Topic 2: Configuration
An organization is using a Cisco FTD and Cisco ISE to perform identity-based access
controls. A network administrator is analyzing the Cisco FTD events and notices that
unknown user traffic is being allowed through the firewall. How should this be addressed to
block the traffic while allowing legitimate user traffic?
A.
Modify the Cisco ISE authorization policy to deny this access to the user.
B.
Modify Cisco ISE to send only legitimate usernames to the Cisco FTD.
C.
Add the unknown user in the Access Control Policy in Cisco FTD.
D.
Add the unknown user in the Malware & File Policy in Cisco FTD.
Add the unknown user in the Access Control Policy in Cisco FTD.
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/fdm/fptd-fdmconfig-guide-640/fptd-fdmidentity.html#concept_655B055575E04CA49B10186DEBDA301A
After deploying a network-monitoring tool to manage and monitor networking devices in
your organization, you realize that you need to manually upload an MIB for the Cisco FMC.
In which folder should you upload the MIB file?
A.
/etc/sf/DCMIB.ALERT
B.
/sf/etc/DCEALERT.MIB
C.
/etc/sf/DCEALERT.MIB
D.
system/etc/DCEALERT.MIB
/etc/sf/DCEALERT.MIB
Which command-line mode is supported from the Cisco Firepower Management Center
CLI?
A.
privileged
B.
user
C.
configuration
D.
admin
configuration
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/660/configuration/guide/fpmcconfig-
guide-v66/command_line_reference.pdf
A company is in the process of deploying intrusion prevention with Cisco FTDs managed
by a Cisco FMC. An engineer must configure policies to detect potential intrusions but not
block the suspicious traffic. Which action accomplishes this task?
A.
Configure IDS mode when creating or editing a policy rule under the Cisco FMC
Intrusion tab in Access Policies section by unchecking the "Drop when inline" option.
B.
Configure IDS mode when creating or editing a policy rule under the Cisco FMC
Intrusion tab in Access Policies section by unchecking the "Drop when inline" option.
C.
Configure IPS mode when creating or editing a policy rule under the Cisco FMC
Intrusion tab in Access Policies section by unchecking the "Drop when inline" option.
D.
Configure IDS mode when creating or editing a policy rule under the Cisco FMC
Intrusion tab in Access Policies section by checking the "Drop when inline" option.
Configure IDS mode when creating or editing a policy rule under the Cisco FMC
Intrusion tab in Access Policies section by unchecking the "Drop when inline" option.
A network engineer is configuring URL Filtering on Firepower Threat Defense. Which two
port requirements on the Firepower Management Center must be validated to allow
communication with the cloud service? (Choose two.)
A.
outbound port TCP/443
B.
inbound port TCP/80
C.
outbound port TCP/8080
D.
inbound port TCP/443
E.
outbound port TCP/80
outbound port TCP/443
outbound port TCP/80
Which report template field format is available in Cisco FMC?
A.
box lever chart
B.
arrow chart
C.
bar chart
D.
benchmark chart
bar chart
What is the result of specifying of QoS rule that has a rate limit that is greater than the
maximum throughput of an interface?
A.
The rate-limiting rule is disabled.
B.
Matching traffic is not rate limited.
C.
The system rate-limits all traffic.
D.
The system repeatedly generates warnings.
Matching traffic is not rate limited.
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmcconfig- guide-v62/quality_of_service_qos.pdf
Which command must be run to generate troubleshooting files on an FTD?
A.
system support view-files
B.
sudo sf_troubleshoot.pl
C.
system generate-troubleshoot all
D.
show tech-support
system generate-troubleshoot all
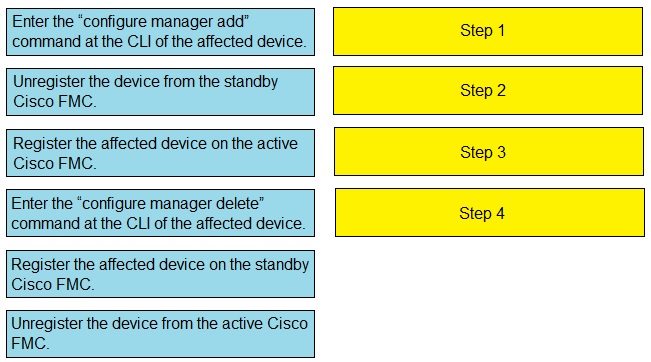
Drag and drop the steps to restore an automatic device registration failure on the standby
Cisco FMC from the left into the correct order on the right. Not all options are used.

Which two statements about deleting and re-adding a device to Cisco FMC are true?
(Choose two.)
A.
An option to re-apply NAT and VPN policies during registration is available, so users do
not need to re- apply the policies after registration is completed.
B.
Before re-adding the device in Cisco FMC, you must add the manager back in the
device.
C.
No option to delete and re-add a device is available in the Cisco FMC web interface.
D.
The Cisco FMC web interface prompts users to re-apply access control policies.
E.
No option to re-apply NAT and VPN policies during registration is available, so users
need to re-apply the policies after registration is completed
The Cisco FMC web interface prompts users to re-apply access control policies.
No option to re-apply NAT and VPN policies during registration is available, so users
need to re-apply the policies after registration is completed
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmcconfig-
guide- v60/Device_Management_Basics.html
| Page 4 out of 26 Pages |
| Previous |