
Use a JSON fie to automate the migration of guest accounts
Which two roles are taken on by the administration person within a Cisco ISE distributed environment? (Choose two.)
A.
backup
B.
secondary
C.
standby
D.
primary
E.
active
secondary
primary
Refer to the exhibit.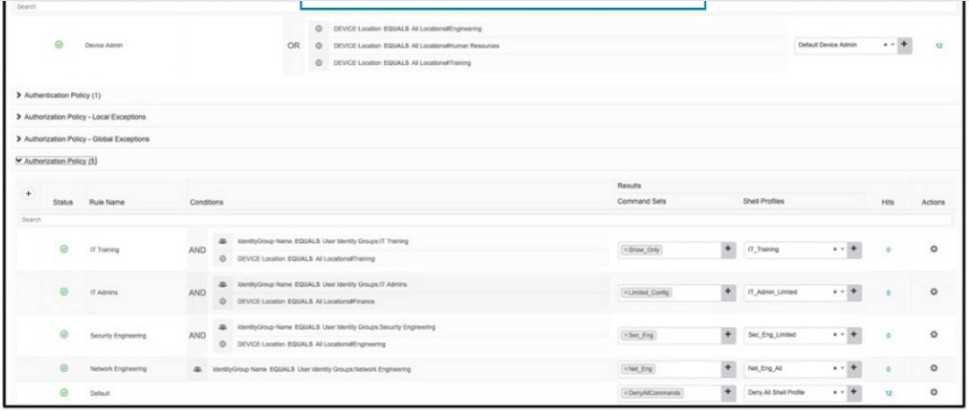
An organization recently implemented network device administration using Cisco ISE. Upon testing the ability to access all of the required devices, a user in the Cisco ISE groupIT Admins is attempting to login to a device in their organization's finance department but is unable to. What is the problem?
A.
The IT training rule is taking precedence over the IT Admins rule.
B.
The authorization conditions wrongly allow IT Admins group no access to finance devices.
C.
The finance location is not a condition in the policy set.
D.
The authorization policy doesn't correctly grant them access to the finance devices.
The authorization policy doesn't correctly grant them access to the finance devices.
An administrator is attempting to replace the built-in self-signed certificates on a Cisco ISE
appliance. The CA is requesting some information about the appliance in order to sign the
new certificate. What must be done in order to provide the CA this information?
A.
Install the Root CA and intermediate CA.
B.
Generate the CSR.
C.
Download the intermediate server certificate.
D.
Download the CA server certificate.
Generate the CSR.
| Page 7 out of 24 Pages |
| Previous |