Topic 1: Exam Pool A
desc about topic
Which mode allows access points to be managed by Cisco Wireless LAN Controllers?
A.
autonomous
B.
lightweight
C.
bridge
D.
mobility express
lightweight
Explanation: https://www.cisco.com/c/en/us/support/docs/wireless/aironet-1200-
series/70278-lap-faq.html
A Lightweight Access Point (LAP) is an AP that is designed to be connected to a wireless
LAN (WLAN) controller (WLC). APs are “lightweight,” which means that they cannot act
independently of a wireless LAN controller (WLC). The WLC manages the AP
configurations and firmware. The APs are “zero touch” deployed, and individual
configuration of APs is not necessary.
What is the purpose of a southbound API in a control based networking architecture?
A.
Facilities communication between the controller and the applications
B.
Facilities communication between the controller and the networking hardware
C.
allows application developers to interact with the network
D.
integrates a controller with other automation and orchestration tools.
Facilities communication between the controller and the networking hardware
Explanation:
https://www.ciscopress.com/articles/article.asp?p=2995354&seqNum=2#:~:text=The-S
outhbound-Interface,communicate-to-the-networking-devices.&text=The
-overall-goal-is-network,from-being-only-a-protocol.
The Southbound Interface
In a controller-based network architecture, the controller needs to communicate to the
networking devices.
Refer to the exhibit.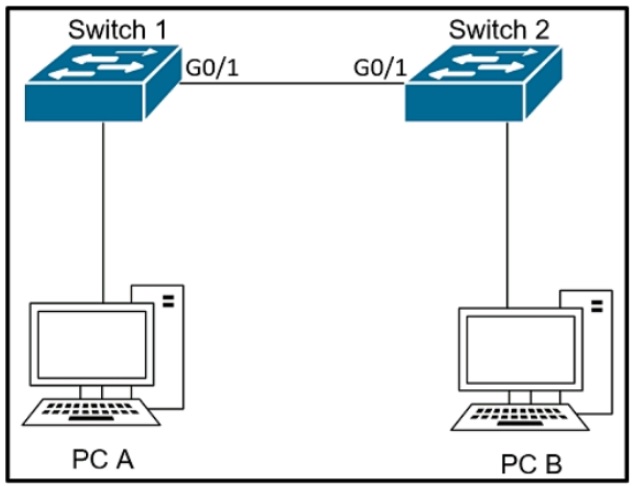
The network administrator wants VLAN 67 traffic to be untagged between Switch 1 and
Switch 2 while all other VLANs are to remain tagged.
Which command accomplishes this task?
A.
switchport access vlan 67
B.
switchport trunk allowed vlan 67
C.
switchport private-vlan association host 67
D.
switchport trunk native vlan 67
switchport trunk native vlan 67
Refer to the exhibit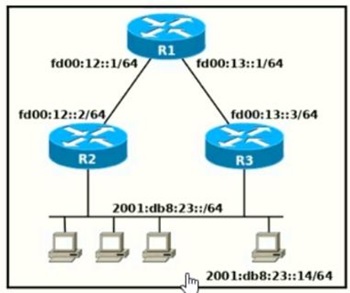
Which two commands, when configured on router R1, fulfill these requirements? (Choose two.)
Packets towards the entire network 2001:db8:2::/64 must be forwarded through router R2.
Packets toward host 2001:db8:23::14 preferably must be forwarded through R3.
A.
Ipv6 route 2001:db8:23::/128 fd00:12::2
B.
Ipv6 route 2001:db8:23::14/128 fd00:13::3
C.
Ipv6 route 2001:db8:23::14/64 fd00:12::2
D.
Ipv6 route 2001:db8:23::/64 fd00:12::2
E.
Ipv6 route 2001:db8:23::14/64 fd00:12::2 200
Ipv6 route 2001:db8:23::/64 fd00:12::2
Ipv6 route 2001:db8:23::14/64 fd00:12::2 200
What are two fundamentals of virtualization? (choose two)
A.
