An investigator is examining a copy of an ISO file that is stored in CDFS format.
What type of evidence is this file?
A.
data from a CD copied using Mac-based system
B.
data from a CD copied using Linux system
C.
data from a DVD copied using Windows system
D.
data from a CD copied using Windows
data from a CD copied using Linux system
Which type of evidence supports a theory or an assumption that results from initial
evidence?
A.
probabilistic
B.
indirect
C.
best
D.
corroborative
corroborative
Refer to the exhibit.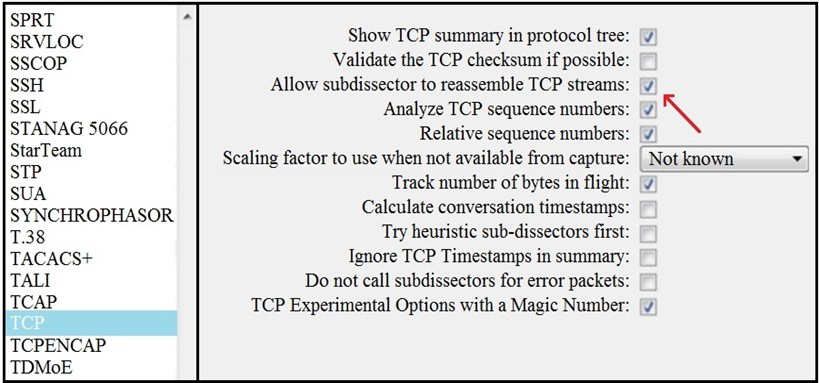 What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
A.
insert TCP subdissectors
B.
extract a file from a packet capture
C.
disable TCP streams
D.
unfragment TCP
unfragment TCP
Refer to the exhibit.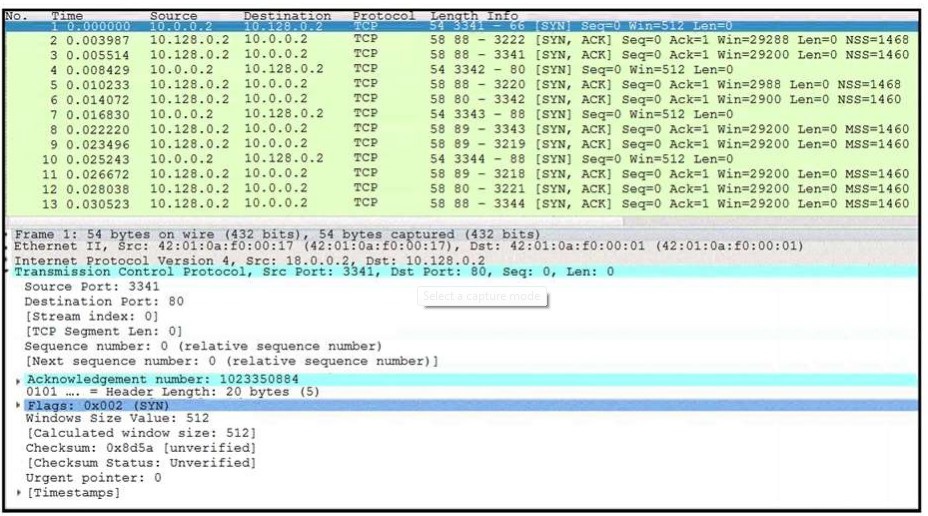 What is occurring in this network traffic?
What is occurring in this network traffic?
A.
high rate of SYN packets being sent from a multiple source towards a single destination IP
B.
high rate of SYN packets being sent from a single source IP towards multiple destination IPs
C.
flood of ACK packets coming from a single source IP to multiple destination IPs
D.
flood of SYN packets coming from a single source IP to a single destination IP
flood of SYN packets coming from a single source IP to a single destination IP
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
A.
confidentiality, identity, and authorization
B.
confidentiality, integrity, and authorization
C.
confidentiality, identity, and availability
D.
confidentiality, integrity, and availability
confidentiality, integrity, and availability
Which HTTP header field is used in forensics to identify the type of browser used?
A.
referrer
B.
host
C.
user-agent
D.
accept-language
user-agent
What does an attacker use to determine which network ports are listening on a potential target device?
A.
man-in-the-middle
B.
port scanning
C.
SQL injection
D.
ping sweep
port scanning
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group.
What is the initial event called in the NIST SP800-61?
A.
online assault
B.
precursor
C.
trigger
D.
instigator
precursor
Which artifact is used to uniquely identify a detected file?
A.
file timestamp
B.
file extension
C.
file size
D.
file hash
file hash
Refer to the exhibit. What is occurring in this network?
What is occurring in this network?
A.
ARP cache poisoning
B.
DNS cache poisoning
C.
MAC address table overflow
D.
MAC flooding attack
ARP cache poisoning
| Page 6 out of 19 Pages |
| Previous |