Topic 2, Exam B
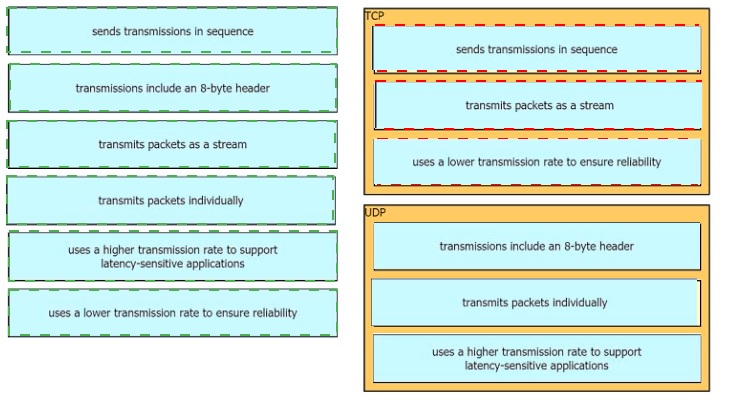
Drag the descriptions of IP protocol transmissions from the left onto the IP traffic types on the right.
If a switch port receives a new frame while it is actively transmitting a previous frame, how does it process the frames?
A.
The new frame is delivered first, the previous frame is dropped, and a retransmission request is sent.
B.
The previous frame is delivered, the new frame is dropped, and a retransmission request is sent.
C.
The new frame is placed in a queue for transmission after the previous frame.
D.
The two frames are processed and delivered at the same time.
The previous frame is delivered, the new frame is dropped, and a retransmission request is sent.
What is the primary function of a Layer 3 device?
A.
to analyze traffic and drop unauthorized traffic from the Internet
B.
to transmit wireless traffic between hosts
C.
to pass traffic between different networks
D.
forward traffic within the same broadcast domain
to pass traffic between different networks
A Cisco IP phone receive untagged data traffic from an attached PC. Which action is taken by the phone?
A.
It allows the traffic to pass through unchanged
B.
It drops the traffic
C.
It tags the traffic with the default VLAN
D.
It tags the traffic with the native VLAN
It allows the traffic to pass through unchanged
Explanation:
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst2960x/software/15-
0_2_EX/vlan/configuration_guide/b_vlan_152ex_2960-x_cg/b_vlan_152ex_2960-
x_cg_chapter_0110.pdf
Untagged traffic from the device attached to the Cisco IP Phone passes through the phone
unchanged, regardless of the trust state of the access port on the phone.
What is a difference between RADIUS and TACACS+?
A.
RADIUS is most appropriate for dial authentication, but TACACS+ can be used for multiple types of authentication
B.
TACACS+ encrypts only password information and RADIUS encrypts the entire payload
C.
TACACS+ separates authentication and authorization, and RADIUS merges them
D.
RADIUS logs all commands that are entered by the administrator, but TACACS+ logs
only start, stop, and interim commands
TACACS+ separates authentication and authorization, and RADIUS merges them
The service password-encryption command is entered on a router. What is the effect of
this configuration?
A.
restricts unauthorized users from viewing clear-text passwords in the running
configuration
B.
encrypts the password exchange when a VPN tunnel is established
C.
prevents network administrators from configuring clear-text passwords
D.
protects the VLAN database from unauthorized PC connections on the switch
restricts unauthorized users from viewing clear-text passwords in the running
configuration
Which two must be met before SSH can operate normally on a Cisco IOS switch? (Choose two)
A.
The switch must be running a k9 (crypto) IOS image
B.
The Ip domain-name command must be configured on the switch
C.
IP routing must be enabled on the switch
D.
A console password must be configured on the switch
E.
Telnet must be disabled on the switch
The switch must be running a k9 (crypto) IOS image
The Ip domain-name command must be configured on the switch
Reference: https://www.cisco.com/c/en/us/support/docs/security-vpn/secure-shellssh/
4145-ssh.html
What are two reasons for an engineer to configure a floating state route? (Choose two)
A.
to automatically route traffic on a secondary path when the primary path goes down
B.
to route traffic differently based on the source IP of the packet
C.
to enable fallback static routing when the dynamic routing protocol fails
D.
to support load balancing via static routing
E.
to control the return path of traffic that is sent from the router
to automatically route traffic on a secondary path when the primary path goes down
to enable fallback static routing when the dynamic routing protocol fails
What is the effect when loopback interfaces and the configured router ID are absent during the OSPF Process configuration?
A.
No router ID is set, and the OSPF protocol does not run.
B.
The highest up/up physical interface IP address is selected as the router ID.
C.
The lowest IP address is incremented by 1 and selected as the router ID.
D.
The router ID 0.0.0.0 is selected and placed in the OSPF process.
The highest up/up physical interface IP address is selected as the router ID.
Refer to the exhibit.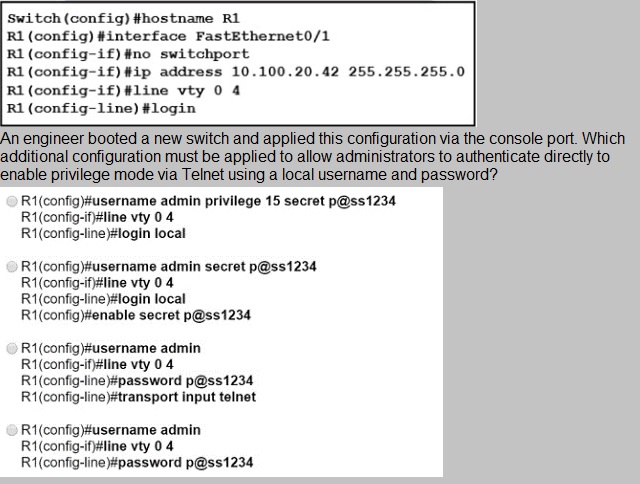
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
| Page 30 out of 87 Pages |
| Previous |