Topic 2, Exam B
What is a function of TFTP in network operations?
A.
transfers a backup configuration file from a server to a switch using a username and password
B.
transfers files between file systems on a router
C.
transfers a configuration files from a server to a router on a congested link
D.
transfers IOS images from a server to a router for firmware upgrades
transfers IOS images from a server to a router for firmware upgrades
Explanation: TFTP is mostly used (Firmware upgrade) whereby the admin have the IOS
image on one device and uses TFTP to load the image to all other devices quickly.
Refer to the exhibit.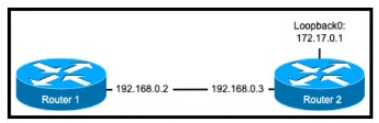
The nip server 192.168.0.3 command has been configured on router 1 to make it an NTP
client of router 2. Which command must be configured on router 2 so that it operates in
server-only mode and relies only on its internal clock?
A.
Router2(config)#ntp passive
B.
Router2(config)#ntp server 172.17.0.1
C.
Router2(config)#ntp master 4
D.
Router2(config)#ntp server 192.168.0.2
Router2(config)#ntp server 172.17.0.1
Explanation: • To use internal clock of this router, use any configured IP address in any
interface of this router.
Refer to the exhibit.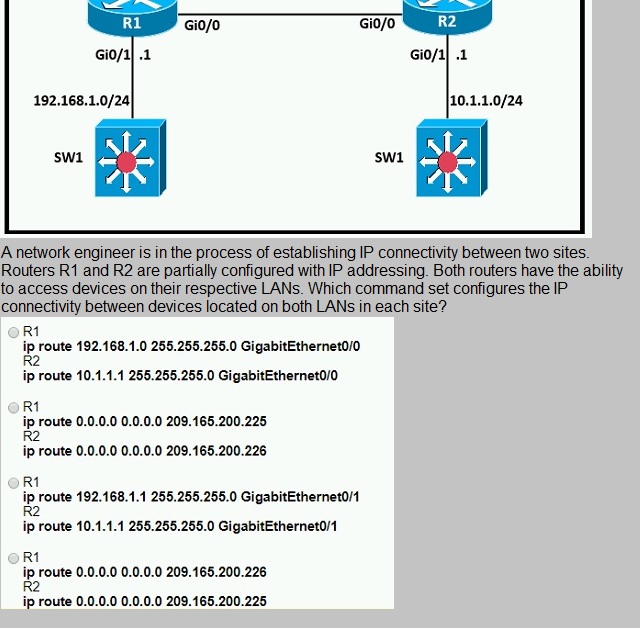
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option D
Which action must be taken to assign a global unicast IPv6 address on an interface that is derived from the MAC address of that interface?
A.
configure a stateful DHCPv6 server on the network
B.
enable SLAAC on an interface
C.
disable the EUI-64 bit process
D.
explicitly assign a link-local address
enable SLAAC on an interface
Refer to me exhibit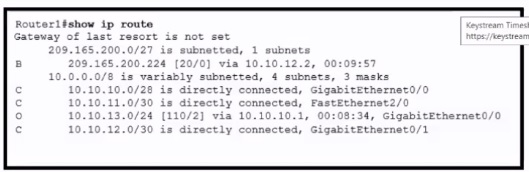
Which action is taken by the router when a packet is sourced from 10.10.10.2 and destined
for 10.10.10.16?
A.
It uses a route that is similar to the destination address
B.
It discards the packets.
C.
It floods packets to all learned next hops.
D.
It Queues the packets waiting for the route to be learned.
It uses a route that is similar to the destination address
Which goal is achieved by the implementation of private IPv4 addressing on a network?
A.
provides an added level of protection against Internet exposure
B.
provides a reduction in size of the forwarding table on network routers
C.
allows communication across the Internet to other private networks
D.
allows servers and workstations to communicate across public network boundaries
provides an added level of protection against Internet exposure
Which QoS tool is used to optimize voice traffic on a network that is primarily intended for data traffic?
A.
FIFO
B.
WFQ
C.
PQ
D.
WRED
PQ
Which result occurs when PortFast is enabled on an interface that is connected to another switch?
A.
Spanning tree may fail to detect a switching loop in the network that causes broadcast storms
B.
VTP is allowed to propagate VLAN configuration information from switch to switch automatically.
C.
Root port choice and spanning tree recalculation are accelerated when a switch link
goes down
D.
After spanning tree converges PortFast shuts down any port that receives BPDUs
Spanning tree may fail to detect a switching loop in the network that causes broadcast storms
Explanation: Enabling the PortFast feature causes a switch or a trunk port to enter the
STP forwarding-state immediately or upon a linkup event, thus bypassing the listening and
learning states.
Note: To enable portfast on a trunk port you need the trunk keyword “spanning-tree portfast
trunk
While examining excessive traffic on the network, it is noted that all incoming packets on an
interface appear to be allowed even though an IPv4 ACL is applied to the interface.
Which two misconfigurations cause this behavior? (Choose two)
A.
The packets fail to match any permit statement
B.
A matching permit statement is too high in the access test
C.
A matching permit statement is too broadly defined
D.
The ACL is empty
E.
A matching deny statement is too high in the access list
A matching permit statement is too high in the access test
A matching permit statement is too broadly defined
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
A.
enable dynamic MAC address learning
B.
implement static MAC addressing.
C.
enable sticky MAC addressing
D.
implement auto MAC address learning
enable sticky MAC addressing
| Page 28 out of 87 Pages |
| Previous |