Topic 1: Exam Pool A
desc about topic
Which state does the switch port move to when PortFast is enabled?
A.
learning
B.
forwarding
C.
blocking
D.
listening
forwarding
In which situation is private IPv4 addressing appropriate for a new subnet on the network of
an organization?
A.
There is limited unique address space, and traffic on the new subnet will stay local
within the organization.
B.
The network has multiple endpoint listeners, and it is desired to limit the number of
broadcasts.
C.
Traffic on the subnet must traverse a site-to-site VPN to an outside organization.
D.
The ISP requires the new subnet to be advertised to the internet for web services.
There is limited unique address space, and traffic on the new subnet will stay local
within the organization.
Aside from discarding, which two states does the switch port transition through while using
RSTP (802.1w)? (Choose two)
A.
listening
B.
blocking
C.
forwarding
D.
learning
E.
speaking
forwarding
learning
How will Link Aggregation be Implemented on a Cisco Wireless LAN Controller?
A.
One functional physical port is needed to pass client traffic
B.
The EthernetChannel must be configured in "mode active".
C.
When enabled, the WLC bandwidth drops to 500 Mbps.
D.
To pass client traffic, two or more ports must be configured.
One functional physical port is needed to pass client traffic
Explanation: https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-5/configurationguide/
b_cg75/b_cg75_chapter_0100010.html
Which feature on the Cisco Wireless LAN Controller when enabled restricts management
access from specific networks?
A.
CPU ACL
B.
TACACS
C.
Flex ACL
D.
RADIUS
CPU ACL
Reference: https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wlansecurity/
71978-acl-wlc.html
Refer to the exhibit.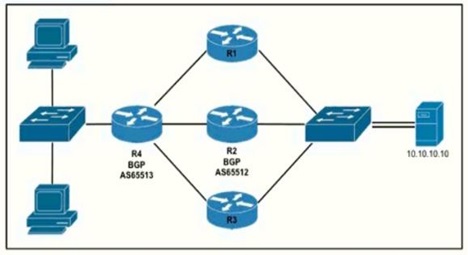
Router R4 is dynamically learning the path to the server. If R4 is connected to R1 via OSPF
Area 20, to R2 v2ia R2 BGP, and to R3 via EIGRP 777, which path is installed in the
routing table of R4?
A.
the path through R1, because the OSPF administrative distance is 110
B.
the path through R2. because the IBGP administrative distance is 200
C.
the path through R2 because the EBGP administrative distance is 20
D.
the path through R3. because the EIGRP administrative distance is lower than OSPF
and BGP
the path through R2 because the EBGP administrative distance is 20
Refer to the exhibit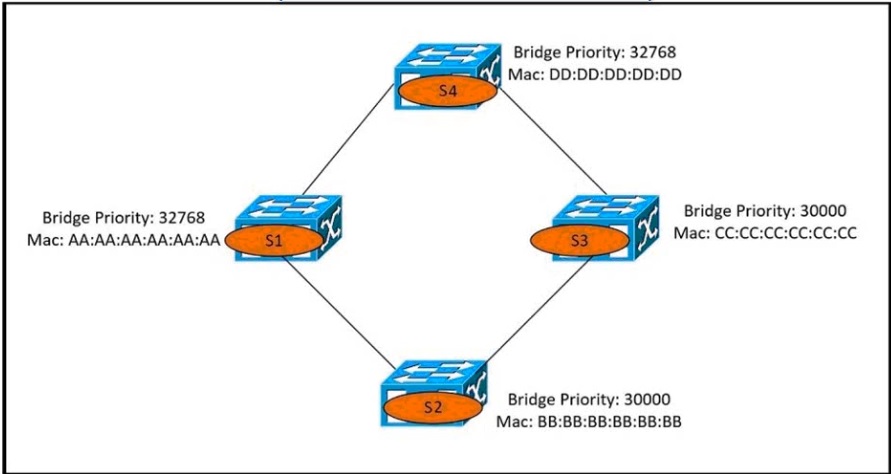
Which switch becomes the root bridge?
A.
S1
B.
S2
C.
S3
D.
S4
S2
What are two functions of a Layer 2 switch? (Choose two)
A.
acts as a central point for association and authentication servers
B.
selects the best route between networks on a WAN
C.
moves packets within a VLAN
D.
moves packets between different VLANs
E.
makes forwarding decisions based on the MAC address of a packet
acts as a central point for association and authentication servers
makes forwarding decisions based on the MAC address of a packet
What are two benefits of controller-based networking compared to traditional networking?
A.
controller-based increases network bandwidth usage, while traditional lightens the load
on the network.
B.
controller-based inflates software costs, while traditional decreases individual licensing
costs
C.
Controller-based reduces network configuration complexity, while traditional increases
the potential for errors
D.
Controller-based provides centralization of key IT functions. While traditional requires
distributes management function
E.
controller-based allows for fewer network failure, while traditional increases failure rates
Controller-based reduces network configuration complexity, while traditional increases
the potential for errors
Controller-based provides centralization of key IT functions. While traditional requires
distributes management function
Explanation:
Cisco DNA Center Device Management
3. Monitor the cloud for software update
5. Uses CLI templates to apply a consistent configuration to multiple devices at an
individual location
6. Uses NetFlow to analyse potential security threats throughout the network and
take appropriate action on that traffic
Traditional device management
2. Manages device configuration on a per-device basis
4. Security is managed near the perimeter of the network with firewalls, VPNs, and
IPS
Implements changes via an SSH terminal
What must be considered when using 802:11 ta?
A.
It is compatible with 802 lib- and 802 11-compliant wireless devices
B.
It is used in place of 802 11b/g when many nonoverlapping channels are required
C.
It is susceptible to interference from 2 4 GHz devices such as microwave ovens.
D.
It is chosen over 802 11b/g when a lower-cost solution is necessary
It is compatible with 802 lib- and 802 11-compliant wireless devices
| Page 3 out of 87 Pages |
| Previous |