Topic 2, Exam B

Refer to the exhibit. After the configuration is applied, the two routers fail to establish an
OSPF neighbor relationship. what is the reason for the problem?
A.
The OSPF router IDs are mismatched.
B.
Router2 is using the default hello timer.
C.
The network statement on Router1 is misconfigured.
D.
The OSPF process IDs are mismatched.
Router2 is using the default hello timer.
Refer to Exhibit.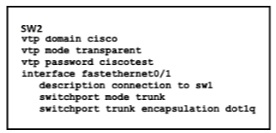
How does SW2 interact with other switches in this VTP domain?
A.
It processes VTP updates from any VTP clients on the network on its access ports.
B.
It receives updates from all VTP servers and forwards all locally configured VLANs out all trunk ports
C.
It forwards only the VTP advertisements that it receives on its trunk ports.
D.
It transmits and processes VTP updates from any VTP Clients on the network on its trunk ports
It forwards only the VTP advertisements that it receives on its trunk ports.
Reference: https://www.cisco.com/c/en/us/support/docs/lan-switching/vtp/10558-21.html
The VTP mode of SW2 is transparent so it only forwards the VTP updates it receives to its
trunk links without processing them.
A corporate office uses four floors in a building
• Floor 1 has 24 users
• Floor 2 has 29 users
• Floor 3 has 28 users
•Floor 4 has 22 users
Which subnet summarizes and gives the most efficient distribution of IP addresses for the
router configuration?
A.
192.168.0.0/26 as summary and 192.168.0.0/29 for each floor
B.
192.168.0.0.24 as summary and 192.168.0.0/28 for each floor
C.
192.168.0.0/23 as summary and 192.168.0.0/25 for each floor
D.
l92.168.0.0/25 as summary and 192.168.0.0/27 for each floor
l92.168.0.0/25 as summary and 192.168.0.0/27 for each floor
What is a role of access points in an enterprise network?
A.
connect wireless devices to a wired network
B.
support secure user logins to devices or the network
C.
integrate with SNMP in preventing DDoS attacks
D.
serve as a first line of defense in an enterprise network
connect wireless devices to a wired network
Which command must be entered to configure a DHCP relay?
A.
ip helper-address
B.
ip address dhcp
C.
ip dhcp pool
D.
ip dhcp relay
ip helper-address
Which configuration is needed to generate an RSA key for SSH on a router?
A.
Configure the version of SSH
B.
Configure VTY access.
C.
Create a user with a password.
D.
Assign a DNS domain name
Assign a DNS domain name
Which type of organization should use a collapsed-core architecture?
A.
large and requires a flexible, scalable network design
B.
large and must minimize downtime when hardware fails
C.
small and needs to reduce networking costs currently
D.
small but is expected to grow dramatically in the near futu
small and needs to reduce networking costs currently
Explanation: A collapsed-core architecture is a limited investment for a small company,
and may be efficient and productive for a limited time.
An engineer must configure a WLAN using the strongest encryption type for WPA2- PSK. Which cipher fulfills the configuration requirement?
A.
WEP
B.
RC4
C.
AES
D.
TKIP
AES
Explanation: Many routers provide WPA2-PSK (TKIP), WPA2-PSK (AES), and WPA2-
PSK (TKIP/AES) as options. TKIP is actually an older encryption protocol introduced with
WPA to replace the very-insecure WEP encryption at the time. TKIP is actually quite similar
to WEP encryption. TKIP is no longer considered secure, and is now deprecated. In other
words, you shouldn’t be using it.
AES is a more secure encryption protocol introduced with WPA2 and it is currently the
strongest encryption type for WPA2-PSK.
An engineer must establish a trunk link between two switches. The neighboring switch is set to trunk or desirable mode. What action should be taken?
A.
configure switchport nonegotiate
B.
configure switchport mode dynamic desirable
C.
configure switchport mode dynamic auto
D.
configure switchport trunk dynamic desirable
configure switchport mode dynamic auto
Which condition must be met before an NMS handles an SNMP trap from an agent?
A.
The NMS software must be loaded with the MIB associated with the trap.
B.
The NMS must be configured on the same router as the SNMP agent
C.
The NMS must receive a trap and an inform message from the SNMP agent within a
configured interval
D.
The NMS must receive the same trap from two different SNMP agents to verify that it is
reliable.
The NMS software must be loaded with the MIB associated with the trap.
| Page 31 out of 87 Pages |
| Previous |