Topic 2, Exam B
What benefit does controller-based networking provide versus traditional networking?
A.
moves from a two-tier to a three-tier network architecture to provide maximum
redundancy
B.
provides an added layer of security to protect from DDoS attacks
C.
allows configuration and monitoring of the network from one centralized port
D.
combines control and data plane functionality on a single device to minimize latency
allows configuration and monitoring of the network from one centralized port
Which type of traffic Is sent with pure iPsec?
A.
broadcast packets from a switch that is attempting to locate a MAC address at one of several remote sites
B.
multicast traffic from a server at one site to hosts at another location
C.
spanning-tree updates between switches that are at two different sites
D.
unicast messages from a host at a remote site lo a server at headquarters
unicast messages from a host at a remote site lo a server at headquarters
Explanation: “The original poster makes a correct observation that EIGRP does not work
in a pure IPSEC environment. IPSEC was designed to process unicast traffic.
Which communication interaction takes place when a southbound API Is used?
A.
between the SDN controller and PCs on the network
B.
between the SON controller and switches and routers on the network
C.
between the SON controller and services and applications on the network
D.
between network applications and switches and routers on the network
between the SON controller and switches and routers on the network
Refer to the exhibit.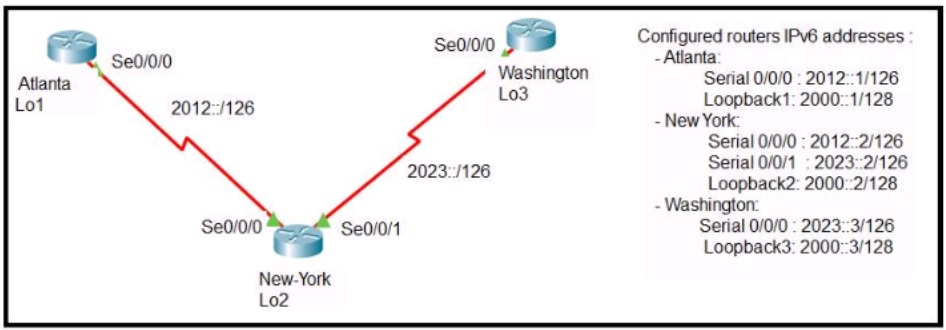
The New York router is configured with static routes pointing to the Atlanta and Washington
sites. Which two tasks must be performed so that the Serial0/0/0 interfaces on the Atlanta
and Washington routers can reach one another?
(Choose two.)
A.
Configure the ipv6 route 2012::/126 2023::1 command on the Washington router.
B.
Configure the ipv6 route 2023::/126 2012::1 command on the Atlanta router.
C.
Configure the Ipv6 route 2012::/126 s0/0/0 command on the Atlanta router.
D.
Configure the ipv6 route 2023::/126 2012::2 command on the Atlanta router.
E.
Configure the ipv6 route 2012::/126 2023::2 command on the Washington router.
Configure the ipv6 route 2023::/126 2012::2 command on the Atlanta router.
Configure the ipv6 route 2012::/126 2023::2 command on the Washington router.
Explanation: The short syntax of static IPv6 route is:ipv6 route <destination-IPv6-address>
{next-hop-IPv6-address | exit-interface}
Which function is performed by DHCP snooping?
A.
propagates VLAN information between switches
B.
listens to multicast traffic for packet forwarding
C.
provides DDoS mitigation
D.
rate-limits certain traffic
propagates VLAN information between switches
Which technology must be implemented to configure network device monitoring with the highest security?
A.
IP SLA
B.
syslog
C.
NetFlow
D.
SNMPv3
NetFlow
Refer to the exhibit.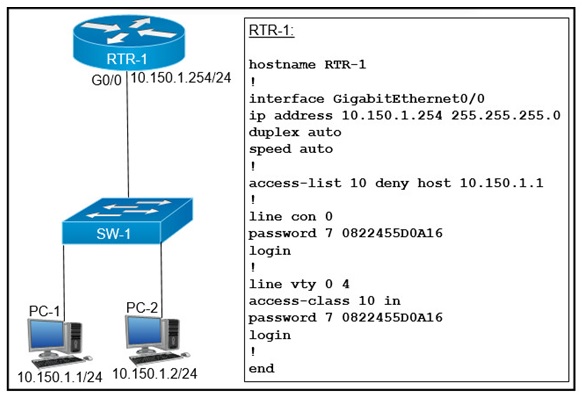
An access list is created to deny Telnet access from host PC-1 to RTR-1 and allow access
from all other hosts A Telnet attempt from PC-2 gives this message:"% Connection refused
by remote host" Without allowing Telnet access from PC-1, which action must be taken to
permit the traffic?
A.
Add the access-list 10 permit any command to the configuration
B.
Remove the access-class 10 in command from line vty 0.4.
C.
Add the ip access-group 10 out command to interface g0/0.
D.
Remove the password command from line vty 0 4.
Add the access-list 10 permit any command to the configuration
How does WPA3 improve security?
A.
It uses SAE for authentication.
B.
It uses a 4-way handshake for authentication.
C.
It uses RC4 for encryption.
D.
It uses TKIP for encryption.
It uses SAE for authentication.
What role does a hypervisor provide for each virtual machine in server virtualization?
A.
infrastructure-as-a-service.
B.
Software-as-a-service
C.
control and distribution of physical resources
D.
services as a hardware controller.
control and distribution of physical resources
Explanation: The hypervisor creates and manages virtual machines on a host computer
and allocates physical system resources to them.
R1 has learned route 192.168.12.0/24 via IS-IS. OSPF, RIP. and Internal EIGRP Under normal operating conditions, which routing protocol is installed in the routing table?
A.
IS-IS
B.
RIP
C.
Internal EIGRP
D.
OSPF
Internal EIGRP
| Page 33 out of 87 Pages |
| Previous |