Which protocol must be allowed for a BYOD device to access the BYOD portal?
A.
HTTP
B.
SMTP
C.
HTTPS
D.
SSH
Which default endpoint identity group does an endpoint that does not match any profile in Cisco ISE become a member of?
A.
Endpoint
B.
unknown
C.
blacklist
D.
white list
E.
profiled
unknown
If you do not have a matching profiling policy, you can assign an unknown profiling policy. The endpoint is therefore profiled as Unknown. The endpoint that does not match any profile is grouped within the Unknown identity group. The endpoint profiled to the Unknown profile requires that you create a profile with an attribute or a set of attributes collected for that endpoint.
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_identities.html
Which command displays all 802 1X/MAB sessions that are active on the switch ports of a Cisco Catalyst switch?
A.
show authentication sessions output
B.
Show authentication sessions
C.
show authentication sessions interface Gi 1/0/x
D.
show authentication sessions interface Gi1/0/x output
Show authentication sessions
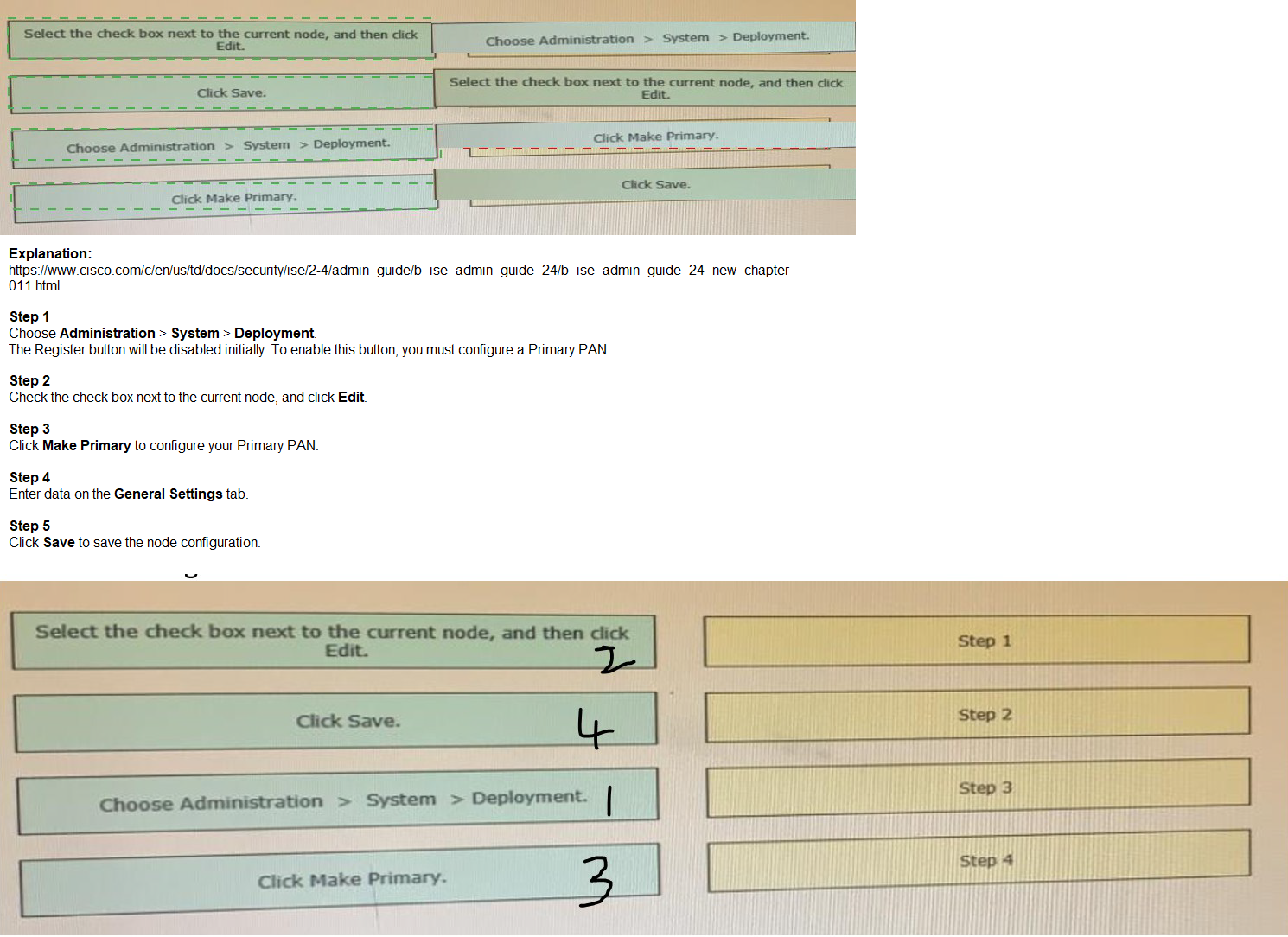
Drag the steps to configure a Cisco ISE node as a primary administration node from the left into the correct order on the night.
Which two ports do network devices typically use for CoA? (Choose two )
A.
443
B.
19005
C.
8080
D.
3799
E.
1700
3799
1700
What is needed to configure wireless guest access on the network?
A.
endpoint already profiled in ISE
B.
WEBAUTH ACL for redirection
C.
valid user account in Active Directory
D.
Captive Portal Bypass turned on
Captive Portal Bypass turned on
What are two benefits of TACACS+ versus RADIUS for device administration? (Choose two )
A.
TACACS+ supports 802.1X, and RADIUS supports MAB
B.
TACACS+ uses UDP, and RADIUS uses TCP
C.
TACACS+ has command authorization, and RADIUS does not.
D.
TACACS+ provides the service type, and RADIUS does not
E.
TACACS+ encrypts the whole payload, and RADIUS encrypts only the password
TACACS+ has command authorization, and RADIUS does not.
TACACS+ encrypts the whole payload, and RADIUS encrypts only the password
What is the purpose of the ip http server command on a switch?
A.
It enables the https server for users for web authentication
B.
It enables MAB authentication on the switch
C.
It enables the switch to redirect users for web authentication
D.
It enables dot1x authentication on the switch
It enables the switch to redirect users for web authentication
Which Cisco ISE service allows an engineer to check the compliance of endpoints before connecting to the network?
A.
personas
B.
qualys
C.
nexpose
D.
posture
posture
Posture is a service in Cisco Identity Services Engine (Cisco ISE) that allows you to check the state, also known as posture, of all the endpoints that are connecting to a network for compliance with corporate security policies. This allows you to control clients to access protected areas of a network.
Which RADIUS attribute is used to dynamically assign the Inactivity active timer for MAB users from the Cisco ISE node?
A.
session timeout
B.
idle timeout
C.
radius-server timeout
D.
termination-action
idle timeout
When the inactivity timer is enabled, the switch monitors the activity from authenticated endpoints. When the inactivity timer expires, the switch removes the authenticated session. The inactivity timer for MAB can be statically configured on the switch port, or it can be dynamically assigned using the RADIUS Idle-Timeout attribute