Topic 5: Exam Pool E
A technician is trying to connect to a user's laptop in order to securely install updates. Given the following information about the laptop:
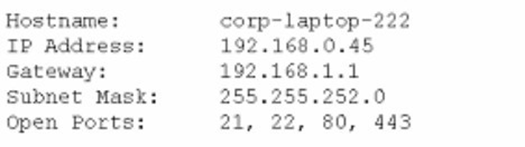
Which of the following should the technician do to connect via RDP?
A. Confirm the user can ping the default gateway.
B. Change the IP address on the user's laptop.
C. Change the subnet mask on the user's laptop.
D. Open port 3389 on the Windows firewall.
A user reports that text on the screen is too small. The user would like to make the text larger and easier to see. Which of the following is the BEST way for the user to increase the size of text, applications, and other items using the Windows 10 Settings tool?
A. Open Settings select Devices, select Display, and change the display resolution to a lower resolution option
B. Open Settings, select System, select Display, and change the display resolution to a lower resolution option.
C. Open Settings Select System, select Display, and change the Scale and layout setting to a higher percentage
D. Open Settings select Personalization, select Display and change the Scale and layout setting to a higher percentage
Explanation:
Open Settings, select System, select Display, and change the Scale and layout setting to a
higher percentage123
Reference: 4. How to Increase the Text Size on Your Computer. Retrieved from
https://www.laptopmag.com/articles/increase-text-size-computer 5. How to Change the
Size of Text in Windows 10.
Retrieved from https://www.howtogeek.com/370055/how-tochange-
the-size-of-text-in-windows-10/ 6. Change the size of text in Windows.
Retrieved
from https://support.microsoft.com/en-us/windows/change-the-size-of-text-in-windows-
1d5830c3-eee3-8eaa-836b-abcc37d99b9a
A technician needs to reimage a desktop in an area without network access. Which of the following should the technician use? (Select two).
A. USB
B. PXE
C. Optical media
D. Partition
E. Boot record
F. SMB
Explanation: A technician needs to reimage a desktop in an area without network access, which means that the technician cannot use network-based methods such as PXE or SMB to deploy the image. Therefore, the technician should use offline methods that involve removable media such as USB or optical media. USB and optical media are common ways to store and transfer system images, and they can be used to boot the desktop and initiate the reimaging process. The technician will need to create a bootable USB or optical media that contains the system image and the imaging software, and then insert it into the desktop and change the boot order in the BIOS or UEFI settings. The technician can then follow the instructions on the screen to reimage the desktop
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work
the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the
problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the Verify
Resolve drop-down menu.


Which of the following items require special e-waste recycling? (Select two). Solid-state drive
A. A/C adapter
B. Surge protector
C. Laptop battery
D. CRT monitor
E. Power supply
A technician has identified malicious traffic originating from a user's computer. Which of the following is the best way to identify the source of the attack?
A. Investigate the firewall logs.
B. Isolate the machine from the network.
C. Inspect the Windows Event Viewer.
D. Take a physical inventory of the device.
Explanation: Isolating the machine from the network is the best way to identify the source of the attack, because it prevents the malicious traffic from spreading to other devices or reaching the attacker. Isolating the machine can also help preserve the evidence of the attack, such as the malware files, the network connections, the registry entries, or the system logs. By isolating the machine, a technician can safely analyze the machine and determine the source of the attack, such as a phishing email, a compromised website, a removable media, or a network vulnerability.
Which of the following OS types provides a lightweight option for workstations thai need an easy-to-use browser-based interface?
A. FreeBSD
B. Chrome OS
C. macOS
D. Windows
Explanation:
Chrome OS provides a lightweight option for workstations that need an easy-to-use
browser-based interface1
Which of the following is command options is used to display hidden files and directories?
A. -a
B. -s
C. -lh
D. -t
Explanation: The -a option is used to display hidden files and directories in a command-line interface. Hidden files and directories are those that start with a dot (.) and are normally not shown by default. The -a option stands for “all” and shows all files and directories, including the hidden ones. The -a option can be used with commands such as ls, dir, or find to list or search for hidden files and directories. The -s, -lh, and -t options are not used to display hidden files and directories. The -s option stands for “size” and shows the size of files or directories in bytes. The -lh option stands for “long human-readable” and shows the size of files or directories in a more readable format, such as KB, MB, or GB. The -t option stands for “time” and sorts the files or directories by modification time.
A user has requested help setting up the fingerprint reader on a Windows 10 laptop. The laptop is equipped with a fingerprint reader and is joined to a domain Group Policy enables Windows Hello on all computers in the environment. Which of the following options describes how to set up Windows Hello Fingerprint for the user?
A. Navigate to the Control Panel utility, select the Security and Maintenance submenu, select Change Security and Maintenance settings, select Windows Hello Fingerprint, and have the user place a fingerprint on the fingerprint reader repeatedly until Windows indicates setup is complete
B. Navigate to the Windows 10 Settings menu, select the Accounts submenu, select Sign in options, select Windows Hello Fingerprint, and have the user place a fingerprint on the fingerprint reader repeatedly until Windows indicates setup is complete.
C. Navigate to the Windows 10 Settings menu, select the Update & Security submenu select Windows Security, select Windows Hello Fingerprint and have the user place a fingerprint on the fingerprint reader repeatedly until Windows indicates setup is complete
D. Navigate to the Control Panel utility, select the Administrative Tools submenu, select the user account in the list, select Windows Hello Fingerprint, and have the user place a fingerprint on the fingerprint reader repeatedly until Windows indicates setup is complete.
Explanation:
Navigate to the Windows 10 Settings menu, select the Accounts submenu, select Sign in
options, select Windows Hello Fingerprint, and have the user place a fingerprint on the
fingerprint reader repeatedly until Windows indicates setup is complete. Windows Hello
Fingerprint can be set up by navigating to the Windows 10 Settings menu, selecting the
Accounts submenu, selecting Sign in options, and then selecting Windows Hello
Fingerprint. The user will then be asked to place a fingerprint on the fingerprint reader
repeatedly until Windows indicates that setup is complete. Windows Hello Fingerprint
allows the user to log into the laptop using just their fingerprint, providing an additional layer
of security.
A technician is unable to completely start up a system. The OS freezes when the desktop background appears, and the issue persists when the system is restarted. Which of the following should the technician do next to troubleshoot the issue?
A. Disable applicable BIOS options.
B. Load the system in safe mode.
C. Start up using a flash drive OS and run System Repair.
D. Enable Secure Boot and reinstall the system.
Explanation: Loading the system in safe mode is a common troubleshooting step that allows the technician to isolate the problem by disabling unnecessary drivers and services. This can help determine if the issue is caused by a faulty device, a corrupted system file, or a malware infection.
| Page 9 out of 74 Pages |
| Previous |