Topic 1, Exam Pool A
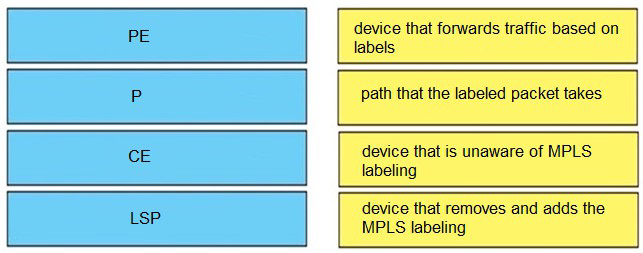
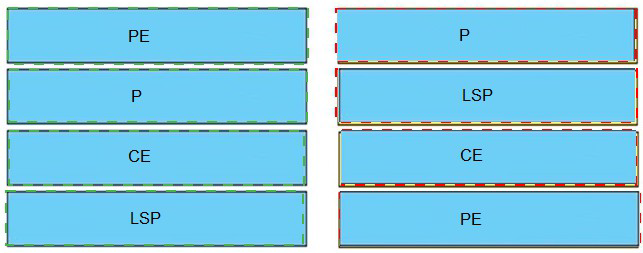
Drag and drop the MPLS terms from the left onto the correct definitions on the right.
Which list defines the contents of an MPLS label?
A.
20-bit label; 3-bit traffic class; 1-bit bottom stack; 8-bit TTL
B.
32-bit label; 3-bit traffic class; 1-bit bottom stack; 8-bit TTL
C.
20-bit label; 3-bit flow label; 1-bit bottom stack; 8-bit hop limit
D.
32-bit label; 3-bit flow label; 1-bit bottom stack; 8-bit hop limit
20-bit label; 3-bit traffic class; 1-bit bottom stack; 8-bit TTL
Explanation: The first 20 bits constitute a label, which can have 2^20 values. Next comes 3 bit value called Traffic Class. It was formerly called as experimental (EXP) field. Now it has been renamed to Traffic Class (TC). This field is used for QoS related functions.
Ingress router can classify the packet according to some criterion and assign a 3 bit value to this filed. If an incoming packet is marked with some IP Precedence or DSCP value and the ingress router may use such a field to assign an FEC to the packet. Next bit is Stack bit which is called bottom-of-stack bit. This field is used when more than one label is assigned to a packet, as in the case of MPLS VPNs or MPLS TE. Next byte is MPLS TTL field which serves the same purpose as that of IP TTL byte in the IP header
Refer to the exhibit.

In which circumstance does the BGP neighbor remain in the idle condition?
A.
if prefixes are not received from the BGP peer
B.
if prefixes reach the maximum limit
C.
if a prefix list is applied on the inbound direction
D.
if prefixes exceed the maximum limit
if prefixes exceed the maximum limit
What is a function of IPv6 ND inspection?
A.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 3 neighbor tables
B.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables
C.
It learns and secures bindings for stateful autoconfiguration addresses in Layer 2 neighbor tables.
D.
It learns and secures bindings for stateful autoconfiguration addresses in Layer 3 neighbor tables.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables
An engineer is trying to copy an IOS file from one router to another router by using TFTP. Which two actions are needed to allow the file to copy? (Choose two.)
A.
Copy the file to the destination router with the copy tftp: flash: command
B.
Enable the TFTP server on the source router with the tftp-server flash: <filename> command
C.
TFTP is not supported in recent IOS versions, so an alternative method must be used
D.
Configure a user on the source router with the username tftp password tftp command
E.
Configure the TFTP authentication on the source router with the tftp-server authentication local command
Copy the file to the destination router with the copy tftp: flash: command
Enable the TFTP server on the source router with the tftp-server flash: <filename> command
Refer to the exhibit.

An engineer is troubleshooting BGP on a device but discovers that the clock on the device does not correspond to the time stamp of the log entries. Which action ensures consistency between the two times?
A.
Configure the service timestamps log uptime command in global configuration mode.
B.
Configure the logging clock synchronize command in global configuration mode.
C.
Configure the service timestamps log datetime localtime command in global configuration mode
D.
Make sure that the clock on the device is synchronized with an NTP server.
Configure the service timestamps log datetime localtime command in global configuration mode
While troubleshooting connectivity issues to a router, these details are noticed:
Standard pings to all router interfaces, including loopbacks, are successful.
Data traffic is unaffected.
SNMP connectivity is intermittent.
SSH is either slow or disconnects frequently.
Which command must be configured first to troubleshoot this issue?
A.
show policy-map control-plane
B.
show policy-map
C.
show interface | inc drop
D.
show ip route
show policy-map control-plane
Refer to the exhibit.

The network administrator configured VRF lite for customer A. The technician at the remote site misconfigured VRF on the router. Which configuration will resolve connectivity for both sites of customer_a?
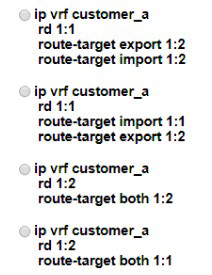
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
Refer to the following output:
Router#show ip nhrp detail
10.1.1.2/8 via 10.2.1.2, Tunnel1 created 00:00:12, expire 01:59:47
TypE. dynamic, Flags: authoritative unique nat registered used
NBMA address: 10.12.1.2
What does the authoritative flag mean in regards to the NHRP information?
A.
It was obtained directly from the next-hop server.
B.
Data packets are process switches for this mapping entry.
C.
NHRP mapping is for networks that are local to this router.
D.
The mapping entry was created in response to an NHRP registration request.
E.
The NHRP mapping entry cannot be overwritten.
It was obtained directly from the next-hop server.
Refer to the exhibit.

AAA server 10.1.1.1 is configured with the default authentication and accounting settings, but the switch cannot communicate with the server Which action resolves this issue?
A.
Match the authentication port
B.
Match the accounting port
C.
Correct the timeout value
D.
Correct the shared secret
Match the authentication port
| Page 9 out of 57 Pages |
| Previous |