The environment must be configured with one hypervisor that serves solely as a network
manager to monitor SNMP traffic
B.
It allows logical network devices to move traffic between virtual machines and the rest of
the physical network
C.
It allows multiple operating systems and applications to run independently on one
physical server.
D.
It allows a physical router to directly connect NICs from each virtual machine into the
network
E. It requires that some servers, virtual machines and network gear reside on the Internet
It allows logical network devices to move traffic between virtual machines and the rest of
the physical network
It allows multiple operating systems and applications to run independently on one
physical server.
How do servers connect to the network in a virtual environment?
A.
wireless to an access point that is physically connected to the network
B.
a cable connected to a physical switch on the network
C.
a virtual switch that links to an access point that is physically connected to the network
D.
a software switch on a hypervisor that is physically connected to the network
a software switch on a hypervisor that is physically connected to the network
Which 802.11 management frame type is sent when a client roams between access points
on the same SSID?
A.
Reassociation Request
B.
Probe Request
C.
Authentication Request
D.
Association Request
Reassociation Request
What is a role of wireless controllers in an enterprise network?
A.
centralize the management of access points in an enterprise network
B.
support standalone or controller-based architectures
C.
serve as the first line of defense in an enterprise network
D.
provide secure user logins to devices on the network.
centralize the management of access points in an enterprise network
Which two protocols are supported on service-port interfaces? (Choose two.)
A.
RADIUS
B.
TACACS+
C.
SCP
D.
Telnet
E.
SSH
Telnet
SSH
Explanation: https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-5/configurationguide/
b_cg75/b_cg75_chapter_011110.html
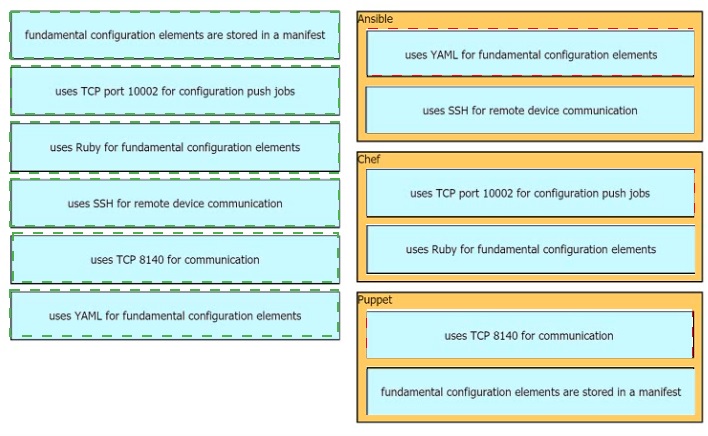
Drag drop the descriptions from the left onto the correct configuration-management technologies on the right.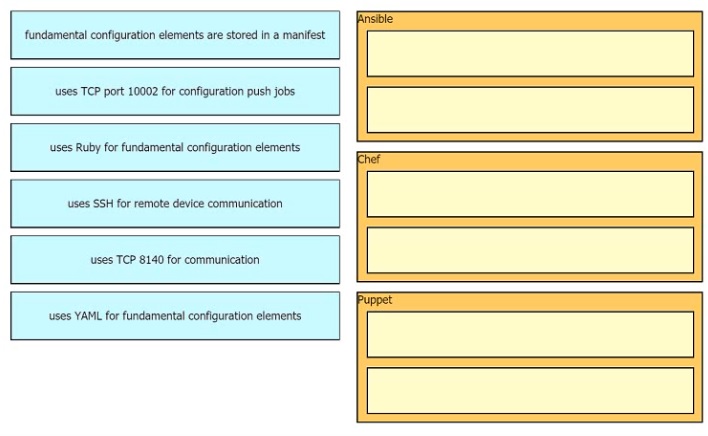
| Page 23 out of 87 Pages |
| Previous |