Topic 1, Exam Pool A
Which protocol is used in a DMVPN network to map physical IP addresses to logical IP addresses?
A.
BGP
B.
LLDP
C.
EIGRP
D.
NHRP
Which two statements about redistributing EIGRP into OSPF are true? (Choose two)
A.
The redistributed EIGRP routes appear as type 3 LSAs in the OSPF database
B.
The redistributed EIGRP routes appear as type 5 LSAs in the OSPF database
C.
The administrative distance of the redistributed routes is 170
D.
The redistributed EIGRP routes appear as OSPF external type 1
E.
The redistributed EIGRP routes as placed into an OSPF area whose area ID matches the EIGRP autonomous system number
F.
The redistributed EIGRP routes appear as OSPF external type 2 routes in the routing table
Refer to the exhibit.
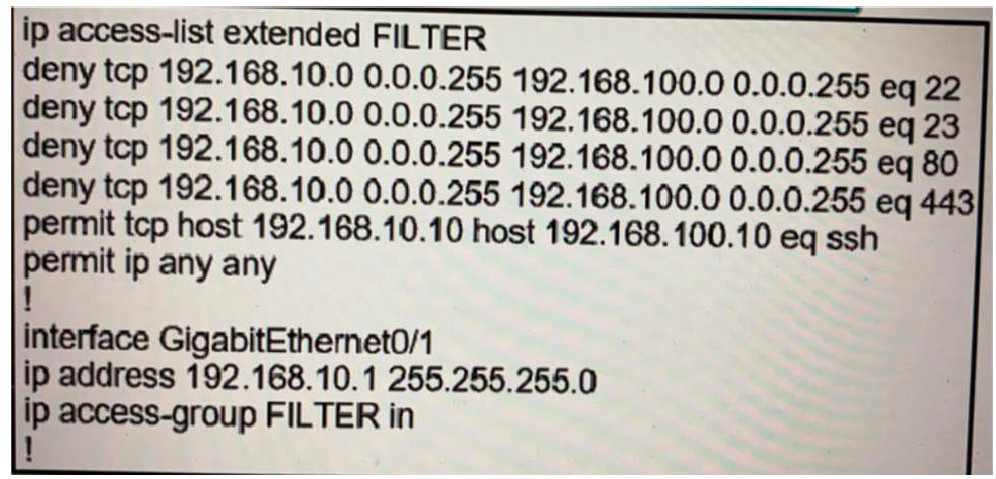
The ACL is placed on the inbound Gigabit 0/1 interface of the router. Host 192.168.10.10cannot SSH to host 192.168.100.10 even though the flow is permitted. Which action resolves the issue without opening full access to this router?
A.
Move the SSH entry to the beginning of the ACL
B.
Temporarily move the permit ip any any line to the beginning of the ACL to see if the flow works
C.
Temporarily remove the ACL from the interface to see if the flow works
D.
Run the show access-list FILTER command to view if the SSH entry has any hit statistic associated with it
Refer to the exhibit.
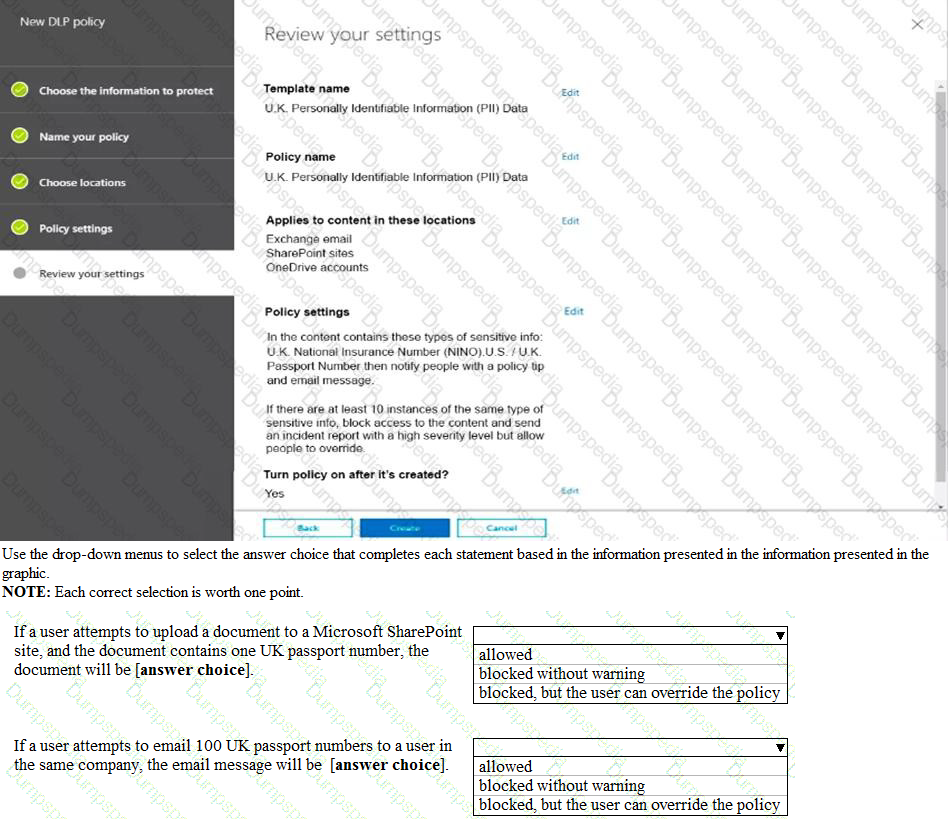
An engineer is trying to configure local authentication on the console line, but the device is trying to authenticate using TACACS+. Which action produces the desired configuration?
