How are policies deployed on cloud-tiosted Cisco SD-WAN controllers?
A.
Policies are created on vSmart and enforced by vSmart
B.
Policies are created on vSmart and enforced by vManage
C.
Policies are created on vManage and enforced by vManage.
D.
Policies are created on vManage and enforced by vSman
Policies are created on vSmart and enforced by vSmart
An organization wants to use the cisco SD-WAN regionalized service-chaining feature to optimize cost and user experience with application in the network, which allows branch routers to analyze and steer traffic toward the required network function. Which feature meets this requirement?
A.
Cloud Services Platform
B.
VNF Service Chaning
C.
Cloud onRamp for Colocation
D.
Cloud onRamp for laaS
Cloud onRamp for Colocation

https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprisenetworks/sd-wan/nb-06-cisco-sd-wan-ebook-cte-en.pdf

A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
An engineer is configuring a data policy IPv4 prefixes for a site WAN edge device on a site with edge devices. How is this policy added using the policy configuration wizard?
A.
In vManage NMS select (he configure policies screen, select the centralized policy tab and click add policy
B.
In vBood orchestrator. select the configure > policies screen select the localized policy tab. and click add policy
C.
In vManage NMS. select the configure policies screen. select the localized policy taband click add policy
D.
In vSmart controller select tie configure policies screen, select the localized policy tab, and click add policy
In vManage NMS. select the configure policies screen. select the localized policy taband click add policy
What are the two advantages of deploying cloud-based Cisco SD-WAN controllers? (Choose two.)
A.
centralized control and data plane
B.
distributed authentication policies
C.
management of SLA
D.
infrastructure as a service
E.
centralized raid storage of data
management of SLA
infrastructure as a service
Refer to the exhibit.
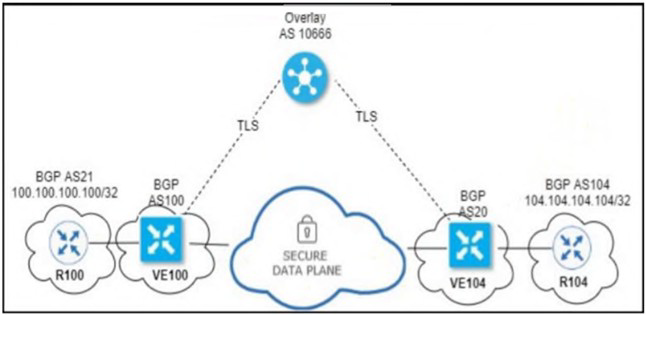
An engineer configured OMP with an overlay-as of 10666. What is the AS-PATH for prefix 104.104.104.104/32 on R100?
A.
100 10666
B.
100 20 104
C.
100 10666 20 104
D.
100 10666 104
100 10666
A voice packet requires a latency of 50 msec. Which policy is configured to ensure that a voice packet is always sent on the link with less than a 50 msec delay?
A.
centralized control
B.
localized data
C.
localized control
D.
centralized data
centralized data
https://www.cisco.com/c/en/us/td/docs/routers/sdwan/configuration/policies/ios-xe-17/policies-book-xe/application-aware-routing.html
What is the threshold to generate a warning alert about CPU or memory usage on a WAN Edge router?
A.
70 to 85 percent
B.
70 to 90 percent
C.
75 to 85 percent
D.
75 to 90 percent
75 to 85 percent
Refer to exhibit.
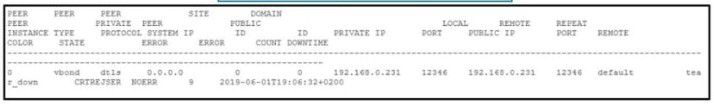
An engineer is troubleshooting tear down of control connections even though a valid Certificate Serial Number is entered Which two actions resolve the Issue? (Choose two)
A.
Enter a valid serial number on the controllers for a given device
B.
Remove the duplicate IP in the network.
C.
Enter a valid product ID (model) on the PNP portal
D.
Match the serial number file between the controllers
E.
Restore network reachability for the controller
Enter a valid product ID (model) on the PNP portal
Match the serial number file between the controllers
https://community.cisco.com/t5/networking-documents/sd-wan-routerstroubleshoot-control-connections/ta-p/3813237
Which two sets of identifiers does OMP carry when it advertises TLOC routes between WAN Edge routers? (Choose two.)
A.
TLOC public and private address, carrier, and preference
B.
source and destination IP address, MAC, and site ID
C.
system IP address, link color, and encapsulation
D.
VPN ID, local site network, and BGP next-hop IP address
E.
TLOC public and private address, tunnel ID, and performance
TLOC public and private address, carrier, and preference
system IP address, link color, and encapsulation
| Page 9 out of 36 Pages |
| Previous |