A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
A.
the intellectual property that was stolen
B.
the defense contractor who stored the intellectual property
C.
the method used to conduct the attack
D.
the foreign government that conducted the attack
the foreign government that conducted the attack
A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
A.
the intellectual property that was stolen
B.
the defense contractor who stored the intellectual property
C.
the method used to conduct the attack
D.
the foreign government that conducted the attack
the foreign government that conducted the attack
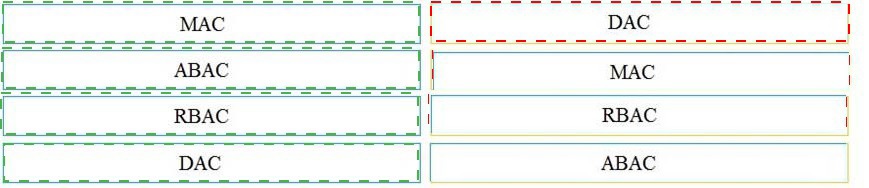
Drag and drop the access control models from the left onto the correct descriptions on the right.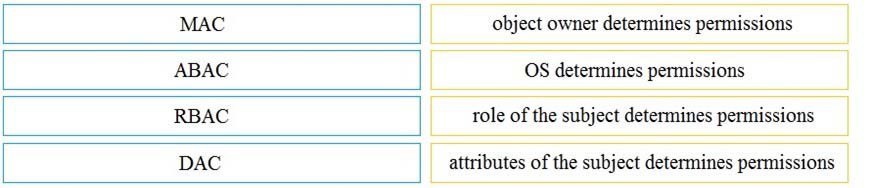
Which security principle requires more than one person is required to perform a critical task?
A.
least privilege
B.
need to know
C.
separation of duties
D.
due diligence
separation of duties
Which incidence response step includes identifying all hosts affected by an attack'?
A.
post-incident activity
B.
detection and analysis
C.
containment eradication and recovery
D.
preparation
post-incident activity
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
A.
file type
B.
file size
C.
file name
D.
file hash value
file hash value
What is the difference between deep packet inspection and stateful inspection?
A.
Deep packet inspection is more secure than stateful inspection on Layer 4
B.
Stateful inspection verifies contents at Layer 4 and deep packet inspection verifies connection at Layer 7
C.
Stateful inspection is more secure than deep packet inspection on Layer 7
D.
Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4
Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4
Refer to the exhibit.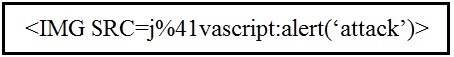
Which kind of attack method is depicted in this string?
A.
cross-site scripting
B.
man-in-the-middle
C.
SQL injection
D.
denial of service
cross-site scripting
How is NetFlow different than traffic mirroring?
A.
ANetFlocollects metadata and traffic mirroring clones data
B.
Traffic mirroring impacts switch performance and NetFlow does not
C.
Traffic mirroring costs less to operate than NetFlow
D.
NetFlow generates more data than traffic mirroring
ANetFlocollects metadata and traffic mirroring clones data
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
A.
syslog messages
B.
full packet capture
C.
NetFlow
D.
firewall event logs
NetFlow
| Page 2 out of 19 Pages |
| Previous |