Refer to the exhibit

Between Cisco UCS Fls and Cisco ACI leaf switches, CDP is disabled, the LLDP is
enabled, and LACP is in Active mode. Which two discovery protocols and load-balancing
mechanism combinations can be implemented for the DVS? (Choose two.)
A.
CDP enabled, LLDP disabled, and LACP Active
B.
CDP disabled, LLDP enabled, and MAC Pinning
C.
CDP enabled, LLDP disabled, and MAC Pinning
D.
CDP enabled, LLDP enabled, and LACP Active
E.
CDP enabled, LLDP disabled, and LACP Passive
F.
CDP disabled, LLDP enabled, and LACP Passive
CDP disabled, LLDP enabled, and MAC Pinning
CDP enabled, LLDP disabled, and LACP Passive
Refer to the exhibit.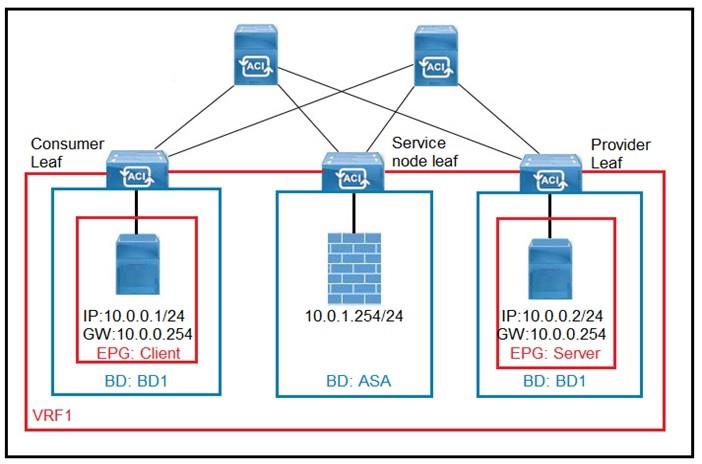
What must be configured in the service graph to redirect HTTP traffic between the EPG client and EPG server to go through the Cisco ASA firewall?
A.
contract filter to allow ARP and HTTP
B.
precise filter to allow only HTTP traffic
C.
contract with no filter
D.
permit-all contract filter
contract filter to allow ARP and HTTP
An engineer configures a new Cisco ACI Multi-Pod and must set up the link between the spine and the IPN device. Which three actions should be taken to accomplish this goal?(Choose three.)
A.
Enable MP-BGP routing
B.
Enable BIDIR-PIM protocol
C.
Enable PIM-SM protocol
D.
Enable OSPF routing
E.
Enable IS-IS routing
F.
Enable DHCP relay
Enable MP-BGP routing
Enable BIDIR-PIM protocol
Enable DHCP relay
What are two characteristics of Cisco ACI interaction with MSTP? (Choose two.)
A.
A Cisco ACI leaf flushes all local endpoints in the received EPG when an MSTP TCN frame is received.
B.
A static path binding is required for native VLAN to carry the MST BPDUs in existing
EPGs.
C.
Mis-cabling protocol is used to snoop the MSTP TCN packets.
D.
A dedicated EPG must be created for the native VLAN ID with static bindings toward the
MSTP-enabled switches.
E.
The PVST simulation must be configured on external network switches to support
MSTP.
Mis-cabling protocol is used to snoop the MSTP TCN packets.
A dedicated EPG must be created for the native VLAN ID with static bindings toward the
MSTP-enabled switches.
Refer to the exhibit.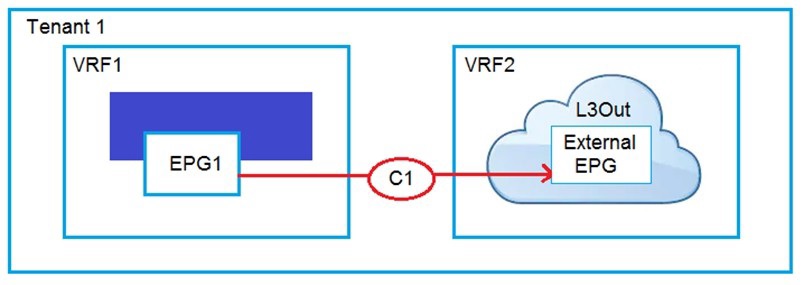
An engineer must have communication between EPG1 in VRF1 and External EPG in
VRF2. Which three actions should be taken for the defined subnets in the L3Out External
EPG to accomplish this goal? (Choose three.)