A.
Add the aaa authentication login default none command to the global configuration.
B.
Replace the capital “C” with a lowercase “c” in the aaa authentication login Console local command.
C.
Add the aaa authentication login default group tacacs+ local-case command to the
global configuration.
D.
Add the login authentication Console command to the line configuration
Drag and drop the OSPF adjacency states from the left onto the correct descriptions on the right.
Drag and drop the packet types from the left onto the correct descriptions on the right.
Refer to the exhibit.

The output of the trace route from R5 shows a loop in the network. Which configuration prevents this loop?
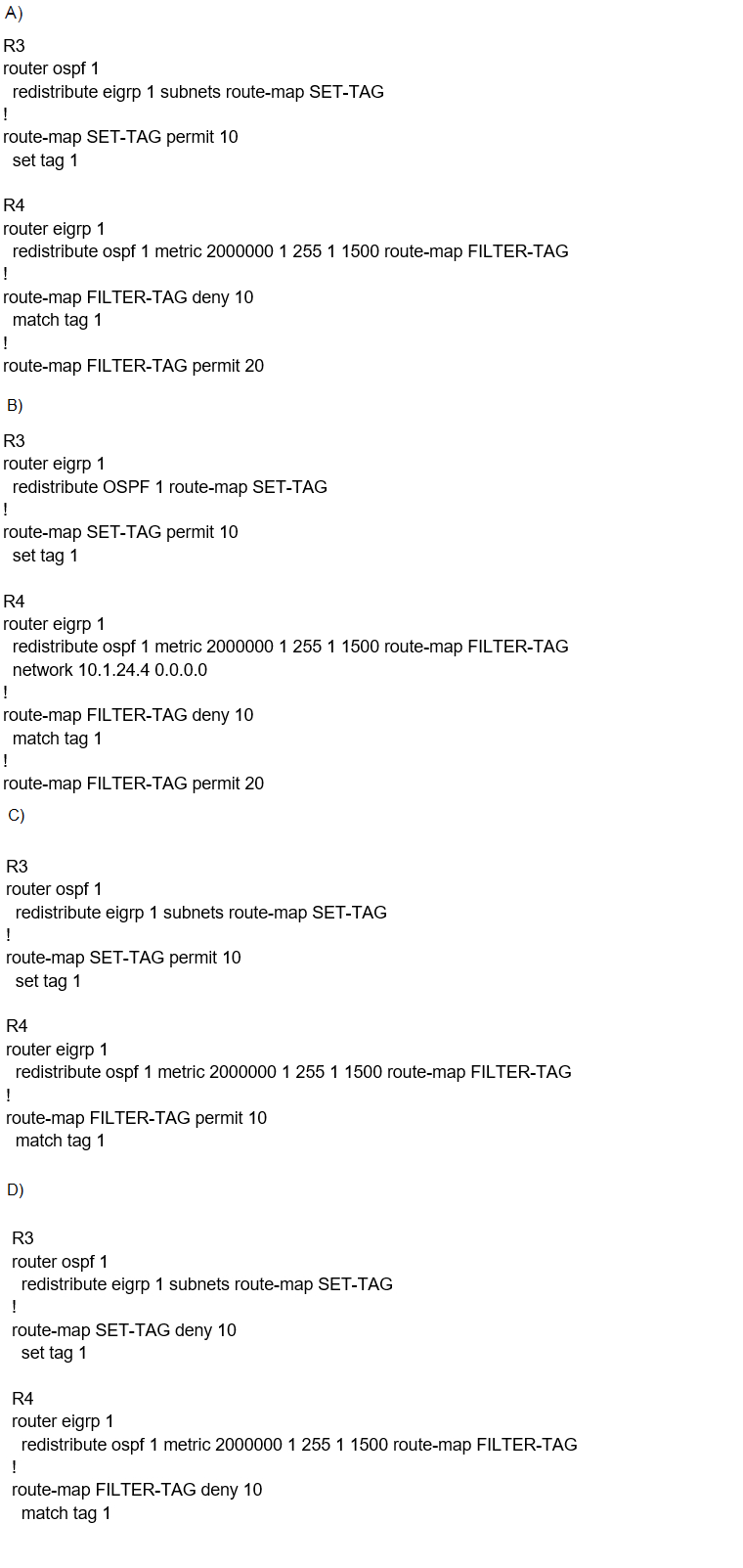
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Refer to the exhibit.

