Refer to the exhibit.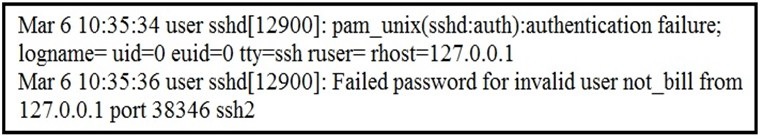
In which Linux log file is this output found?
A.
/var/log/authorization.log
B.
/var/log/dmesg
C.
var/log/var.log
D.
/var/log/auth.log
/var/log/auth.log
Which two components reduce the attack surface on an endpoint? (Choose two.)
A.
secure boot
B.
load balancing
C.
increased audit log levels
D.
restricting USB ports
E.
full packet captures at the endpoint
secure boot
restricting USB ports
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
A.
queries Linux devices that have Microsoft Services for Linux installed
B.
deploys Windows Operating Systems in an automated fashion
C.
is an efficient tool for working with Active Directory
D.
has a Common Information Model, which describes installed hardware and software
has a Common Information Model, which describes installed hardware and software
An analyst is investigating an incident in a SOC environment.
Which method is used to identify a session from a group of logs?
A.
sequence numbers
B.
IP identifier
C.
5-tuple
D.
timestamps
5-tuple
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A.
Untampered images are used in the security investigation process
B.
Tampered images are used in the security investigation process
C.
The image is tampered if the stored hash and the computed hash match
D.
Tampered images are used in the incident recovery process
E.
The image is untampered if the stored hash and the computed hash match
Tampered images are used in the security investigation process
The image is untampered if the stored hash and the computed hash match
Refer to the exhibit.

Which type of log is displayed?
A.
proxy
B.
NetFlow
C.
IDS
D.
sys
NetFlow
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions.
Which identifier tracks an active program?
A.
application identification number
B.
process identification number
C.
runtime identification number
D.
process identification number
process identification number
Which metric is used to capture the level of access needed to launch a successful attack?
A.
privileges required
B.
user interaction
C.
attack complexity
D.
attack vector
privileges required
Which IETF standard technology is useful to detect and analyze a potential security incident by recording
session flows that occurs between hosts?
A.
SFlow
B.
NetFlow
C.
NFlow
D.
IPFIX
IPFIX
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
A.
MAC is controlled by the discretion of the owner and DAC is controlled by an
administrator
B.
MAC is the strictest of all levels of control and DAC is object-based access
C.
DAC is controlled by the operating system and MAC is controlled by an administrator
D.
DAC is the strictest of all levels of control and MAC is object-based access
MAC is the strictest of all levels of control and DAC is object-based access
| Page 3 out of 19 Pages |
| Previous |