Topic 1, Exam Pool A
Which component of MPLS VPNs is used to extend the IP address so that an engineer is able to identify to which VPN it belongs?
A.
VPNv4 address family
B.
RD
C.
RT
D.
LDP
RD
Which security feature can protect DMVPN tunnels?
A.
IPsec
B.
TACACS+
C.
RTBH
D.
RADIUS
IPsec
Refer to the exhibit.
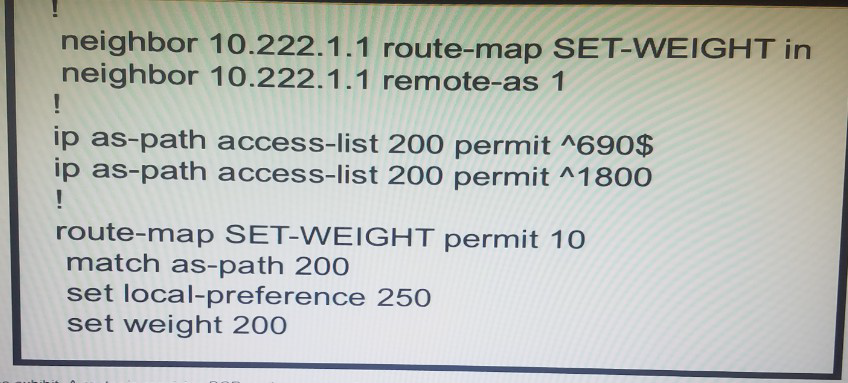
A router receiving BGP routing updates from multiple neighbors for routers in AS 690. What is the reason that the router still sends traffic that is destined to AS 690 to a neighbor other than 10.222.1.1?
A.
The local preference value in another neighbor statement is higher than 250.
B.
The local preference value should be set to the same value as the weight in the route map.
C.
The route map is applied in the wrong direction.
D.
The weight value in another neighbor statement is higher than 200.
The route map is applied in the wrong direction.
Which statement about route distinguishers in an MPLS network is true?
A.
Route distinguishers allow multiple instances of a routing table to coexist within the edge router.
B.
Route distinguishers are used for label bindings.
C.
Route distinguishers make a unique VPNv4 address across the MPLS network.
D.
Route distinguishers define which prefixes are imported and exported on the edge router.
Route distinguishers make a unique VPNv4 address across the MPLS network.
Which two methods use IPsec to provide secure connectivity from the branch office to the headquarters office? (Choose two.)
A.
DMVPN
B.
MPLS VPN
C.
Virtual Tunnel Interface (VTI)
D.
SSL VPN
E.
PPPoE
DMVPN
Virtual Tunnel Interface (VTI)
An engineer configured a leak-map command to summarize EIGRP routes and advertise specifically loopback 0 with an IP of 10.1.1.1.255.255.255.252 along with the summary route. After finishing configuration, the customer complained not receiving summary route with specific loopback address. Which two configurations will fix it? (Choose two.)
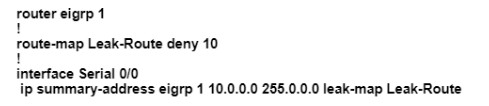
A.
Configure access-list 1 permit 10.1.1.0.0.0.0.3.
B.
Configure access-list 1 permit 10.1.1.1.0.0.0.252.
C.
Configure access-list 1 and match under route-map Leak-Route.
D.
Configure route-map Leak-Route permit 10 and match access-list 1.
E.
Configure route-map Leak-Route permit 20.
Configure access-list 1 permit 10.1.1.0.0.0.0.3.
Configure route-map Leak-Route permit 10 and match access-list 1.
Explanation: When you configure an EIGRP summary route, all networks that fall within the range of your summary are suppressed and no longer advertised on the interface. Only the summary route is advertised. But if we want to advertise a network that has been suppressed along with the summary route then we can use leak-map feature. The below commands will fix the configuration in this question:
R1(config)#access-list 1 permit 10.1.1.0 0.0.0.3
R1(config)#route-map Leak-Route permit 10 // this command will also remove the
“route_map
Leak-Route deny 10” command.
R1(config-route-map)#match ip address 1
What is the role of a route distinguisher via a VRF-Lite setup implementation?
A.
It extends the IP address to identify which VFP instance it belongs to.
B.
It manages the import and export of routes between two or more VRF instances
C.
It enables multicast distribution for VRF-Lite setups to enhance EGP routing protocol capabilities
D.
It enables multicast distribution for VRF-Lite setups to enhance IGP routing protocol capabilities
It extends the IP address to identify which VFP instance it belongs to.
Which statement about IPv6 ND inspection is true?
A.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 3 neighbor tables.
B.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables
C.
It learns and secures bindings for stateful autoconfiguration addresses in Layer 3 neighbor tables.
D.
It learns and secures bindings for stateful autoconfiguration addresses in Layer 2 neighbor tables.
It learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables
Refer to the exhibit.

Network operations cannot read or write any configuration on the device with this configuration from the operations subnet. Which two configurations fix the issue? (Choose two.)
A.
Configure SNMP rw permission in addition to community ciscotest.
B.
Modify access list 1 and allow operations subnet in the access list.
C.
Modify access list 1 and allow SNMP in the access list.
D.
Configure SNMP rw permission in addition to version 1.
E.
Configure SNMP rw permission in addition to community ciscotest 1.
Modify access list 1 and allow operations subnet in the access list.
Configure SNMP rw permission in addition to community ciscotest 1.
Which transport layer protocol is used to form LDP sessions?
A.
UDP
B.
SCTP
C.
TCP
D.
RDP
TCP
Explanation: LDP multicasts hello messages to a well-known UDP port (646) in order to discover neighbors. Once the discovery is accomplished, a TCP connection (port 646) is established and the LDP session begins. LDP keepalives ensure the health of the session.
Thanks to the LDP session, LDP messages create the label mappings required for a FEC. Withdraw messages are used when FECs need to be torn down.
| Page 8 out of 57 Pages |
| Previous |