A company is evaluating multiple network management system tools. Trending graphs generated by SNMP data are returned by the NMS and appear to have multiple gaps. While troubleshooting the issue, an engineer noticed the relevant output. What solves the gaps in the graphs?
A.
Remove the exceed-rate command in the class map.
B.
Remove the class map NMS from being part of control plane policing.
C.
Configure the CIR rate to a lower value that accommodates all the NMS tools
D.
Separate the NMS class map in multiple class maps based on the specific protocols with appropriate CoPP actions
Refer to the exhibit. an engineer is trying to get 192.168.32.100 forwarded through 10.1.1.1, but it was forwarded through 10.1.1.2. What action forwards the packets through 10.1.1.1?
A.
Configure EIGRP to receive 192.168.32.0 route with lower admin distance.
B.
A. Configure EIGRP to receive 192.168.32.0 route with longer prefix than /19.
C.
A. Configure EIGRP to receive 192.168.32.0 route with lower metric.
D.
A. Configure EIGRP to receive 192.168.32.0 route with equal or longer prefix than /24.
Refer to the exhibit.
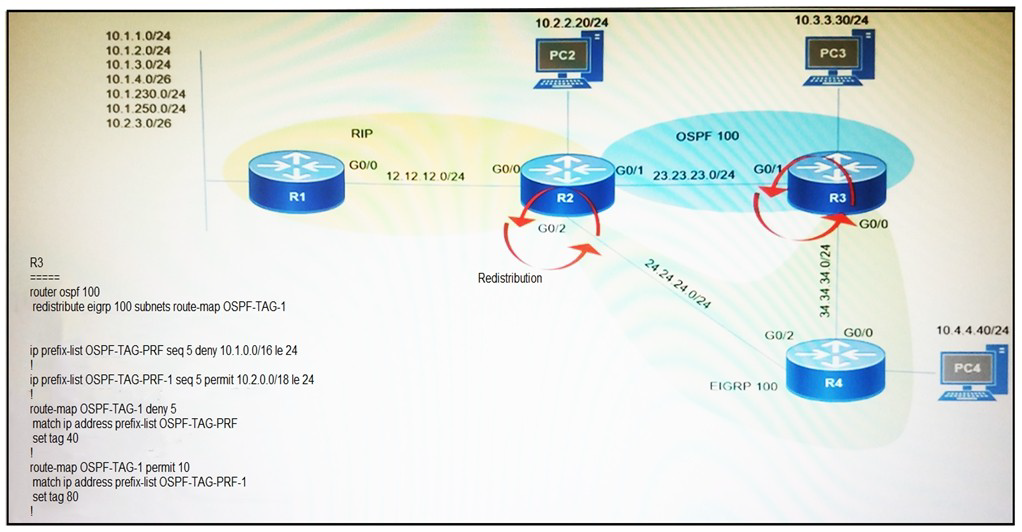
Which subnet is redistributed from EIGRP to OSPF routing protocols?
A.
10.2.2.0/24
B.
10.1.4.0/26
C.
10.1.2.0/24
D.
10.2.3.0/26
| Page 3 out of 57 Pages |
| Previous |