A.
Enable Shared Route Control Subnet
B.
Enable External Subnets for External EPG
C.
Enable Export Route Control Subnet
D.
Enable Shared Security Import Subnet
E.
Enable Aggregate Shared Routes
F.
Enable Import Route Control Subnet
Enable Export Route Control Subnet
Enable Shared Security Import Subnet
Enable Import Route Control Subnet
Refer to the exhibit.

The 0.0.0.0/0 is configured as a default static route on L3Out-1. Which action should be
taken for the 0.0.0.0/0 prefix to advertise out on L3Out-2 OSPF?
A.
Enable Shared Security Import Subnet
B.
Enable Aggregate Export Subnet
C.
Enable Shared Route Control Subnet
D.
Enable Export Route Control Subnet
E.
Enable Export Route Control Subnet
Enable Aggregate Export Subnet
How is broadcast forwarded in Cisco ACI Multi-Pod after ARP flooding is enabled?
A.
For the specific bridge domain, all spines forward the broadcast frames to IPN routers
B.
Broadcast frames are forwarded inside the pod and across the IPN using the multicast
address that is associated to the bridge domain
C.
Within a pod, the ingress leaf switch floods the broadcast frame on all fabric ports
D.
Ingress replication is used on the spines to forward broadcast frames in the IPN infrastructure
For the specific bridge domain, all spines forward the broadcast frames to IPN routers
How is multicast traffic managed in a Cisco ACI fabric?
A.
FTag trees are rooted at the spine nodes. Cisco APIC determines the roots.
B.
FTag trees are rooted at the leaf nodes. Cisco APIC determines the roots.
C.
FTag trees are rooted at the leaf nodes. The roots must be configured manually.
D.
FTag trees are rooted at the spine nodes. The roots must be configured manually.
FTag trees are rooted at the spine nodes. Cisco APIC determines the roots.
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2015/pdf/BRKAPP-
9004.pdf
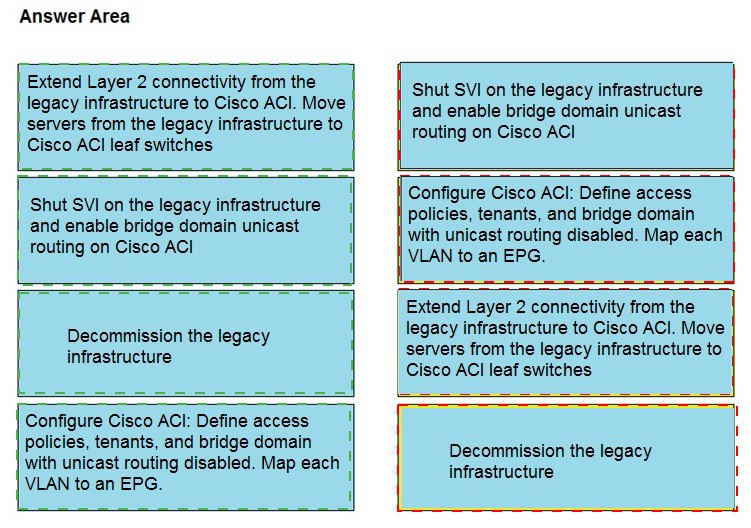
An engineer must migrate servers from a legacy data center infrastructure to a Cisco ACI
fabric. Drag and drop the steps from the left into the order that they must be completed on
the right to ensure the least amount of downtime.
Which feature should be disabled on a bridge domain when a default gateway for
endpoints is on an external device instead of a Cisco ACI bridge domain SVI?
A.
unicast routing
B.
ARP flooding
C.
unknown unicast flooding
D.
proxy ARP
unknown unicast flooding